Identity-based Trusted Authentication in Wireless Sensor Networks
Texto
Imagem


Documentos relacionados
terreno: Setem: un año y un mes; Secretaria de Joventut “Jove Cooperant” Generalitat de Catalunya: 6 meses; Paz y desarrollo: 1 año; ACPP: “Programa
Keywords: Target localization, target tracking, wireless sensor network, received signal strength (RSS), angle of arrival (AoA), convex optimization, maximum likelihood (ML)
This work proposes and evaluates a sampling algorithm based on wavelet transforms with Coiflets basis to reduce the data sensed in wireless sensor networks applications.. The
The following topics have marked the scientific knowledge production in what refers to the research that the participants of the line are actually working: novice and
A set of biosensors deployed or implanted in the human body constitutes a subtype of WSN named Wireless Body Area Networks (WBANs) also known as Wireless Body Sensor
The service layer contains most of the services required for communication and discovery. This layer invokes its service after receiving the message from the application
The main purpose of the paper is to provide an overview of the architecture of the Kerberos authentication service and using the Kerberos authentication services in Wireless
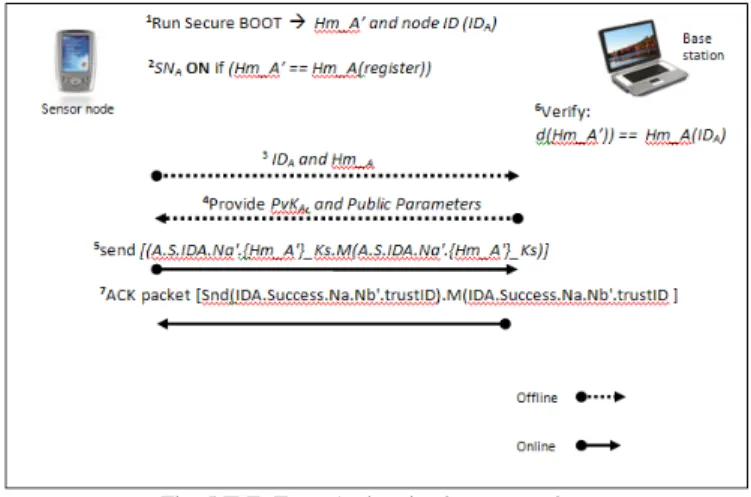
In the case of sensor networks, it is essential for each sensor node and base station to have the ability to verify that the data received was really sent by a
