Authenticated Broadcast in Heterogeneous Wireless Sensor Networks using Chinese Remainder Theorem Algorithm
Texto
Imagem

Documentos relacionados
Keywords: Target localization, wireless sensor network (WSN), received signal strength (RSS), angle of arrival (AoA), convex optimization, maximum likelihood (ML)
Keywords: Target localization, wireless sensor network (WSN), received signal strength (RSS), angle of arrival (AoA), convex optimization, maximum likelihood (ML)
In (Ankita Agarwal 2012), Ankita proposed a method based on Genetic Algorithm (GA) which is used to produce a new encryption method by exploitation the powerful features of
The algorithm encryption and decryption of an image transform an image into cipher code using the random keys, which allow users to have confidentiality and security in
We believe that the encoding of cryptographic algorithms is an important step in that direction, and it is the main reason why in this paper we present a
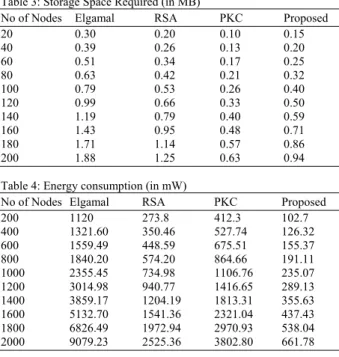
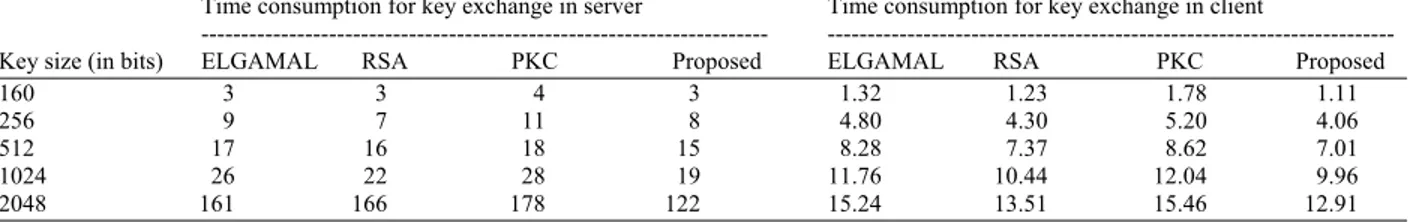
ECDSA and RSA are used for digital signature generation and their performance is compared based on the combination of algorithms as given in Table 2.. The time delay
To overwhelm the challenge faced by WSNs, this paper proposes a scheme which efficiently detects the captured nodes by using a novel technique, embedded with an Intrusion
Elliptic curve cryptography Public Key Cryptography, embedded systems, Elliptic Curve Digital Signature Algorithm ( ECDSA), Elliptic Curve Diffie Hellman Key