International Journal of Electronics and Computer Science Engineering 239
Available Online at www.ijecse.org ISSN: 2277-1956
ISSN-2277-1956/V1N2-239-242
Performance evaluation of DSR Protocol under
DoS attack
Ms. Trupti Patel 1, Ms. Ch.Shyamala Rani 2, Mrs. Hina Patel 3
1,3Electronics and Communication Dept. PIET, Limda, Baroda, Gujarat, India 2
Computers Science & Engg Dept. BMCET, Surat, Gujarat, India
Email-1 Pateltrupti15@gmail.com, 2rani.shyamala@gmail.com, 3heena_ldce@yahoo.co.in
Abstract- A mobile ad-hoc network (MANET) consists of mobile hosts equipped with wireless communication devices. A Mobile Ad hoc Network is a self-organizing, infrastructure less, multi-hop network. The transmission of a mobile host is received by all hosts within its transmission range due to the broadcast nature of wireless communication and unidirectional antenna. If two wireless hosts are out of their transmission ranges in the ad hoc networks, other mobile hosts located between them can forward their message, which effectively builds connected networks among the mobile hosts in the deployed area. One main challenge in design of these networks is their vulnerable nature to security attack. These attacks can be deployed by insider or outsider attacker. Sometime, the node from network can be attacker. This is happen because of mobility of nodes and changing network topology. There are different kind of attacks available in literature and can be implemented on MANET. One of these attacks is Grey Hole attack that has dangerous effect on Mobile Ad-Hoc Network. In this paper, we study the effect of Grey Hole attack on Dynamic Source Routing (DSR) protocol in Mobile Ad-Hoc Network.
Keywords—Ad-Hoc Networks, Grey Hole attack, DSR, CBR Traffic
I-INTRODUCTION
In recent years, the explosive growth of mobile computing devices, which mainly include laptops, personal digital assistants (PDAs) and handheld digital devices, has impelled a revolutionary change in the computing world: computing will not merely rely on the capability provided by the personal computers, and the concept of ubiquitous computing emerges and becomes one of the research hotspots in the computer science society [1].
The nature of the ubiquitous computing has made it necessary to adopt wireless network as the interconnection method: it is not possible for the ubiquitous devices to get wired network link whenever and wherever they need to connect with other ubiquitous devices. The Mobile Ad Hoc Network is one of the wireless networks that have attracted most concentrations from many researchers.
A Mobile Ad hoc Network (MANET) is a system of wireless mobile nodes that dynamically self-organize in arbitrary and temporary network topologies. People and vehicles can thus be internetworked in areas without a preexisting communication infrastructure or when the use of such infrastructure requires wireless extension [2]. Because of this features, the mobile ad hoc networks are more prone to suffer from the malicious behaviors than the traditional wired networks. Therefore, we need to pay more attention to the security issues in the mobile ad hoc networks.
In this paper, Aim is to evaluate the performance of dynamic source routing protocol under DoS attack.
In section 2, we explore DSR protocol. Section 3 define and explain DoS attack. Section 4 say problem statement and analyze the performance of DSR through simulation result. Section 5 concludes the paper. Section 6 specifies the future work.
II-DSR PROTOCOL OPERATION
IJECSE,Volume1,Number 2
Trupti Patel et al.ISSN-2277-1956/V1N2-239-242
node. Advantage of on demand routing is that it saves bandwidth by reducing routing overhead. Disadvantage is the latency at the beginning of transmission to nodes when no route, have yet been discovered.
Dynamic Source Routing (DSR)[3] is specifically designed for use in multi-hop wireless ad hoc networks. The protocol does not require any existing infrastructure or administration and is completely self-organizing and self configuring. DSR is source routing protocol, which means the entire route is known before transmission is begun. DSR stores discovered routes in Route Cache. The protocol basically consists of the two mechanisms:
Route Discovery
Route Maintenance
A-Route Discovery
When source node sends a packet to the destination node, it first searches its route cache for suitable route to destination. If no route from source to destination exists in source’s route cache, Source initiates Route Discovery and sends out a ROUTE REQUEST message to find the route. The source node is referred to as initiator and destination node as the target. When a node receives a ROUTE REQUEST message it examines the target ID to determine if it is the target of message. If not, then nodes own id is appended to the address list and the RReq is broadcasted. If the node is the target it returns a ROUTE REPLY message to the initiator. This ROUTE REPLY message includes the accumulated route from the ROUTE REQUEST message.
B-Route Maintenance
Since nodes move in and out of transmission range of other nodes and thereby creates and breaks routes, it is necessary to maintain the routes that are stored in the route cache. When a node receives a packet it is responsible for confirming that the packet reaches the next node on the route. Figure illustrates the mechanism work like a chain where each link has to make sure that the link in front of it not broken.
III-DENIAL OF SERVICE ATTACK - GREY HOLE
A DoS attack is distributed in nature, large scale attempt by malicious users to disrupt connection between two machines, thereby preventing access to a service or to disrupt service to a specific system.[4] This exhausts the victim network of resources such as bandwidth, battery, computing power, etc. The victims are unable to provide services to its legitimate clients and network performance is greatly deteriorated.
One of the most important attacks of DoS category is grey hole attack. We need to find the effect of this attack on DSR.
In this case, the attacker introduce itself as co-operating node, it participate in route request and route reply mechanism, it make sure that it will be available on the path. After the route discovery mechanism, when source node transmit data packet at that time malicious user just drop all the data packet. In other words, such attacker does not allow that all of packets arrive at real destination [4].
IV-PROBLEM STATEMENT
In DSR, Route Request and Route Reply messages are used for finding the path between source and destination. Source initiates Route Discovery and sends out a ROUTE REQUEST message to find the route. When a node receives a ROUTE REQUEST message it examines the target ID to determine if it is the target of message. If the node is the target it returns a ROUTE REPLY message to the initiator. This ROUTE REPLY message includes the accumulated route from the ROUTE REQUEST message.
In Grey Hole Attack, Attacker participates in route discovery procedure and it will make sure that it will be available on the path. In this kind of attack, attackers do not drop the entire packet but only drop certain kind of packet such as data packet. With this half dropping the attacker tries to hide the attack by not denying all the network service.
241
Performance evaluation of DSR Protocol under DoS attack
ISSN-2277-1956/V1N2-239-242
TABLE I-PARAMETERS USED IN NS-2 SIMULATOR
Simulation time 500 sec Number of Nodes 50 Routing Protocol DSR
Traffic CBR
Packet Size 512 Bytes Number of traces 10
Topologies Dynamic
Mobility Model Random Way Point For the evaluation we use following metrics in our study:
1-Packet Delivery Ratio: The packet delivery ratio of a receiver is defined as the ratio of the number of data packets received by receiver over the number of data packets transmitted by the sender.
2-Throughput: Network throughput refers to the average data rate of successful data or message delivery over a specific communications link.
3-End to End Delay: The end to end delay of a packet is defined as the time a packet takes to travel from the source to destination.
V-SIMULATION RESULTS
Following are our simulation results that demonstrate the effects of grey hole attack on DSR protocol in Mobile Ad-Hoc Networks.
Table II-PACKET DELIVERY RATIO
2 Nodes
4 Nodes
6 Nodes
8 Nodes
10 Nodes
88.99% 85.62% 83.82% 78.67% 77.30%
Figure 1 Packet Delivery Ratio under grey hole attack
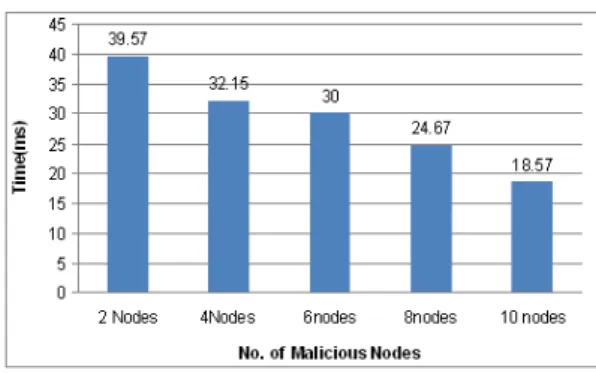
TABLE IIII- END TO END DELAY
2 Nodes 4 Nodes 6 Nodes 8 Nodes 10
Nodes
IJECSE,Volume1,Number 2
Trupti Patel et al.ISSN-2277-1956/V1N2-239-242 Figure 2 End-to-End Delay under grey hole attack
TABLE IIIV- THROUGHPUT
2 Nodes 4 Nodes 6 Nodes 8 Nodes 10
Nodes
245.092 235.764 230.86 216.348 213.092
Figure 3 Throughput under grey hole attack
VI-CONCLUSIONS
The performance of routing protocols in MANET depends heavily on much kind of attacks. One of these attacks is grey hole attack. The results of simulation show that this attack has high effect on DSR protocol.
In this case, based on the number of attacker, the Packet Delivery Ratio is high or low. If the number of them increases, the Packet Delivery Ratio is low, because we have grey hole attack.
End to End Delay is not more different between two states (attack or no attack), because the topology is dynamic and the figured structure in first state is change in next times and finally Throughput for other nodes is high.
With this results, must consider defense mechanism for MANET protocols under various attacks. This aim is most important for future these types of networks.
REFERENCES
[1] Marco Conti, Body, ”Personal and Local Ad Hoc Wireless Networks”, in Book The Handbook of Ad Hoc Wireless Networks (Chapter 1), CRC Press LLC, 2003.
[2] M.S. Corson, J.P. Maker, and J.H. Cernicione, ”Internet-based Mobile Ad Hoc Networking”, IEEE Internet Computing, pages 63-70, July-August 1999.
[3] David B. Johnson, David A. Maltz, Josh Broch, ”Dynamic Source Routing Protocol for Multihop WIreless Ad Hoc etworks”, Ad Hoc Networking (Chapter 5), pages 139-172, 2010.