16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 22 a 24 de Setembro de 2016, Porto, Portugal
ISSN 2183-489X
DOI http://dx.doi.org/10.18803/capsi.v16.16-24
16
An analysis of the alignment of the contracts for Cloud Computing with the
norms and recommendations
Teófilo Branco Junior, University of Minho, Portugal, teofilotb@hotmail.com
Abstract
This study evaluated whether the content of the contracts for the provision of IT services platforms in Computer Cloud (PaaS) of some suppliers is adequate to ensure the good practices of an offer and use these services by vendors and clients. To can be auditable, the services agreements must comply with the recommendations and standards of the regulatory bodies and these must clearly be being in their contracts. Through a literature review, this study analyzed the established standards and recommendations under consideration by groups of normative research of the cloud environment. After, we conducted a study about the contractual clauses for the provision of IT services platforms in Cloud for some well-known suppliers that divulge their contracts on the web. A comparison between the recommendations and the terms of these contracts demonstrates there is still a lot to improve this relationship to provide compliance to safety auditability between both parties.
Keywords: Cloud Computing, Information Security, Platform as a Service (PaaS), auditability, Service Level Agreements (SLA).
1. I
NTROCUCTIONThe contracting of services under the modality Cloud Computing (CC) is a tendency of growing in the
market and has been several discussions about the security and auditability about this in recent times (Zhu,
Hu, Ahn, & Yau, 2012).
Several IT companies promise advantages in a use of these services such as decrease customer costs in
exchange for more advanced and specialized technologies. This proposal can be attractive and advantageous
for both parties, because the customers in delegating the IT infrastructure maintenance tasks to highly skilled
companies, can focusing their efforts on their end activity. Therefore, the suppliers can provide better
services for their clients increase your receipts and consolidating their business Cloud Computing (Chen,
Paxson, & Katz, 2010a).
However, several issues related to security and quality of service provision has raised discussions in
academia and reflections in the business community about the risks involved in adopting this model of
service at this time. One concern in this regard relates to the establishment of a formal trust relationship
between contractors and providers of this service by establishing Service Level Agreements (SLA) and the
feasibility of audits to verify the delivery of these services. To make viable this idea is must create ways of
verifying these clauses so that contractors and entrepreneurs can control and monitoring their contracts (M.
Kanchana, Sk. Nazar Hussain, Kumar, & Praveen, 2013).
16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 17
This article makes an analysis of the cloud provider contracts applied in this moment and checks if they are
aligned with the regulators entities norms and safety recommendations in their clauses.
2. T
HE LITERATURE REVIEWThe research was conducted to know the rules and recommendations published by institutions involved in
regulating the CC area. The study included the following topics: Standards and recommendations for CC;
and relevant metrics and measures related to the CC.
The following entities that publish and conduct study groups in CC were considered. We selected the entities
by criteria of a significant number of publications and relevance regarding the technical norms:
NIST National Institute of Standards and Technology;
EU - European Commission and ENISA - European Network and Information Security Agency;
ISO - International Organization for Standardization;
IEEE - Institute of Electrical and Electronics Engineers;
ETSI - European Telecommunications Standards Security;
CSMIC - Cloud Services Measurement Initiative Consortium;
DMTF - Distributed Management Taskforce;
OMG - Object Manage Group CSCC - Cloud Standards Customer Council;
CSA - Cloud Security Alliance;
ISACA - Information Systems and Control Association Inc;
HISPI - Holistic Information Security Practitioner Institute;
SANS Institute.
In another hand, four companies that published their contracts on the Internet were selected. These
companies were chosen from the publication of NetworkWorld magazine (“Networkworld,” n.d.) listed the
ten most PaaS providers highlighted in its release on June 4, 2014:
Amazon;
Windows Azure;
IBM;
16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 18
Amazon RDS SLA – Database (AWS - Amazon Web Services, 2013a); Amazon EC2 SLA – Elastic (AWS -
Amazon Web Services, 2013c); Amazon S3 SLA – Storage (AWS - Amazon Web Services, 2013b);
Amazon Cloud Watch (AWS - Amazon Web Services, 2010)
Services Level Agreements (W. Azure, 2015);
IBM Cloud Services Agreement - Bluemix IBM (IBM, 2014);
Google Compute Engine Service Level Agreement SLA (Cloud, 2014).
3. T
HEC
LOUDC
OMPUTING ENVIRONMENTCloud Computing (CC) are deposits of virtualized IT resources readily usable and accessible, in which the
vendor warranties of use and quality of use of these services and the user is tariffed only for what you use.
The service provider supplies the customer's computing resources disengaging it from the purchase and
maintenance of IT infrastructure (Mell & Grance, 2011).
CC is a service model where the premise is providing all kinds of processing information systems and
technological applications, through the provision of infrastructure and data storage over the internet, based
mainly on the user's consumption needs (Buyya, Broberg, & Goscinski, 2011).
A service-level agreement (Service Level Agreement - SLA) is a contract between a supplier of IT services
and a customer specifying in general and often contain measurable terms of what services the client will pay.
Service levels are set at the beginning of any hiring ratio of IT services and are used to measure and monitor
the performance of a vendor supplier (Armbrust, Fox, Griffith, & Joseph, 2009).
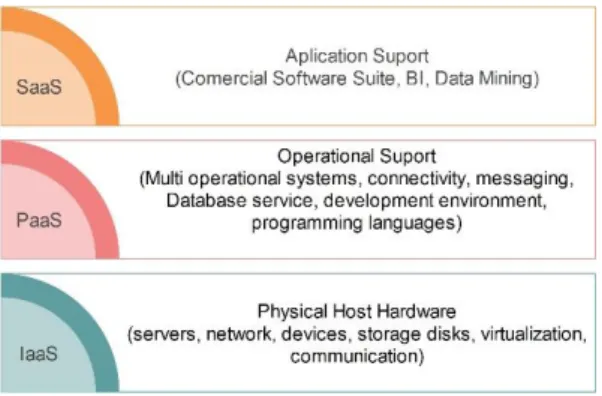
The services can be categorized in three layers of computing resources: Infrastructure as a Service (IaaS),
Platform as a Service (PaaS) and Software as service (SaaS) (Armbrust et al., 2009). Figure 1 illustrates such
layers.
Figure 1- Layers in Cloud Computing
The analysis of this paper considers the availability of resources PaaS layer. This choice is because this layer
is the intermediate and the most appropriate for organizations that have their software and applications.
16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 19
4. T
HE STANDARDS AND RECOMMENDATIONSCurrently, several agencies are working to develop specific safety standards for cloud computing, taking
these surveys for a large number of areas including auditing, applications, encryption, governance, network
security, risk management, storage and virtualization. Through literature review, we identified some entities
that develop relevant studies on the establishment of standards, procedures and recommendations through
their research work groups in CC. Table 1 presents a summary of approaches to each organ.
ENTITY REFERENCE PUBLICATIONS
NIST National Institute of Standards and Technology
NIST SP 800-53r4 (National Institute of Standards and Technology, 2013b); NIST SP 800-144 (Jansen & Grance, 2011); NIST 500-292 – Architecture (Liu et al., 2011); NIST 500-299 SP- Architecture (National Institute of Standards and Technology, 2013a); NIST 500-307 – Metrics (National Institute of Standards and Technology, 2015).
EU - European Commission and ENISA - European Network and Information Security Agency
Trusted Cloud Europe (European Commission, 2014b); A guide to monitoring of Security SLA (Giles Hogben, 2012); Incident reporting for cloud computing (Dekker, Liveri, & Lakka, 2013); Benefits, risks, and recommendations for information security (Catteddu & Hogben, 2009); Cloud Security Guide to SMEs (Dimitra, 2015); CSIG Cloud Service Level Agreement Standardisation Guidelines (European Commission, 2014a).
ISO - International Organization for Standardization (JTC 1/SC38 - ISO/IEC JTC 1/SC 38)
Catalogue Under development since 2014-09-22
ISO/IEC 17788:2014 Information Technology - Cloud Computing - Overview and vocabulary; ISO/IEC 17789:2014 Information Technology - Cloud Computing - Reference Architecture; ISO/IEC 17826:2012
Information Technology - Cloud Data Management Interface (CDMI); ISO/IEC AWI 19941 Information Technology - Cloud Computing - Interoperability and Portability; ISO/IEC AWI 19944 Information Technology - Cloud Computing - Data and their Flow across Devices and Cloud Services; ISO/IEC NP 19086-1 Part 1: Overview and concepts; ISO/IEC NP 19086-2 Part 2: Metrics; ISO/IEC NP 19086-3 Requirements IEEE - Institute of Electrical and
Electronics Engineers Standard P2301 Working Group; Standard P2302 Inter Cloud. ETSI - European
Telecommunications Standards Security
Cloud Standards Coordination (ETSI, 2013) CSMIC - Cloud Services
Measurement Initiative Consortium
CSMIC framework 2.1 Overview (CSMIC, 2014) DMTF - Distributed
Management Taskforce
Base Metrics Profile DSP1053 - 2011.07.31 (Benke et al., 2012); Cloud Audit Data Federation DSP 2038 (Management Task Force, 2015) OMG - Object Manage Group
CSCC - Cloud Standards Customer Council
Practical Guide to Cloud SLA V 1.0 (Meegan, Singh, Woodwar, Venticinque, & Rak, 2012)
CSA - Cloud Security Alliance (Guidance V.4: In development)
CSA releases the Cloud Trust Protocol data model and API (CSA Cloud Security Alliance, 2015); CSA Guidance V.3.0 (CSA Cloud Security Alliance, 2011); Cloud Control Matrix v3.01
ISACA - Information Systems
and Control Association Inc. Controls and Assurance in Cloud COBIT-5 (ISACA, 2014) HISPI - Holistic Information
Security Practitioner Institute CAAP Validate Score
SANS Institute Security SLA for Cloud (Hoehl & Pelaez, n.d.) Table 1 - Norms and references for entities that study the CC
16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 20
On The CC environment, one of the challenges is to develop mutual auditing templates for agreements
management (SLAs), so that may be established a trust between the partners, thus consolidating the use of
this environment through a formal relationship, involving relevant legal responsibilities (Chen, Paxson, &
Katz, 2010b)
After analyzing the entities that conduct studies within the framework of rules and procedures in CC, there is
a series of standards and recommendations proposed to become the safest CC environment and proposes to
serve to support service contracts through clauses SLA.
Notes a greater standardization between entities regarding metrics and principles adopted for the SLA
agreements. Some bodies develop joint studies to establish standards and regulations for the CC
environment.
In general, the recommendations are based on processes considered "best practices" adopted in traditional IT
environment and SI being adapted the specifics of the CC environment.
The analysis of these norms and recommendations demonstrates the follows areas of interest: Technical
security mechanisms, safety guidelines recommendations, establish specific metrics for measuring
performances of safety and compliance.
5. T
HE CONTRACTUAL TERMS OF SOMEP
AAS
SUPPLIERSThe supply contracts by the selected companies (Amazon, Azure, IBM and Google) were listed the main
clauses and metrics involved in SLA agreements by a corporation, as shown in Table 2.
ENTITY REFERENCE PUBLICATIONS CLAUSES APPROACHED IN SLAS CONTRACTS
AWS - Amazon Web Service
Amazon RDS SLA – Database (AWS - Amazon Web Services, 2013a); Amazon EC2 SLA – Elastic (AWS - Amazon Web Services, 2013c); Amazon S3 SLA – Storage (AWS - Amazon Web Services, 2013b); Amazon Cloud Watch (AWS - Amazon Web Services, 2010)
Specification in uses cases and compensation in case of not available services; Access error rate; possible uptime in the month.
Windows
Azure Services Level Agreements (W. Azure, 2015)
Billing about deployment sites, using the Visual Studio online, manages traffic on the network, storage with geographic redundancy, use access to SQL database, site recovery service, Event Hubs services, Notification Hubs, Service Bus, Transaction research, Task Scheduler, using RemoteApp service, Multifactor Authentication Service, Activity mobile services, Protection to content, Media Services, HD Insight, Using Express route service, Performance measurement, Cache utilization, Using BizTalk, Backup service, Automation, API Management
IBM Smart Cloud
IBM Cloud Services Agreement - Bluemix IBM (IBM, 2014)
Best Practices to developed SLAs in Cloud (Myerson, 2013)
Forms of consulting contracts and helpdesk uses; specification about charging services; data security modes involving isolation, users identify; disposed of possible logs available.
16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 21 Google App
Engine
Google Compute Engine Service Level Agreement SLA (Cloud, 2014).
Google Cloud Platform Terms (Google Cloud Platform, 2015)
Only clauses about uses and compensations in case of services unavailable.
Table 2 - Cloud Suppliers, references publications and principals’ clauses in SLAs contracts
Most of the provisions services (SLAs) are related to loading conditions and service availability. In most
contracts, to deal with the availability services are referenced through metrics that represent the performance
and availability of each of the services listed in a period of 30 days. Each service has its calculation formula.
The focus of the major terms in the SLA contracts of suppliers refer to commercial clauses of use like prices
for the services. Some of these clauses establishing rates and payment punishment in defaults rate cases.
The other content of the terms refers to the availability services. All the providers, in their contracts, offer
pledge a compensation for unavailability of any service through a corresponding time credit in minutes to
deduce from the next bill.
Another fact verified refers to the lack of a standardization of common nomenclatures by contractual
arrangements between companies and for the metrics used in contracts by the providers themselves. In this
way, each supplier has its proprietary metrics.
Regarding the possibility of monitoring or audit, service providers Microsoft Azure (M. Azure, 2015) and
IBM (IBM, 2014) allow the customer chooses to hire a third party to perform the control. However,
Microsoft's Azure contract (M. Azure, 2015) limits the scope of restricting the number of these companies
through a list of accredited companies that the customer can hire. The others companies do not allow
auditing or external monitoring by limiting the use of a monitoring tool of its property, for which the
customer even paid for their use.
The SLAs provided by suppliers only dealing with legal terms involving financial issues such as payments,
deadlines and responsibilities for such by the contracting client.
6. T
HE SUPPLIERS AUTHORIZATIONS FOR VERIFY THE COMPLIANCERegarding the possibility of monitoring or audit, service providers Microsoft Azure (M. Azure, 2015) and
IBM (IBM, 2014) allow the customer chooses to hire a third party to perform the control. However,
Microsoft's Azure contract (M. Azure, 2015) limits the scope of restricting the number of these companies
through a list of accredited companies that the customer can hire. The others companies do not allow
auditing or external monitoring by limiting the use of a monitoring tool of its property, for which the
customer even paid for their use. Table 3 shows the explicit permissions of the Sla`s PaaS suppliers related in
Section 5 to verify the compliance with the regulatory standards listed in Section 4.
16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 22 SLA`S SUPPLIER PROPRIETARY AUDIT / MONITORING THIRD PART
MONITORING THIRD PART AUDIT ASSUMPTION RISKS
AWS - Amazon Yes Not permit Not permit No
Windows Azure No With restrictions With restrictions No
IBM Smart Cloud No Permit Permit No
Google App Engine Yes Not permit Not permit No
Table 3 - Comparison with SLA`s Supplier
7. C
ONCLUSIONSThis study allowed us to examine the compliance of provider CC contracts from the perspective of what is
required to ensure an auditability environment and how it can guarantee by contractual clauses (SLAs).
From regulators entities, note that the primary concern is the safety of the CC environment and the users’
operations involved in the cloud. In this sense, the providers of IT services in cloud publish some guides, but
their observance does not is mentioned in contracts clauses.
Regarding regulatory bodies, it is clear that these are developing in-depth studies, but many of them are not
consolidated yet. Many of the proposed standards are still in development or under review.
On the other hand, from the perspective of CC providers, the primary focus is the commercial, as shown by
the clauses dealing with billing services and regarding the issue of availability of the environment. On the
latter, some compensation given to the client for a possible unavailability of the environment is through
discounts on future rates over the coming months.
For aspects of confidentiality and integrity, some vendors omit or do not address explicitly and transparent
forms of verification and the implications that providers are subject. Another fact that stands out is how to
monitor services, often through use of metrics and measurement tools imposed by CC own service providers.
The omission in some security requirements in SLA agreements proposed by providers leads to the
conclusion that is not possible to offer guarantees about the safety and the quality of services explicitly in the
contracts.
There is still a need for many studies and work to develop for improving relationships between the suppliers
and customers in this scope, clearly defining the issues surrounding security and normative uses in the
business relationship through in the formal contracts to allow audits.
8. A
CKNOWLEDGMENTSOur thanks to ALGORITMI CENTER - The research unit of the School of Engineering - University of
Minho - Portugal to support this publication. This work has been supported by FCT - Fundação para a
Ciência e Tecnologia within the Project Scope UID/CEC/00319/2013.
16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 23
9. R
EFERENCESArmbrust, M., Fox, A., Griffith, R., & Joseph, A. (2009). Above the clouds: A Berkeley view of cloud computing.
University of California, Berkeley, Tech. Rep. UCB, 07–013. Retrieved from http://scholar.google.com/scholar?q=intitle:Above+the+clouds:+A+Berkeley+view+of+cloud+computing#0 AWS - Amazon Web Services. (2010). Amazon CloudWatch Developer Guide API Version 2010-08-01 Amazon
CloudWatch : Developer Guide.
AWS - Amazon Web Services. (2013a). Acordo de Nível de Serviço Amazon RDS. Retrieved from https://aws.amazon.com/pt/rds/sla/
AWS - Amazon Web Services. (2013b). Contrato de Nível de Serviço do Amazon S3. Retrieved from https://aws.amazon.com/pt/s3/sla/
AWS - Amazon Web Services. (2013c). Contrato de Nível de Serviços da Amazon EC2. Retrieved from https://aws.amazon.com/pt/ec2/sla/
Azure, M. (2015). Contrato de Nível de Serviço do Microsoft Azure. Retrieved from http://azure.microsoft.com/en-us/support/legal/sla/
Azure, W. (2015). Service Level Agreements. Retrieved from https://azure.microsoft.com/en-us/support/legal/sla/ Benke, O., Johanssen, M., Maier, A., Merkin, A., Papanyan, K., Schopmeyer, K., & Shah, N. (2012). Base Metrics
Profile V2, 1–91. Retrieved from
http://www.dmtf.org/sites/default/files/standards/documents/DSP1053_1.1.0a.pdf
Buyya, R., Broberg, J., & Goscinski, A. (2011). Cloud Computing: Principles and Paradigms. Cloud Computing:
Principles and Paradigms. John Wiley and Sons. Retrieved from http://books.google.pt/books?id=S1NvRRd77rQC&lpg=PT18&ots=HSi9o6Zo0g&dq=Cloud Computing: Principles and Paradigms&lr&hl=pt-BR&pg=PT23#v=onepage&q=Cloud Computing: Principles and Paradigms&f=false
Catteddu, D., & Hogben, G. (2009). Benefits, risks, and recommendations for information security. Computing, 72(1), 2009–2013. http://doi.org/10.1007/978-3-642-16120-9_9
Chen, Y., Paxson, V., & Katz, R. (2010a). What’s new about cloud computing security. of California, Berkeley Report
No. UCB/. California. Retrieved from
http://www.utdallas.edu/~muratk/courses/cloud13s_files/what-is-new-in-cloud-security.pdf
Chen, Y., Paxson, V., & Katz, R. (2010b). What’s new about cloud computing security. … of California, Berkeley
Report No. UCB/ …. Retrieved from
http://www.utdallas.edu/~muratk/courses/cloud13s_files/what-is-new-in-cloud-security.pdf
Cloud, G. (2014). Google Compute Engine Service Level Agreement ( SLA ). Retrieved from https://cloud.google.com/compute/sla
CSA Cloud Security Alliance. (2011). Security Guidance for Critical Areas of Focus in Cloud Computing V3.0. Cloud
Security Alliance, 3, 155. http://doi.org/10.1016/S1353-4858(99)90042-9
CSA Cloud Security Alliance. (2015). CTP Data Model and API, rev. 2.13, (October). Retrieved from https://downloads.cloudsecurityalliance.org/assets/research/cloudtrust-protocol/CTP-Data-Model-And-API.pdf CSMIC. (2014). Service Measurement Index Introducing the Service Measurement Index ( SMI ), (July), 1–8.
Retrieved from http://csmic.org/downloads/SMI_Overview_TwoPointOne.pdf
Dekker, M., Liveri, D., & Lakka, M. (2013). Cloud Security Incident Reporting - Framework for reporting about
major cloud security incidents. European Union Agency for Network and Information Security.
http://doi.org/10.2788/14231
Dimitra, L. (ENISA). (2015). Cloud Security Guide for SMEs. (E. U. A. for N. and I. S. (ENISA), Ed.). http://doi.org/10.2824/508412
ETSI. (2013). Cloud Standards Coordination Final Report. European Telecommunications Standards Institute (ETSI)
for the European Commission, (November), 59.
European Commission. (2014a). Cloud Service Level Agreement Standardisation Guidelines, 1–41. European Commission. (2014b). Establishing a Trusted Cloud Europe. http://doi.org/doi:10.2759/44445
Giles Hogben, M. D. (2012). A guide to monitoring of security service levels in cloud contracts. ENISA Europe. Retrieved from http://www.enisa.europa.eu/media/press-releases/procure-secure-enisa2019s-new-guide-for-monitoring-cloud-computing-contracts
Google Cloud Plataform. (2015). Google Cloud Platform Terms of Service. Retrieved from https://cloud.google.com/terms/
Hoehl, M., & Pelaez, M. H. S. (n.d.). Proposal for standard Cloud Computing Security SLAs - Key Metrics for Safeguarding Confidential Data in the Cloud.
IBM. (2014). IBM Cloud Services Agreement IBM Cloud Service Description : IBM Bluemix. Retrieved from http://www-03.ibm.com/software/sla/sladb.nsf/pdf/6605-01/$file/i126-6605-01_06-2014_en_US.pdf
ISACA. (2014). Controls and Assurance in the Cloud : Using COBIT-5. Retrieved from www.isaca.org/controls-and-assurance-in-the-cloud
16ª Conferência da Associação Portuguesa de Sistemas de Informação (CAPSI’2016) 24 November 27, 2015, from http://www.nist.gov/customcf/get_pdf.cfm?pub_id=909494
Liu, F., Tong, J., Mao, J., Bohn, R., Messina, J., Badger, L., & Leaf, D. (2011). NIST Cloud Computing Reference Architecture. Retrieved November 27, 2015, from http://www.nist.gov/customcf/get_pdf.cfm?pub_id=909505 M. Kanchana, Sk. Nazar Hussain, Kumar, M. K., & Praveen, C. (2013). Preserving Audit of Secure Data Storage
Services in Cloud Computing. International Journal of Advanced Research in Computer Science, 4(5), 70–73. Retrieved from http://www.ijarcs.info/?wicket:interface=:3::::
Management Task Force, I. (DMTF). (2015). Cloud Audit Data Federation - OpenStack Profile, 1–60. Retrieved from https://www.dmtf.org/sites/default/files/standards/documents/DSP2038_1.0.0.pdf
Meegan, J., Singh, G., Woodwar, S., Venticinque, S., & Rak, M. (2012). Practical Guide to Cloud Service Level Agreements version 1.0. Cloud Standards Customer Council, 1–44. Retrieved from http://scholar.google.com/scholar?hl=en&btnG=Search&q=intitle:Practical+Guide+to+Cloud+Service+Level+Ag reements#0
Mell, P., & Grance, T. (2011). The NIST Definition of Cloud Computing Recommendations of the National Institute of
Standards and Technology. National Institute of Standards and Technology, Information Technology Laboratory
(Vol. 145). http://doi.org/10.1136/emj.2010.096966
Myerson, J. M. (2013). Best practices to develop SLAs for cloud computing Develop a standard way to create service level agreements that multiple partners can use, 1–9. Retrieved from http://www.ibm.com/developerworks/cloud/library/cl-slastandards/cl-slastandards-pdf.pdf
National Institute of Standards and Technology. (2013a). NIST Cloud Computing 6 Security Reference Architecture. Retrieved November 27, 2015, from http://bigdatawg.nist.gov/_uploadfiles/M0007_v1_3376532289.pdf
National Institute of Standards and Technology. (2013b). Security and Privacy Controls for Federal Information Systems and Organizations. Retrieved November 27, 2015, from http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf
National Institute of Standards and Technology. (2015). Cloud Computing Service Metrics Description. Retrieved November 27, 2015, from http://www.nist.gov/itl/cloud/upload/RATAX-CloudServiceMetricsDescription-DRAFT-20141111.pdf
Networkworld. (n.d.). Retrieved from http://www.networkworld.com/article/2288002/cloud-computing/10-most-powerful-paas-companies.html
Zhu, Y., Hu, H., Ahn, G.-J., & Yau, S. S. (2012). Efficient audit service outsourcing for data integrity in clouds.