Routing Based Data Security in Mobile Ad Hoc Network Using Group Key Management
Texto
Imagem

Documentos relacionados
13 show the efficiency of our algorithm in generating the key for small and large group sizes compared with dual-level key management for secure grid communication in dynamic and
In this protocol, the KS broadcasts the rekey information to all the group members. Chiou and Chen [9] proposed Secure Lock protocol, in this key server uses a
Routing is the critical issue in the MANET and focus based on routing protocols such as Ad hoc On-demand Distance Routing Protocol (AODV), Dynamic Source Routing (DSR),
Approach: Network coding-based broadcasting was proposed which focuses on reducing the number of transmissions each forwarding node performs in the multiple source/multiple
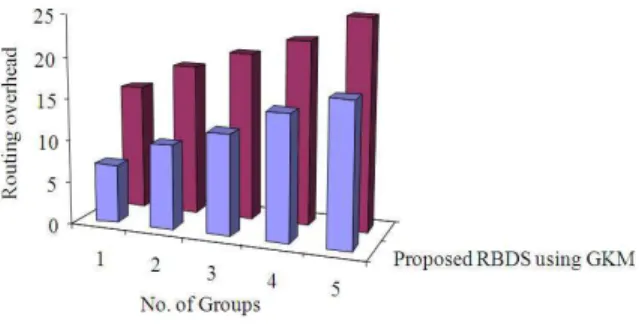
The proposed method states that the mobile nodes must be formed as groups for better security .It generates message authentication code during route discovery phase and then
Upendra Kumar [7] proposed a secure key exchange and encryption mechanism for group communication in wireless adhoc networks that aims to use the MAC address as an
Messages send by central node to group members by using the hash of the encryption keys that are known to compromised nodes.. Hence using the keys of the compromised nodes it is
heads’ double trees, a neighbor of leaved member detects that there is a member leaved, and inform both the main cluster head and its cluster head to refresh the double multicast