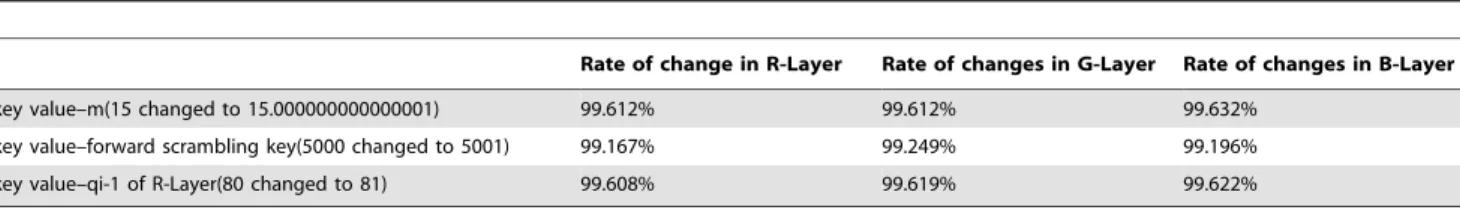
An image encryption algorithm utilizing julia sets and hilbert curves.
Texto
Imagem


Documentos relacionados
The position of the data is scrambled in the order of randomness of the elements obtained from the chaotic map and again rearranged back to their original position in
Figure 14 (b) -(d) shows the Lena image encrypted by our proposed algorithm, the FT-based algorithm and the FRT-based algorithm; after 70% of pixels were cropped, the
In this paper we have used capabilities and features of hyper chaos functions such as sensitivity to initial values, random behavior, non-periodic and certainty
Cryptography or sometimes referred to as encipherment is used to convert the plaintext to encode or make unreadable form of text [1]. The sensitive data are
The entropy of the watermarked image and correlation coefficient of extracted watermark image is very close to ideal values, proving the correctness of proposed
For lossy compression based on RLE algorithm and its modifications I2BN and I3BN, Zip algorithms, Rar and Huffman algorithm used two-threshold progressive image
The algorithm encryption and decryption of an image transform an image into cipher code using the random keys, which allow users to have confidentiality and security in
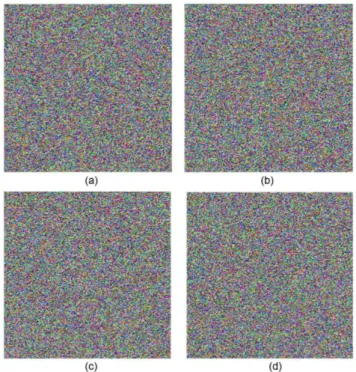
An attacker can examine the histogram of an encrypted image (red, green and blue) using the algorithms of attack and the statistical analysis of the encrypted image