A survey on top security threats in cloud computing
Texto
Imagem
Documentos relacionados
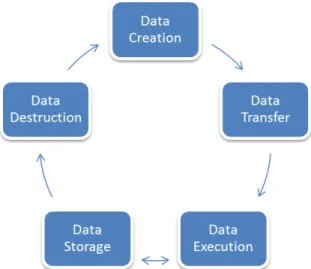
Cloud computing consist of three layers like Infrastructure as a service (Iaas) is a lowest layer, it provides the basic infrastructure support services, Platform as a service
Phospho-ERK expression was found to be higher in malignant tumors compared to benign tumors or normal adrenal glands, suggesting that MAPK/ERK pathway activation could
A number of systems lie in-between, providing client views that exhibit some degree of guarantees, for example: guarantee- ing that all causal dependencies are observed
O que igualmente sobressai destes registos é a instrumentalidade que adquirem os medicamentos prescritos na legitimação, não só das práticas, mas, simultaneamente, das
Temporal Attribute-based Access Control (TAAC) is proposed to provide the efficient data access control schemes in multi authority cloud storage systems on attribute level.. In
The cloud computing security based on fully Homomorphic encryption, is a new concept of security which enables providing results of calculations on encrypted
proposed model that is, “Quality based Enhancing the user data protection via fuzzy rule based systems in cloud environment ”, will helps to the cloud clients by
A Survey on Cloud Computing Security Issues, Vendor Evaluation and Selection.. Process: World Future Society