The thesis is part of the CLEEN SHOK Smart Grids and Energy Markets project and studies the information security of the Smart Grid demonstration environment. The thesis examines information security in the Smart Grid demonstration environment at the Tampere University of Technology (TUT) and is part of the Smart Grid for Energy Market (SGEM).
Landscape
For example, each laser printer leaves a unique trace that can be used to trace the owner of the printer if necessary. An important part of the Smart Grid will be the new technological solution that can be used to improve the system.
Definition and objectives
The two most important information security subsystems are the power and ICT systems. In ICT systems, information security focuses on ensuring the confidentiality, integrity and availability (CIA) of the system.
![Figure 2.1. The building blocks of information security in automation [10].](https://thumb-eu.123doks.com/thumbv2/9pdfco/1890652.266818/20.892.177.790.256.506/figure-building-blocks-information-security-automation.webp)
Special information security features of Smart Grid
The objectives of information security for the Smart Grid are to ensure the availability of the grid and to ensure the integrity and confidentiality of the information. These goals identify the particular structure of the Smart Grid: availability stands for the needs of the automation system, integrity for the ICT system and confidentiality for the customer-oriented system.
Threats
Attacks
Legal attacks are fundamentally different from others in that their idea is not to exploit a flaw, or even try to find one. The idea is to put doubt in the minds of the judge and jury that security is not perfect, and use that observation to prove the client's innocence.
Adversaries
The third attack group is the most mysterious, and also the most dangerous - the government. Since there is only one port of interest - port 4850 - the fuzz testing concentrates on this port.
![Table 2.1. The list of adversaries that NIST – SGWC introduces [13, p. 20].](https://thumb-eu.123doks.com/thumbv2/9pdfco/1890652.266818/24.892.180.789.144.555/table-list-adversaries-nist-sgwc-introduces-p.webp)
Vulnerabilities
Security measures
Cryptography, identification and authentication
The idea of hybrid cryptography is that the sender encrypts the message with some random symmetric key. Now, however, the sender encrypts the message with his private key, and the recipient decrypts the message with the sender's public key.
Technical solutions and methods
The certificates are issued to users by a CA, which could be a private company, for example. Certificates are used to authenticate network access and are more secure than password-based authentication methods.
Security testing techniques
Code is difficult to test from the outside, and for this reason there are various tools to test them. This model is used together with the TUT demonstration environment to find out the domains and actors involved.
The landscape
Understanding the idea, and especially the structure and building blocks of a smart network, is important for understanding the risks in information security. A conceptual model based on NIST/SGWC guidelines is presented to assist in the analysis and discovery of the smart grid environment.
Infrastructure and architecture
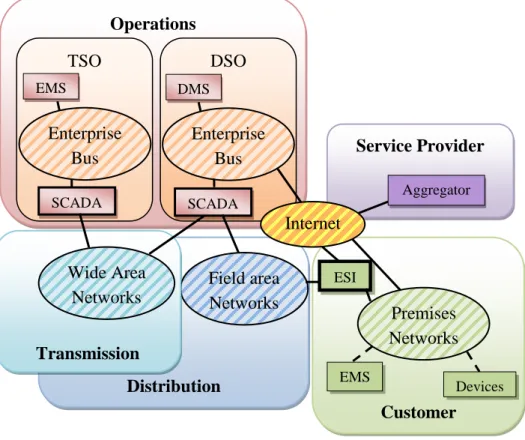
As a whole, the Smart Grid architecture will bring flexibility and in some ways has great similarity with the architecture of the Internet. The high-level view of the information network for the Smart Grid is shown in Figure 3.3.
![Figure 3.2. The architecture of the old electric grid and the new Smart Grid [40].](https://thumb-eu.123doks.com/thumbv2/9pdfco/1890652.266818/34.892.178.782.108.397/figure-architecture-old-electric-grid-new-smart-grid.webp)
Benefits
Players
For example, the TSOs of the Scandinavian countries are Statnett SF (Norway), Svenska Krafnät (Sweden), Fingrid (Finland) and Energinet.dk (Denmark).[44; 45]. 42.] The three main players in the Nordic manufacturing markets are Fortum in Finland, Vattenfall in Sweden and Statkraft in Norway [45].
The conceptual model
Domains and actors
The Bulk Generation domain is electrically connected to the Transmission domain and interfaces with the Operations, Markets and Transmission domains. The customer domain is electrically connected to the distribution domain and communicates with the Operations, Markets, Service Provider, and Distribution domains.
![Figure 3.5. The top-level view of conceptual model of Smart Grid [49, p. 35].](https://thumb-eu.123doks.com/thumbv2/9pdfco/1890652.266818/40.892.176.807.427.825/figure-level-view-conceptual-model-smart-grid-p.webp)
Differences between North America and Europe
Smart Grid demonstration environment
Use cases
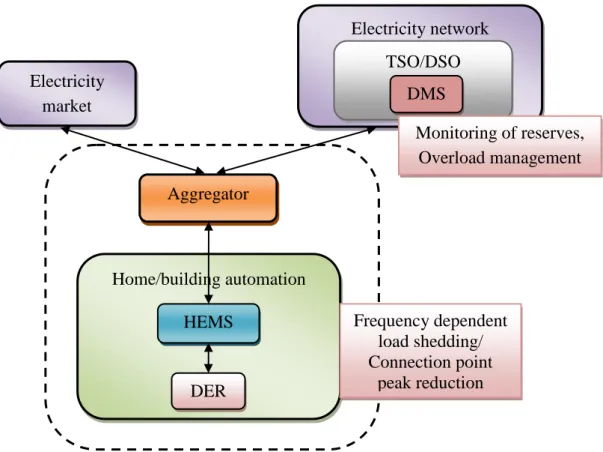
However, real-time monitoring of reserves is not necessary, as resource capacity can be predicted statistically. Many automatic backups can also be operated based on local measurements and real-time communication with the TSO control center is not necessary. Congestion management is a control center function implemented, for example, in DMS, which receives real-time measurements via the ICT system.
The domains, actors and players
The domains of the previously introduced use cases include customer, service provider, operations, transmission, and distribution. Starting from the equipment, there are the manufacturers of the HEM system, aggregator, SCADA, DMS, EMS and home devices. The players of the lab demonstration environment are: ABB in domain Operations, NSN in domain Service Provider, There in domain Customer, TUT in domain Service Provider and customer in domain Customer.
Laboratory demonstration equipment
54.] But one thing all these stakeholders have in common is that if the Smart Grid doesn't work, it will affect everyone. Therefore, it is a common business benefit for everyone to ensure that the Smart Grid works in all conditions. This chapter presents the concept of threat modeling and applies it to the TUT Smart Grid environment.
The scope and limitations
Threat modeling is a technique that helps to think about the security threats that the system may face. Today, threat modeling begins with a planning process, where threats are identified and appropriate countermeasures are implemented. The basic idea behind threat modeling is the idea that every system has something worth protecting.
Viewing the system as an adversary
Entry and exit points
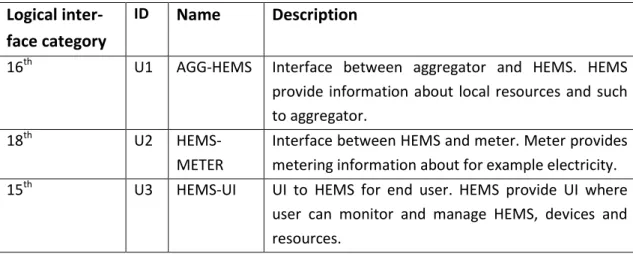
The above Table 4.1 describes the logical interface categories, identifications, names and descriptions of the interfaces. This means that the physical security of ThereGate is left, at least in part, to the customer's responsibility. The availability of the information is important, but not critical, as alternative means of obtaining the information can still be used.
The assets
This is quite sensible as wrong or incorrect information would eventually cause the system to operate incorrectly. In fact, the feeling of security can be one of the greatest assets that the end users have. The loss of trust in the system can lead to many problems, for example avoidance of using the equipment, which can lead to the failed implementation of Smart Grid.
Characterizing the system
Implementation of the system
There are many ideas and plans on how to implement a Smart Grid information infrastructure. Since the HEMS will be on the customer's premises, wired solutions such as cable or fiber optics provide a natural way to connect the HEMS to other components of the Smart Grid system. Smart Grid implementation in such environments can be done by using an already existing network structure or by e.g.
Determining threats and vulnerabilities
HEMS crashes
But also with the Smart Grid, the information is first collected from all apartments and then forwarded, even with GPRS technology. In any case, the information is sent over the same cable or fiber that the Internet uses. Of the reasons that can cause the HEMS to be unavailable, the DoS attacks are the most important to address.
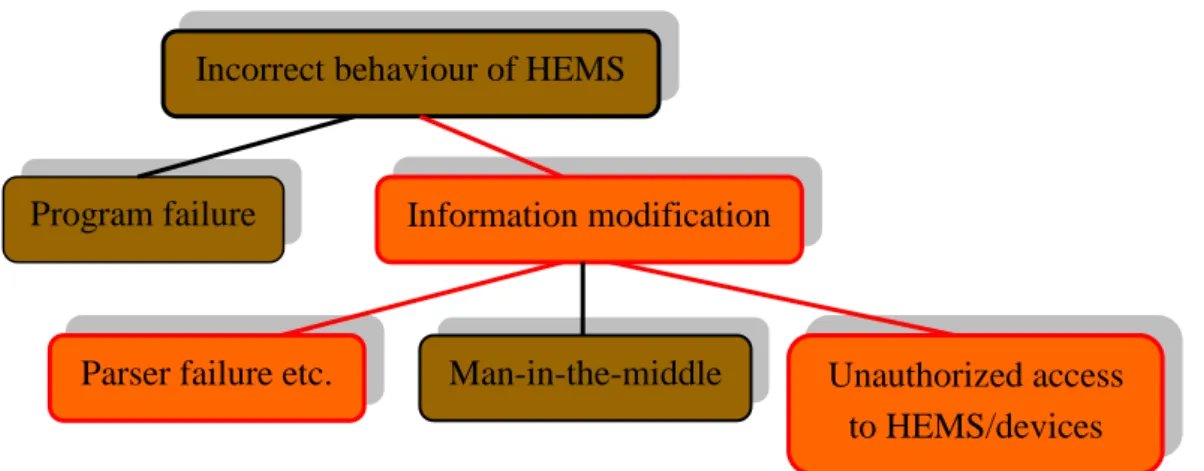
HEMS works incorrectly
One of the biggest threats to the system is HEMS being accessed by an unauthorized person. In the long run, even the most conscientious people will violate company safety instructions and procedures. For example, if certificates are used, the most difficult problem to solve is secure key management.
HEMS losses sensitive information
For example, with a Quad Pentium II 400 MHz, any possible seven-character password can be tried in 480 hours using the L0phtcrack program. Even users who are more aware of information security can be used to penetrate the system. There are solutions to make using a password more secure; this can be done, for example, by locking the system after a certain number of bad passwords.
Components
ThereGate
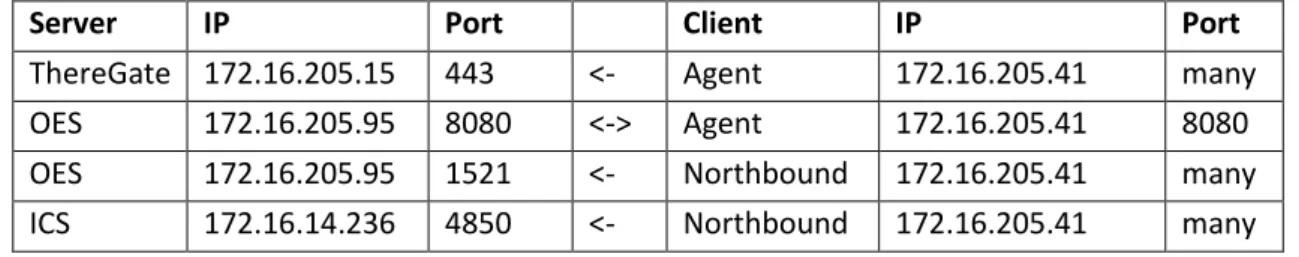
Connections to the agent and the graphical user interface are made using the Hypertext Transfer Protocol (HTTP) API. This means that the agent has to initiate communication, and ThereGate cannot send anything to the agent spontaneously. Therefore, a time-based communication structure is needed; Every minute, the agent requests real-time raw data from ThereGate using a GET request.
Aggregator
When registration is complete, the agent starts sending SOAP requests to MF and works as a WS client. However, there is no specific authentication for Agent; the agent ID is the IP address and the agent key is assigned by the OES. On the agent side, the connection is made using MF, which acts as an intermediary, so the agent does not have to worry about the OES structure.
Industrial control system
The UA client was built using the open source OPC client from the Prosys OPC UA Java SDK. Since OES is already developed software, it is difficult to ask for more specific information about its architecture and blog construction. The OPC UA wrapper is already developed, and the main focus from a presentation point of view is the interface between OES and ICS.
Information security analysis
Vulnerabilities in hardware
In addition, in the case of a demonstration, the entire ICS system only works on one and the same computer (PC), which may not be valid in a real Smart Grid environment. For example, these are cold boot attacks, where encryption keys are retrieved from the operating system after a cold reboot to restart the computer [66]. In the demonstration environment, software such as OES and ICS will demand a lot from the PC on which they run.
Vulnerabilities in software
Vulnerabilities in protocols and communication technologies
However, there are vulnerabilities such as buffer overflows in many sold SHHs, especially in the older SSH1 version. In the demo environment, neither authentication nor encryption is used in the OPC UA protocol. In the analysis part, the most critical interfaces of the system are found, while in the test part, interfaces will actually be tested and the results analyzed.
Test case analysis
- Customer owns ThereGate
- ISP owns ThereGate
- DSO owns ThereGate
- Conclusion
One of the most popular targets in the system is the OES database, as it contains all user data. Moreover, in the current version of the demo system, the information from ThereGate is not validated at any stage of the system. However, when the ISP is in charge of There-Gate's information security, it will be more secure than it would be on average in the hands of the end user.
Testing plan
- Target and layout
- Used tools
- Testing methodology
- Execution of testing
Nessus is free for personal use only (HomeFeed) and can be downloaded from www.tenable.com. As can be seen, the test tools cover the different layers of the OSI model quite well. An important factor in information security is to pay attention to the versions of software used in the system.

Testing results
- Open ports and services
- Version of software
- Software configuration
- Information disclosure
- Protocol flaws
- Encryption of information
- Authentication
- Other found issues
- Synopsis of the test results
ThereGate is one of the system's most important pieces of equipment, as it is the customer's interface to the system. An important factor for information security is to be aware of the versions of software used in the system. These flaws can be used to gain complete access to ThereGate, which violates all of the CIA's goals.
Customer Domain – HEMS/Home automation
Available from: http://www.euractiv.com/energy-efficiency/smart-grids-could-save-europe-52bn-news-499738. Available from: http://www.nist.gov/public_affairs/releases/upload/smartgrid_interopera bility_final.pdf. Available from: http://www.sans.org/reading_room/whitepa pers/wireless/security-vulnerabilities-wireless-lan-technology_1629.
Available from: http://www.imperva.com/resources/adc/pdfs/the_untold_tale_of_database_communication_protocol_vulnerabilities.pdf. Available from: http://www.sans.org/reading_room/whitepapers/authentication/two-factor-authentication-choose-one_33093.

![Figure 3.1. High level picture of communication and power layers [38].](https://thumb-eu.123doks.com/thumbv2/9pdfco/1890652.266818/32.892.178.809.551.973/figure-high-level-picture-communication-power-layers.webp)
![Figure 3.3. The information network of the Smart Grid [35, pp. 16-18].](https://thumb-eu.123doks.com/thumbv2/9pdfco/1890652.266818/34.892.179.655.664.960/figure-information-network-smart-grid-pp.webp)
![Figure 3.4. The top-level view of conceptual model of Smart Grid [35, p 22].](https://thumb-eu.123doks.com/thumbv2/9pdfco/1890652.266818/38.892.176.662.104.467/figure-level-view-conceptual-model-smart-grid-p.webp)