Mathematical Attacks on RSA Cryptosystem
Texto
Imagem


Documentos relacionados
O objetivo dessa pesquisa foi realizar um estudo observacional sobre classe econômica, estresse e disfunção temporomandibular em servidores do Centro de Ciências Biológicas e da
Já os ministros civis, dentre 35 e 65 anos, devem ser escolhidos dentre 03 advogados de notório saber jurídico e conduta ilibada (com mais de 10 anos de efetiva
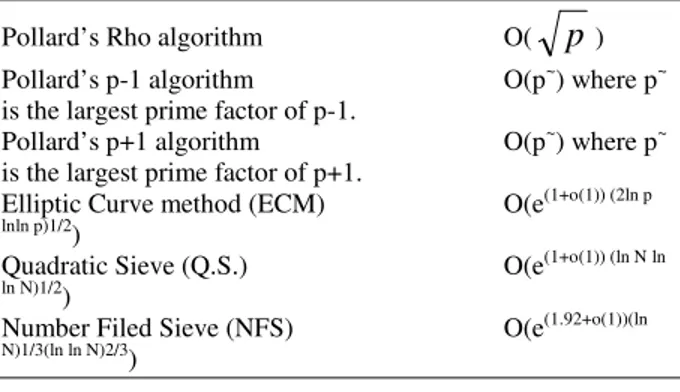
The major advantage gained in the security enhancement described above is making RSA system immune against many well known attacks on basic RSA cryptosystem, thus making the
ECDSA and RSA are used for digital signature generation and their performance is compared based on the combination of algorithms as given in Table 2.. The time delay
SAODV protocol is capable for defense against the two attacks namely Replay and Routing table poisoning remaining attacks cannot be defended by it.. (v)
Two attacks that will probably be detected by this rule are the negligence attack, in which the intruder does not send data messages generated by a tampered node, and the
Based on their functionality attacks may be classified into three types, attacks on secrecy of data, attacks on availability of nodes, attacks on the network:..
In order for our attack model to be capable of implementing variety types of smurf attacks, we need to involve main factor affecting the severity of smurf attack. Therefore,