Secure Clustering in Vehicular Ad Hoc Networks
Texto
Imagem
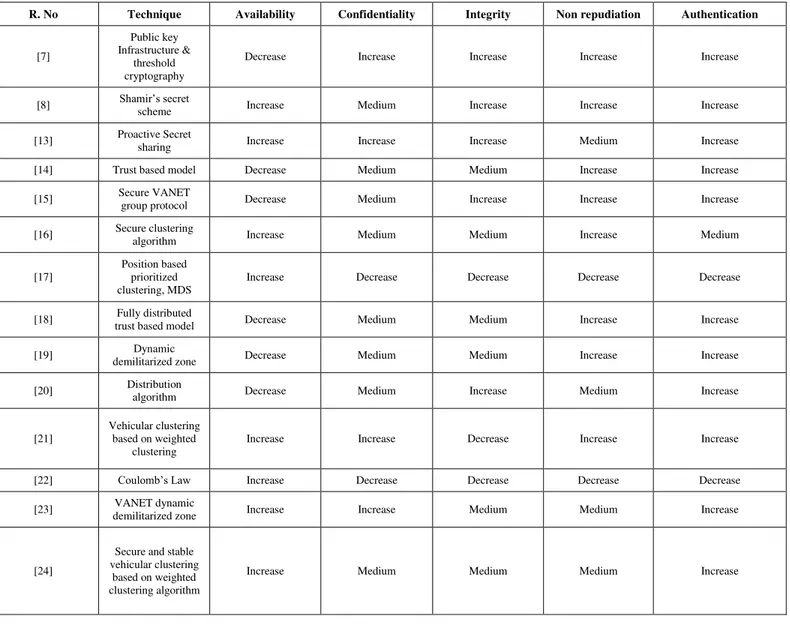
Documentos relacionados
A fast clustering algorithm based on an approximate commute time embedding for heterogeneous information networks with a star network schema is proposed in this paper by utilizing
Organizing nodes in separate groups for preventing extra data transfer is a method for reducing nodes' energy consumption but on the other hand the problem of
In this paper, a novel density based k-means clustering algorithm has been proposed to overcome the drawbacks of DBSCAN and kmeans clustering algorithms.. The result will be
In Case 1, i,e., for high level of security ( sec_ level = 1), during routing process, the source and destination nodes separately verify the authenticity of all other nodes in
Moreover, since GPACs are equivalent to systems of polynomial differential equations then we show that all real computable functions can be defined by such models..
It uses LSI (Latent Semantic Indexing); an IR (Information Retrieval) technique for induction of meaningful labels for clusters and VSM (Vector Space Model) for cluster
LEACH is a clustering algorithm, which means the nodes of the network are organized within clusters and they communicate between themselves via sensor elements called Cluster
The main purpose of BSSID configured with wildcards strengthen the sending and receiving data frames for safety communication but also support signaling of future upper