Identification of Closest and Phantom Nodes in Mobile Ad Hoc Networks
Texto
Imagem
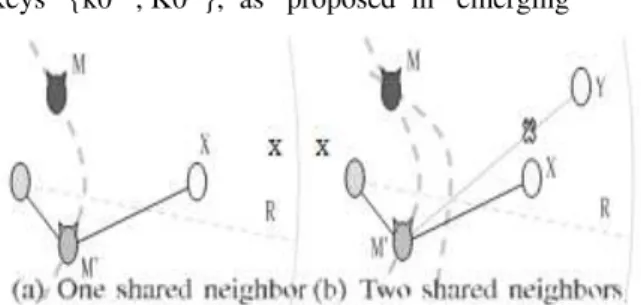

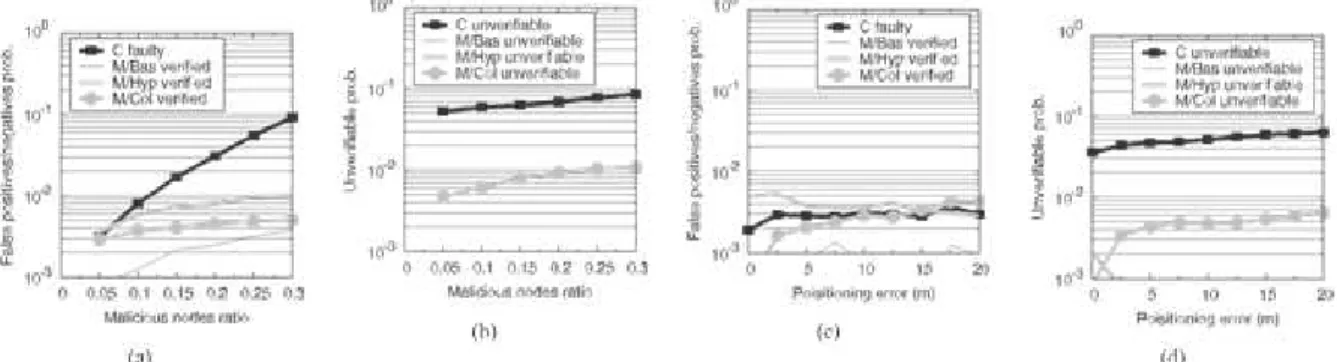
Documentos relacionados
The iterative methods: Jacobi, Gauss-Seidel and SOR methods were incorporated into the acceleration scheme (Chebyshev extrapolation, Residual smoothing, Accelerated
The survey explored the characteristics of mobile devices being used in the form of hardware technology, software and communication systems, achievements made and
The broad objective of the study is to analyze male and female access to land for cassava production in Abia state and specifically to describe the
Ainsi, au cours du siècle, l’on peut déceler la présence de communautés et groupes de «portugais» qui vivaient en marge des circuits officiel de l’Estado
quando num dado momento, um estabelecimento de turismo de saúde e bem-estar define a composição do produto turístico que coloca no mercado, deve ter em conta quais são
social assistance. The protection of jobs within some enterprises, cooperatives, forms of economical associations, constitute an efficient social policy, totally different from
Routing is the critical issue in the MANET and focus based on routing protocols such as Ad hoc On-demand Distance Routing Protocol (AODV), Dynamic Source Routing (DSR),
Abstract: As in ancient architecture of Greece and Rome there was an interconnection between picturesque and monumental forms of arts, in antique period in the architecture