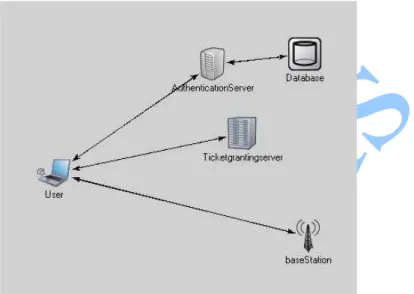
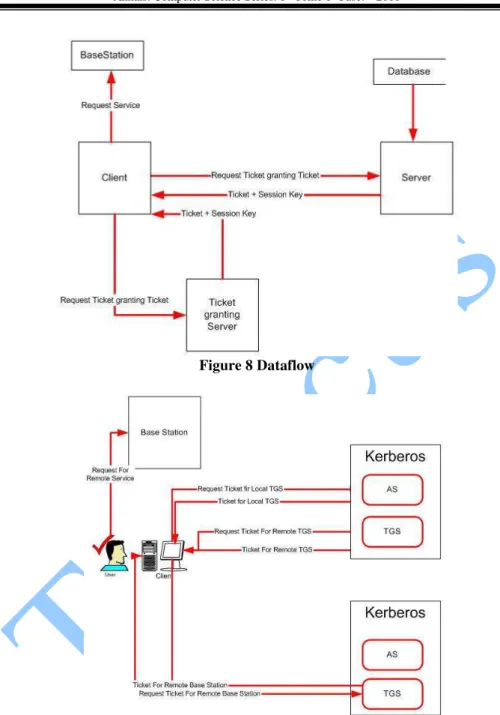
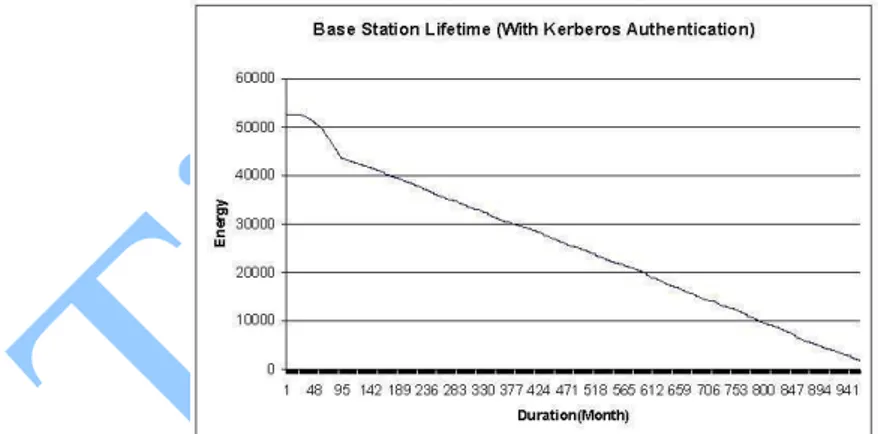
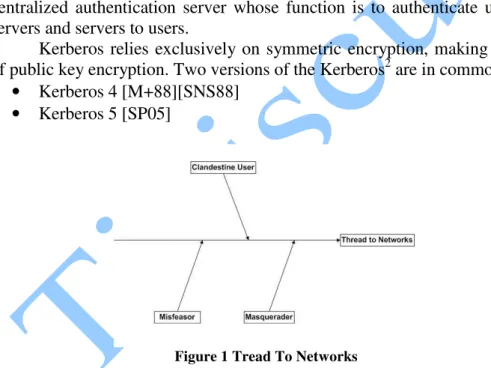
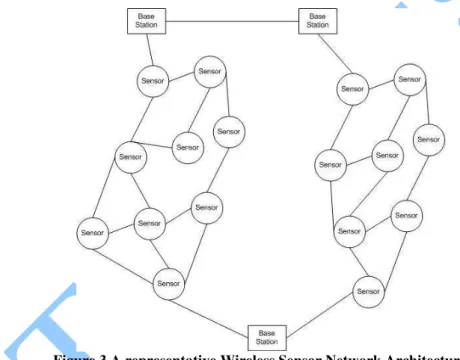
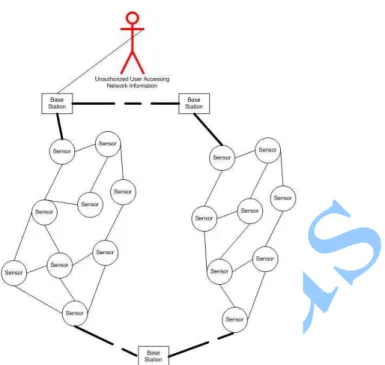
Kerberos Authentication in Wireless Sensor Networks
Texto
Imagem
Documentos relacionados
Entre todas as localidades, destaca-se Delmiro Gouveia que apresentou período de retorno superior a 50 anos, sendo, aproximadamente, 18 anos para o cultivo da
We make two main points regarding the impact of POB on organizational behavior research: first, we acknowledge that POB is a biased approach that focuses on middle-range
social assistance. The protection of jobs within some enterprises, cooperatives, forms of economical associations, constitute an efficient social policy, totally different from
Abstract: As in ancient architecture of Greece and Rome there was an interconnection between picturesque and monumental forms of arts, in antique period in the architecture
" JJJJJJJJJJJJJJJJJJJJJJJJJJ
The probability of attending school four our group of interest in this region increased by 6.5 percentage points after the expansion of the Bolsa Família program in 2007 and
A título de exemplo, usaremos o doente IV: pelo método de ELISA este doente obteve resultados positivos para um painel múltiplo de alergénios alimentares