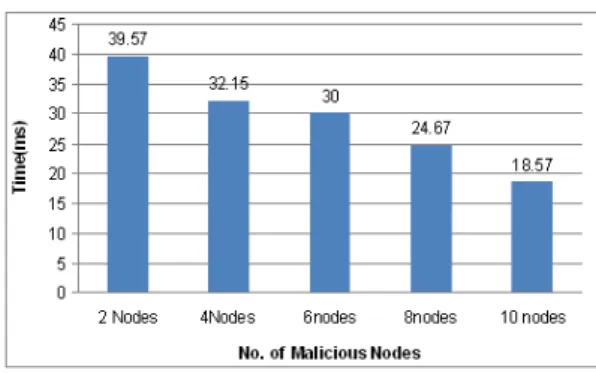
Performance evaluation of DSR Protocol under DoS attack
Texto
Imagem

Documentos relacionados
For comparing various routing protocols using UDP transport layer protocol, we have chosen three performance metrics Average End to End delay, Packet Delivery Ratio,
In this paper, simulation based study of the impact of neighbor attack and black hole attack on AOMDV routing protocol by calculating the performance metrics such as packet
The protocol performance evaluation for an ad-hoc network is necessary to be tested under realistic conditions, especially including the movement of the mobile nodes which
ADMR consists of 3 phases are Multicast State Setup, Multicast Packet Forwarding, Multicast State Maintenance .Like other tree based multicast routing protocols, it builds a
Source peer s, once gathering swarm agent RCSA, updates the secretion table with the pheromone indicator value g ni of every relay hope peer ni which
Topology Based routing approach has Route instability, this is because an established route consists of a set of nodes between the source and the destination that are affected
The proposed algorithm is used to prevent Co-operative Black hole attack in Manet using DSR protocol and also improve the performance in terms of throughput and delay.. The rest of
Routing is the critical issue in the MANET and focus based on routing protocols such as Ad hoc On-demand Distance Routing Protocol (AODV), Dynamic Source Routing (DSR),