Multi-pixel Visual Cryptography for color
images with Meaningful Shares
1
Ms. KIRAN KUMARI, 2Prof. SHALINI BHATIA 1
Student, Thadomal Shahani Engineering College, Mumbai, India.
2
Professor, Computer Engineering Department, Thadomal Shahani Engineering College, Mumbai, India. kirkirankumari@gmail.com, shalini.tsec@gmail.com
ABSTRACT
The important issue of visual cryptography is visual quality of recovered image. This paper presents Multi-pixel Visual Cryptography for color images to generate two meaningful shares. Some filters are proposed for better visual quality of recovered image and a new simple watermarking algorithm is proposed to generate meaningful shares. Keywords: Visual Cryptography, Error Diffusion Halftone, Filters, Watermarking.
1. INTRODUCTION
Visual cryptography is a cryptographic technique which allows visual information (pictures, text, etc.) to be encrypted in such a way that the decryption can be performed by human visual system, without the aid of computers. It uses a simple algorithm unlike the complex.
Visual cryptography technique for black and white images (Basic) introduced by Naor and Shamir [1]. Any visual secret information ( pictures, text, etc) is considered as image and encryption is performed using simple algorithm to generate n copies of shares depending on type of access structure schemes[2, 6].The simplest access structure is the 2 out of 2 scheme where the secret image is encrypted into 2 shares and both needed for a successful decryption. These shares are random dots without revealing the secret information.
Basic visual cryptography is expansion of pixels [1]. First Continuous image (Gray scale) is converted into halftone image ( Binary) using any halftone technique as error diffusion, thresholding, ordered dithering, etc. The error diffusion gives better halftone. Each pixel of halftone is broken into some sub-pixels as shown in Table 1.
Table 1 Construction of 2-out-of-2 scheme
M0 =
0
0
1
1
0
0
1
1
M1 =1
1
0
0
0
0
1
1
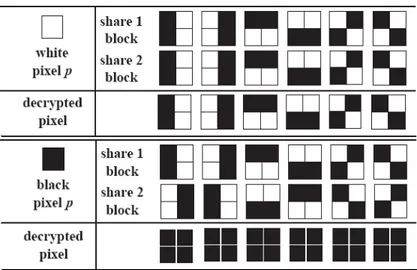
Two rows of matrices denote the number of shares to be created. If a particular pixel is white in the original image, then two rows of the matrix M0 are put into two shares, one for each. If the pixel is black in original image, then the rows of M1 are used. Thus single pixel in original image takes four positions in the shares as shown in Figure 1.1.
Figure1.1 Traditional Visual Cryptography
Decryption is achieved by stacking the shares. In case of black pixel, overlaying two rows of M1 results in four black bits, and reveals the information, where as for the white pixel, stacking the two rows of M0 results in two black and two white bits, and thus introduces noise.
Stacking shares represents OR operation to human visual system. OR operation is lossy recovery. If XOR operation is applied instead of OR then we can get lossless restore of the original image[7]. But, XOR operation requires computation. The physical stacking process can only simulate the OR operation. The drawbacks of this scheme are:
1. It is for black and white images.
2. Need more storage capacity as shares are four times the original image. 3. It is time consuming as single pixel encoding at each run.
Many advanced schemes were introduced in [3, 7] where a colored image is encrypted. A multi-pixel non-expanded scheme for color images [4] introduced which can encode more than one pixel for each run resulting same size of shares as secret image. The scheme achieves high efficiency for encoding and this works well for general access structure for chromatic images without pixel expansion but it generates meaningless shares.
This paper proposes a simple watermarking algorithm to generate meaningful shares and it proposes some filters to improve the visual quality of recovered image.
2. IMPLEMENTATION
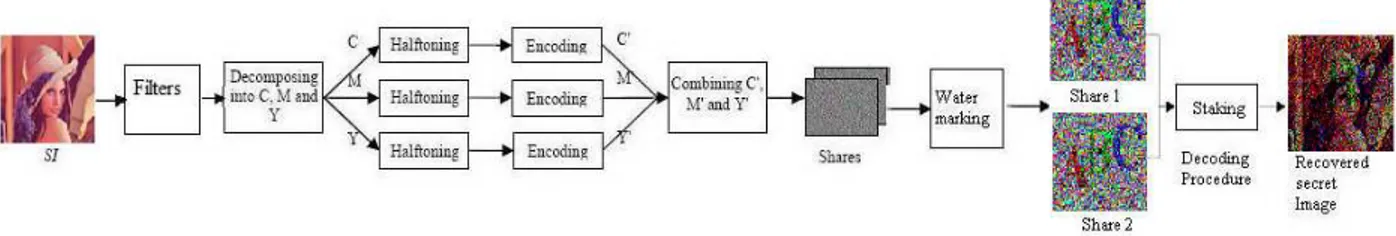
Figure 2.1 Block Diagram of Multi-pixel Visual Cryptography with meaningful shares
2.1 Filters (proposed) [8]: The following filters are used to eliminate the noise and for sharpening the input secret image:
1. Low Pass Averaging Filter: It eliminates Gaussian noise. It achieves filtering by blurring the noise. 2. Laplacian Filter: This filter is used for sharpening the image. Sharper image gives better recovered result. 3. Min and Max Filters: It eliminates salt and pepper noise.
2.2 Decomposition into C, M and Y [8]: The input image is decomposed into three channels of Cyan, Magenta and Yellow by using equation:
1Cyan = 1 – (Red/255)
2Magenta = 1 – (Green/255) and 3Yellow = 1 – (Blue/255).
Each one looks gray-scale image on the monitor. Matlab and monitor do not support CMY color model. So decomposition of image does not show C, M and Y color on the screen. Prints of images using TIFF file in Photoshop show real color (C, M and Y).
2.3 Generating print: Matlab does not have capability for displaying a CMY/CMYK images directly. TIFF file only support CYMK color model. So an array of size [M×N×4] is created for each C, M and Y image. These are filled with correct value of C, M and Y respectively and other are set to zero as for example (Cyan Image):
1C(m,n,1) = Cyan; 2C(m,n,2) = 0; 3C(m,n,3) = 0; 4C(m,n,4) = 0;
The image is saved as TIFF file. This file is opened in Photoshop CS2 to print on the color laser. To print, “No Color Management” is selected in Color Handling of File -> Print Preview. This instructs Photoshop to prevent the printer from doing its own color correction.
Figure 2.2 Block Diagram of Error Diffusion
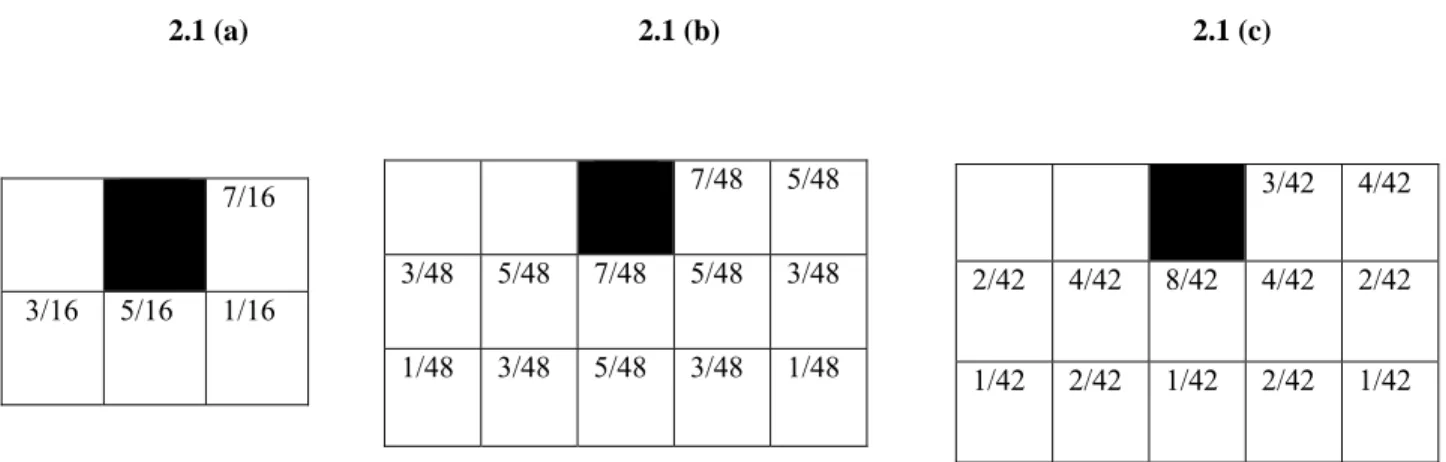
The image is scanned in raster scan fashion (left to right, top to bottom). Every pixel is threshold against a fixed threshold (T=127). If value of pixel is greater than or equal to T then output pixel gets the value 255 or else 0. The quantization error (input gray level – output gray level) is spread to the neighborhood of the input pixel, which is dependent on Error Diffusion filter or kernel, which is being used for halftone as shown in Table 2.1.
Table 2.1 Error Diffusion Kernels (a) Floyd-steinberg (b) Jarvis (c) Stucki
2.1 (a) 2.1 (b) 2.1 (c)
The black spot represents current pixel, which is being threshold. The filter coefficients in Error Diffusion filter are indexed relative to the current pixel, which determines what percentage of quantization error, is to pass to pixel at that position, relative the current pixel.
2.5 Encryption: It is applied on each halftone channel to generate shares. There will be two shares for each halftone as shown in Figure 2.3.
Cyan Magenta Yellow
C1 C2 M1 M2 Y1 Y2
Figure 2.3 Encryption
It sequentially scans the halftone channel. The length of encoding at one run is equal to the number of the consecutive same pixels met during scanning the secret image. During encoding the m integers, i.e., 1, 2,…, m, randomly rearranges to indirectly achieve the rearranging of the entire basis matrix M0 and M1.
3/42 4/42
2/42 4/42 8/42 4/42 2/42
1/42 2/42 1/42 2/42 1/42 7/48 5/48
3/48 5/48 7/48 5/48 3/48
1/48 3/48 5/48 3/48 1/48 7/16
Algorithm[4]
Input: SI with L× Hpixels; M0 and M1 with size of n × m, respectively. Output: S1 and S2with L× Hpixels, respectively.
1 Scan the secret image SItill meeting different pixel or reaching the end of SI, and two values are known: r, the span of this run, and p, the pixel type. There is p= 0 for white pixel, otherwise p= 1.
2 for ( i= 1 to ┌ r/m ┐) {
Randomly rearrange (1, 2, …, m) and write the result as Li= (l1, l2, …, lm); }
3 Concatenate all the Lis into L. Namely, L= L1 || L2 || … || L┌ r/m ┐; 4 if ( |L| > r)
{
Truncate the tail of Lto make sure that |L| = r; }
5 Fill the pixels at line iand the columns indicated by Lof Mpinto Si, where i=1,2. 6 Repeat above procedure to encode all the pixels of SI.
7 Stop.
2.6 Combining C, M and Y: One share of each encoding is combined to generate two colored shares as shown in Figure 2.4. These shares do not reveal any information about the secret image by its own. Only overlapping of shares can reveal the secret image.
Share C1 Share C2 ShareM1 ShareM2 ShareY1 ShareY2
S1 S2
Figure 2.4 Combining C, M and Y
2.7 Watermarking [proposed]: The meaningless shares are easy target for attackers. So these are watermarked on some cover images to generate meaningful shares.
Algorithm:
1. Take two copies of a cover image of same size of Secret image. 2. Apply halftone (Stucki Error Diffusion) on cover images.
3. Replace ¼ 1’s pixels of first halftone cover image by share, S1 pixels and second halftone cover image by share, S2 pixels.
4. Replace all 0’s pixels of first halftone cover image by S1 pixels and second halftone cover image by S2 pixels.
5. Stop.
3. RESULTS
Figures from 3.1 to 3.7 represent the results of each step of the system. Size of images is resized to fit in the paper. Figure 3.8 shows recovered image without using filters. Figure 3.9 represents halftone using different kernels.
(a)Input Image (b)Filterd I/P Image
Figure 3.1 (a) Secret Image. (b) Filtered Secret Image
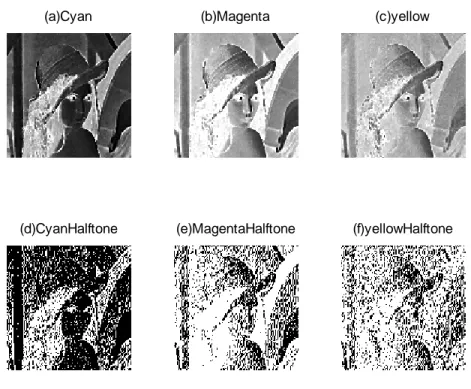
(a)Cyan (b)Magenta (c)yellow
(d)CyanHalftone (e)MagentaHalftone (f)yellowHalftone
(a)CyanS1
(b)CyanS2
(c)MagentaS1
(d)MagetaS2
(e)YellowS1
(f)YellowS2
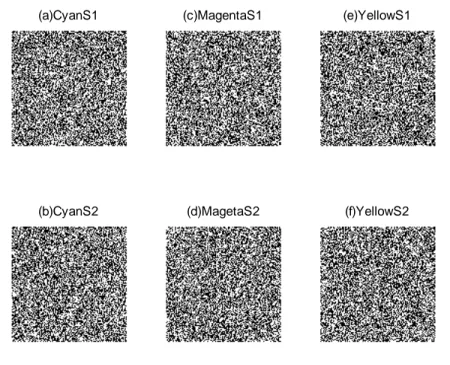
Figure 3.3 Encoding (a) & (b) Two shares of Cyan channel (c) & (d) Two shares of Magenta channel (e) & (f) Two shares of Yellow channel
(a)Share1 (b)Share2
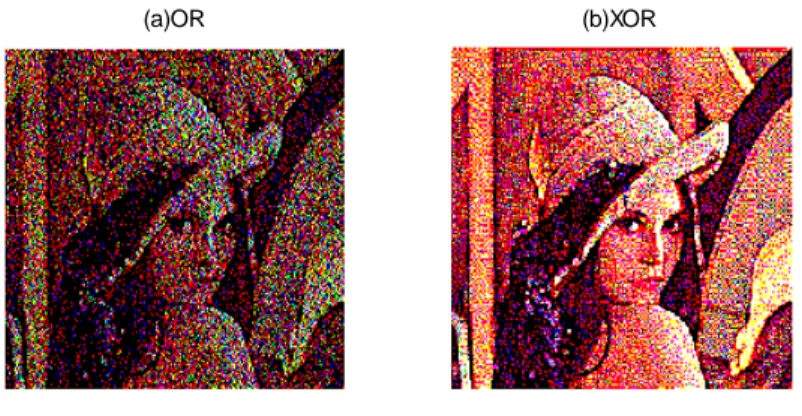
(a)OR (b)XOR
Figure 3.5 Reconstruction (a) result of OR operation of shares of figure 3.4 (b) result of XOR operation of shares of figure 3.4
(a)Watermark Halftone (b)Watermarked Share1 (c)Watermarked Share2
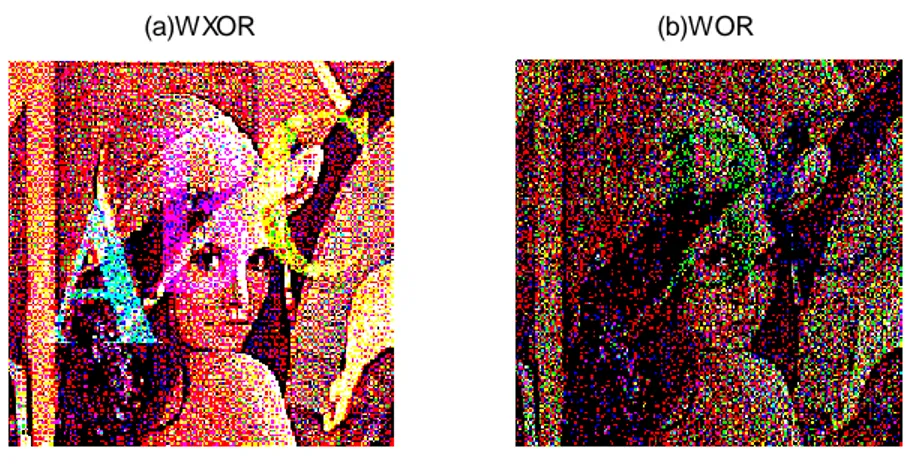
(a)WXOR (b)WOR
Figure 3.7 Reconstruction (a) XOR operation of shares (b) and (c) of figure 3.6 (b) result of OR operation of shares (b) and (c) of figure 3.6
(a)WXOR (b)WOR
(a)Floyd (b)Jarvis (c)Stucki
Figure 3.9 Halftone of Lena image using different kernels (a) Floyd (b) Jarvis and (c) Stucki
4. CONCLUSION
Different kernels of halftone (Figure 3.9) are compared. Stucki kernel gives better halftone visual quality. Shares before watermark are random dots so it does not reveal the secret information. For better security, shares are watermarked on other cover image using simple watermark algorithm. This gives meaningful shares without revealing the secret information. The secret information is revealed by overlapping of meaningful shares. The quality of recovered image (Figure 3.7) is improved by filters.
REFERENCES
[1] M. Naor and A. Shamir, Visual cryptography, Advances in Cryptology EUROCRYPT ’94, Lecture Notes in Computer Science, vol.950, no.7, pp.1–12, 1995.
[2] Debasish Jena and Sanjay Kumar Jena, A Novel Visual Cryptography Scheme, International Conference on Digital Object Identifier, pp.207 – 211, 2008.
[3] Hsien-Chu Wu, Hao-Cheng Wang and Rui-Wen Yu, Color visual Cryptography Scheme using Meaningful Shares, Eighth International Conference on Digital Object Identifier, Volume 3, pp.173 – 178, 2008.
[4] Haibo Zhang, Xiaofei Wang, Wanhua Cao and Youpeng Huang, Visual Cryptography for General Access Structure by Multi-pixel Encoding with Variable Block Size, International Symposium on Digital Object Identifier, pp.340 – 344,2008.
[5] Zhongmin Wang and Gonzalo R. Arce, Halftone visual cryptography through error diffusion, IEEE Transactions on Digital Object Identifier, Volume 4, Issue 3, pp.109-112, 2006.
[6] Chetan Hegde ,Manu S, P. Deepa Shenoy, Venugopal K R and L M Patnaik, Secure Authentication using Image Processing and Visual Cryptography for Banking Application, 16th International Conference, pp.65-72, 2008.
[7] Duo Jin, Wei-Qi Yan, Mohan S. Kankanhalli, Progressive color Visual Cryptography, Journal of Electronic Imaging,Vol.14, No. 3, pp.033019(1-13), July-Sep 2005.