Security Risk Assessment of Cloud Computing Services in a Networked Environment
Texto
Imagem
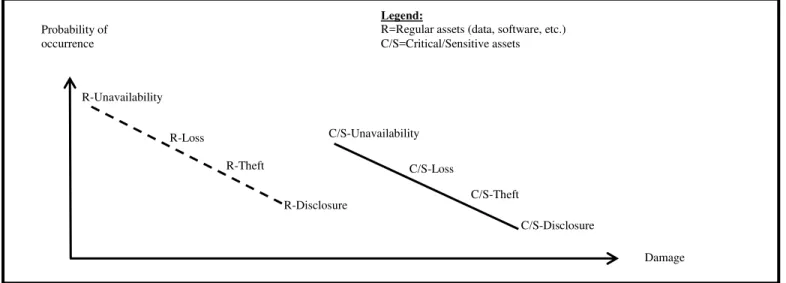
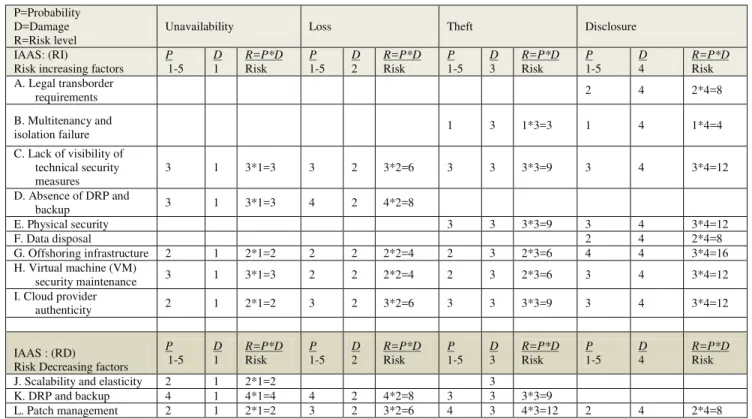
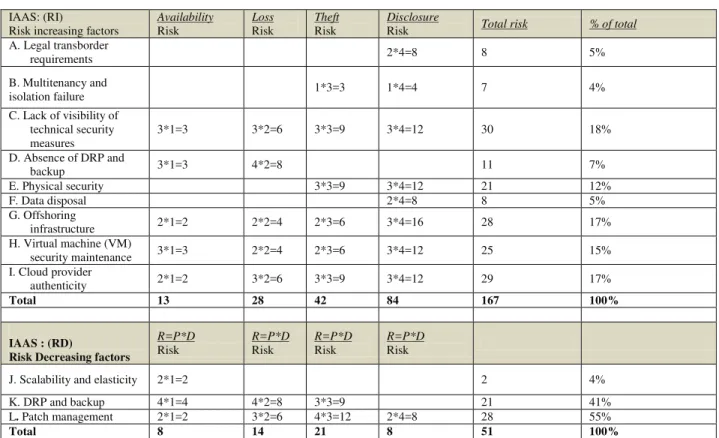
Documentos relacionados
This can be done by specifying parameters that we would like to monitor in a Service Level Agreement (SLA) and making sure that the cloud service provider monitors
With this in mind, the cloud computing system (OpenStack) described in this chapter aims to provide the core features of a cloud computing architecture, On-demand self- service
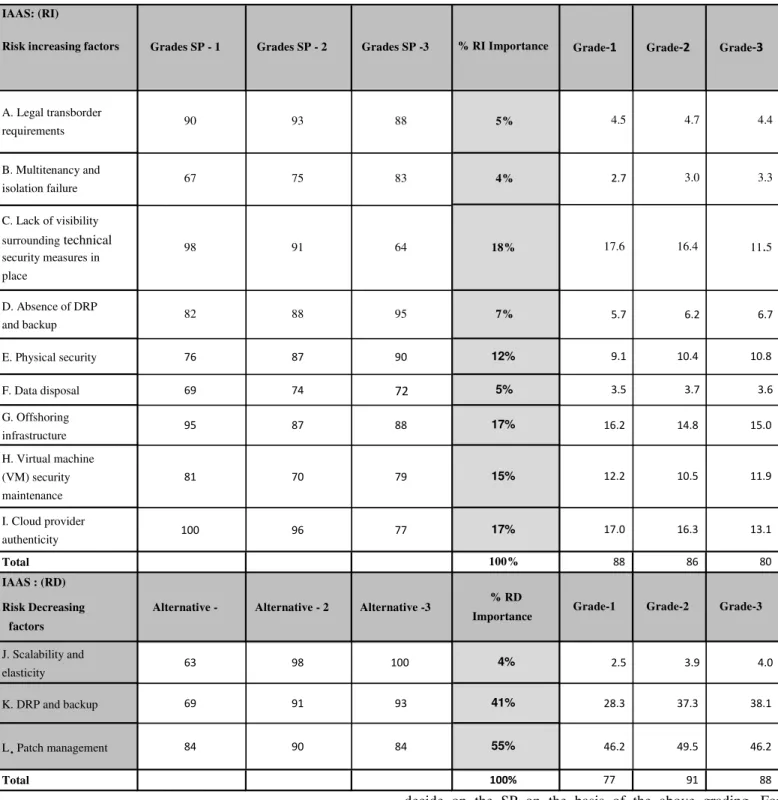
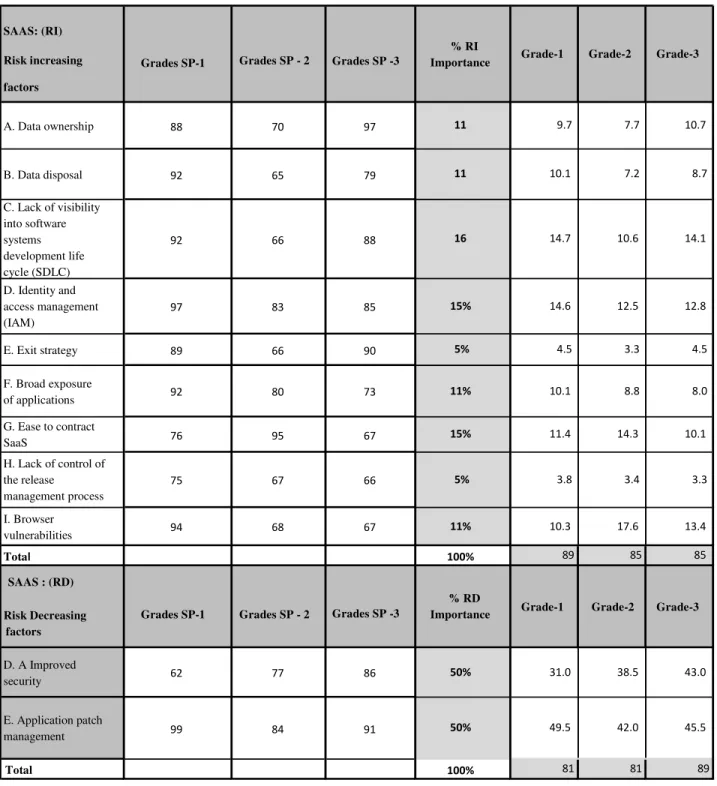
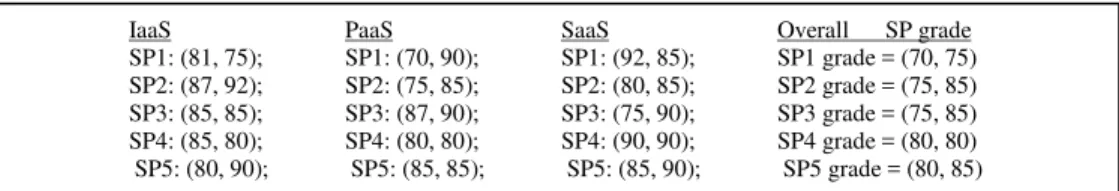
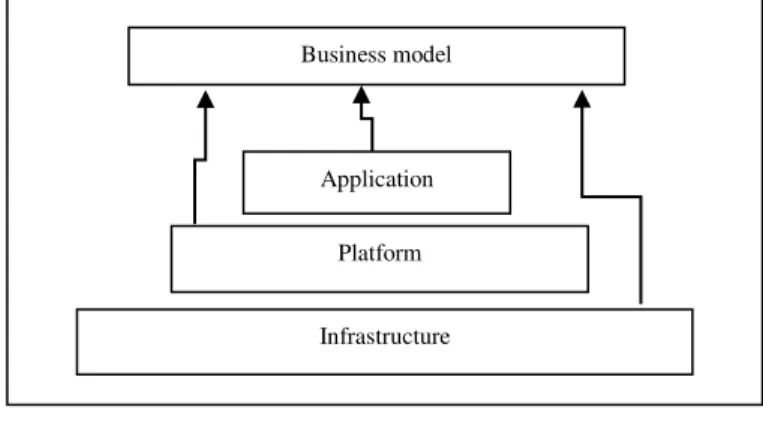
Cloud computing providers offer services built around three fundamental models: Infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service
Cloud computing consist of three layers like Infrastructure as a service (Iaas) is a lowest layer, it provides the basic infrastructure support services, Platform as a service
Pais e filhos apresentam semelhanças ao nível das dimensões, Relacional, Equilíbrio Pessoal e Tradicionalismo, e diferenças na Preocupação Social (mais
Overall, this set of empirical results support the existence of a subsample of countries (Germany, France, United States of America and Canada) where it is found statistically
Amazon VPC enables enterprises to connect their existing infrastructure to a set of isolated AWS compute resources via a Virtual Private Network (VPN) connection, and to extend
1) Protection from Data Breaches: Various security mea- sures and techniques have been proposed to avoid the data breach in cloud. One of these is to encrypt data before storage