Predictability and Resilience in Embedded Networks
An Approach to Enhance the Timeliness of Wireless Communications
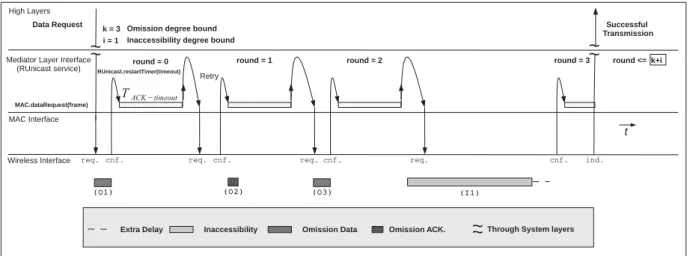
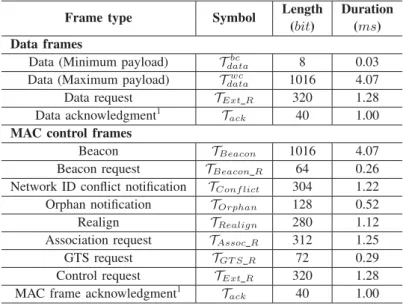
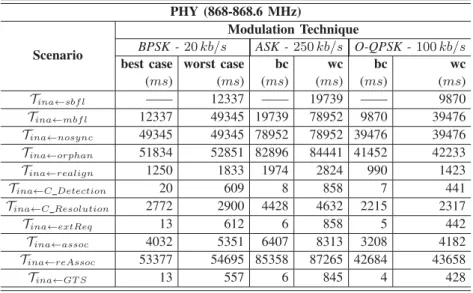
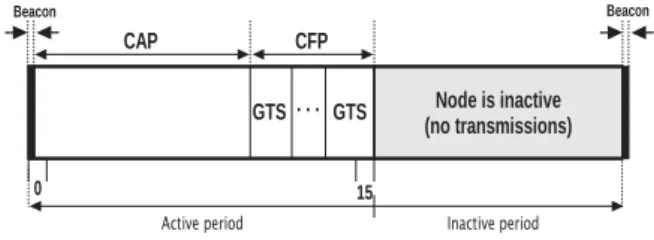
Traditionally, a MAC frame transmission service is unaware of the occurrence of periods of inaccessibility during network operation. Future directions include: shortening the duration of inaccessibility scenarios based on mechanisms present in the IEEE 802.15.4 standard; improvement of support to periodic.
Characterization of Network Inaccessibility in IEEE 802.15.4 Wireless Networks . 13
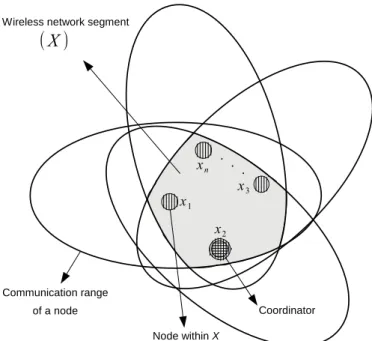
These periods of network inaccessibility are considered global by all nodes of the wireless network segment. Defining methods and reducing the duration of periods of network inaccessibility in the IEEE 802.15.4 wireless network is critical to achieving real-time operation.
Reducing Inaccessibility in IEEE 802.15.4 Wireless Communications
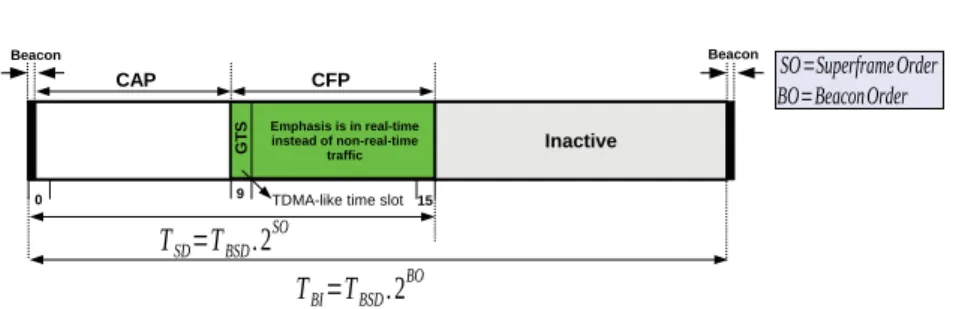
To present our progress, the paper is organized as follows: Section 2 presents an overview of the IEEE 802.15.4 standard. The (real) value of TBI is also used to normalize the duration of the network, the duration of network inaccessibility events, as in Fig.
Self‐Stabilizing TDMA algorithms for Dynamic Wireless Ad‐hoc Networks
The proposed algorithm facilitates the implementation of both of the above approaches (see Section 7 for more details). After showing that the MAC algorithm in Figure 2 is self-stabilizing with respect to the τTDMA task. sections 10 to 9 of the appendix), we consider the time required for convergence within an individual neighborhood (section 5) and the entire neighborhood (section 6). Furthermore, when we consider the convergence time of the network, i.e. the expected convergence time of all nodes in the network, we see that the most dominant parameter is the average neighborhood size.
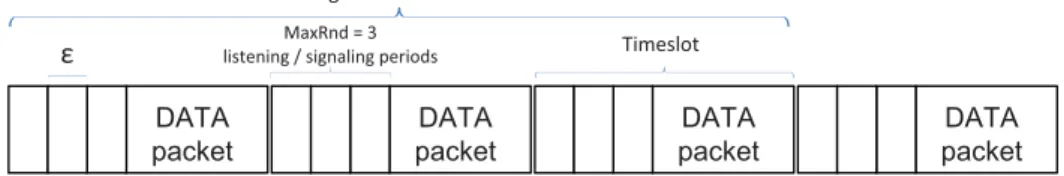
We achieve this by studying the influence of parameters T andn on the MAC algorithm in Fig. Assume that n≥2 is the number of listening/alarming periods, see line 2 of the code in Fig. When Nodes try to access the medium, the conversation time, S (cf. contour lines), is stable in the presence of an increasing number, n, of listening/signaling periods.
Thus, analyzing the expected time of planner-luck games [16, 18], we have a limited value. This sequential selection of the listening/signaling period leads to a uniform selection of a listening/signaling neighbor.
Autonomous TDMA alignment for VANETs
Abstract—We study the local clock synchronization problem in the context of media access control (MAC) protocols, such as time division multiple access (TDMA), for dynamic and wireless ad hoc networks. Task definition The problem of (decentralized) local synchronization of pulses takes into account the rapid reduction of all local synchronous limits ψ ≥ max({Λi,j(k, q) ∶ pi, pj ∈ N∧pj ∈ NTi ∧Δi,j(k, q) = 0 }), where NiT refers to the recent neighbors of pi, see the figure. In addition, headγi= (ti−tpr)modP and tailγi= (tsu−ti)modP are the phase difference between the phase value pi, ti and predecessors= ppr, respectively. , successori = psu.
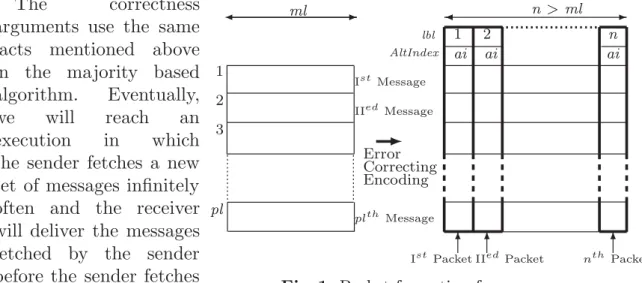
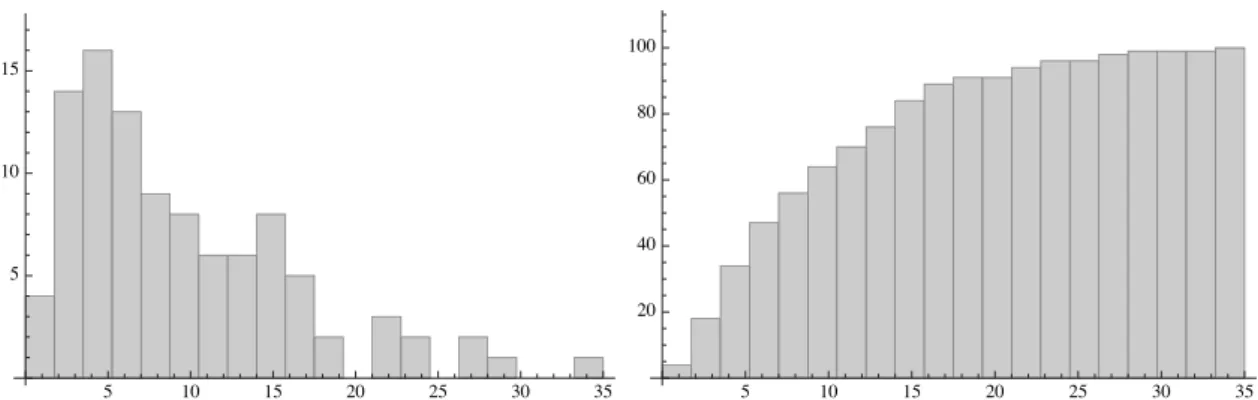
Local dominant pulses Let's look at a typical convergence of the cricket strategy, see Fig. Given two nodes, pi, pj ∈N, and pi's locally observed pulse profile, γi(t), we say that pj's pulse (phase value) locally dominates the one of pi, ifheadγi Single-hop Ad Hoc Network Both algorithms reduce the synchrony binding to 1% of the time slot size, see Fig. Furthermore, the synchrony limits of the cricket and grasshopper are 24%, and 62% lower, respectively, when using pre-allocated TDMA rather than Chameleon-MAC [8]. Packets are exchanged by the sender and the receiver to deliver (high level) messages in a reliable manner. The sender waits for an acknowledgment of packet arrival for each of the (2 · capacity + 1) different labels, and an indication that the receiver has delivered a message due to the arrival of (capacity + 1) packets with alternating index 0. the sender collects the incoming packet into a sequence of (2 capacity + 1) inputs and waits to receive a packet for each input, and to have a value of ldai equal to the alternating index the sender is currently using in the transmitted packets in at least (capacity + 1) of the contained packets. When the receiver accumulates separate label packets, the capacity of the packets may be incorrect. In this case, the sender repeatedly sends n separate packets and the receiver keeps sending (capacity + 1) packets, each with a distinct label in the range 1 to (capacity + 1). Throughout, we refer to R as an implementation of the Sender and the Receiver algorithms, where ps. We show that, between asα and asα+1, the receiver pr sends at least one of the packets ackα( ) ∈ ACKα that ps receives. Between asα and asα+1, the receiver makes exactly one step arβ, and between arβ and arβ+1, the sender makes exactly one step asα+1. For example, we see that about 80% of the sample values are equal to or less than 15. As the number of sample values approaches infinity, the sample statistics converge to the true population values. The kthorder statistic for the uniform distribution can be described by a Beta(α, β) distribution with parameters α = k and β = n + 1 − k. This should give us the rank of the sample value corresponding to the target coverage C. It also adjusts for a zero-based indexing of the sample array, for added clarity of implementation. The maximum sample size should be chosen according to the limitations of the hardware and the dynamics of the environment. This sliding window can be implemented as circular buffer, with an array for the sample values, a pointer to the beginning of the window and a fill counter. In this section, we measure an adaptation process, which uses the proposed bound estimation algorithm, to determine the empirical effectiveness of the non-parametric method. The second aspect is related to the assessment of the quality of measurements of individual sensors during operation. The behavior of the fusion process can be controlled by FC requests or triggered in case of new input data. A basic virtual sensor (BVS) combines several SVS of the same type and provides greater reliability. Additionally, Virtual Sensor applications are limited to a hierarchical depth of three nodes, as defined by the three subclasses. The standardization of the various interfaces is mapped to an Interface File System (IFS) typically in the memory of each Smart Transducer. Based on these requirements, we developed our framework for processing fault-tolerant sensor data in dynamic environments (MOSAIC) that defines a suitable software abstraction - "Smart Abstract Entity". This feedback provides redundant information and enables effective validation of the current measurement. In Proceedings of the 19th IEEE International Conference on Distributed Computing Systems Middleware Workshop, pp. The frontline fault tolerance community deals with failures of the computer and communications system, i.e. This allows the preparation of data sets that are compatible with the formats of the subsequent processing chain. The second step quantifies the effect of the node-specific errors collected in the previous step. If the error level reaches the range of the sensor (1), we set the error amplitude index value to 10. II structures the error types for the sensor type [28] and their parameters for error amplitude (Fn) and for occurrence probability ( On). An indication of the low validity of the raw sensor system is the derived maximum RPN of 720. The system validity, represented by the RPN, is a confirmation of the reliability of the event validity. Implementation of the multi-level fault detection for an IR remote sensor using MOSAIC - Diagram (adapted from [26]). In particular, we assume that the identity of the sending node is known to the receiver. We also note that, since we assume that the nodes of the system are a subset of P. Once the receiver delivers a message to the network layer, the receiver starts to repeatedly send acknowledgments with the label of the delivered message over 2f+ 1vertex disjoint paths. If not, pi forwards the message to the next node on the intended path of the message, not forgetting to update the visited path. However, if pi is the destination of the message, pi checks the message type in line 10. If the message type is Datathen (in line 11), pi adds the message's payload and label to the part of the data structure associated with the message hears source, i.e. the sender, and the path the message visited. All nodes that appear in the message, ie. in the first, second or third entry of the tuple, are inN. This is correct since each asynchronous round pr sends a new frame containing an Ack on each of the 2f + 1 node disjoint paths. Due to capture effects, neighboring nodes correctly receive one of the simultaneously sent packets with high probability. By repeating this process, the network converges to a stable state where all nodes have received the same data (consensus). Upon completion, all nodes are likely to have received the same data as the basis for activation. CaptureCom takes advantage of spatial diversity in low-energy wireless networks: sequential, simultaneous transmissions distributed across the network enable data distribution with very low delays and high energy efficiency. For example, the capture effect has been used for fast flooding in sensor networks: nodes simultaneously forward received packets to spread them quickly in the network [5]. To introduce the basic design of CaptureCom and demonstrate its benefits, we use a sample application whose purpose is to determine the maximum sensor reading among all nodes in the network (eg occupancy or temperature) and propagate this maximum to all nodes. Ultimately, all nodes are aware of the maximum temperature reading in the network and can trigger activation. On reception, a node merges its local bitfield with the received one via a bitwise OR and determines the maximum of the local and the received data (see Fig.
Self‐Stabilizing End‐to‐End Communication in Bounded Capacity, Omitting,
Adaptive Middleware for Advanced Control Systems
Lightweight Dependable Adaptation for Wireless Sensor Networks
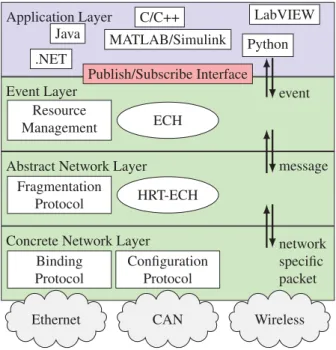
Programming abstractions and middleware for building control systems as
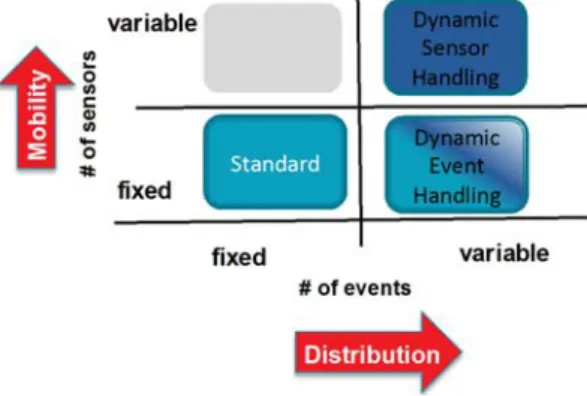
A fault‐aware sensor architecture for cooperative mobile applications
Reliable Assessment of Global State
Self‐Stabilizing Byzantine Resilient Topology Discovery and Message Delivery

Capture effect based communication primitives