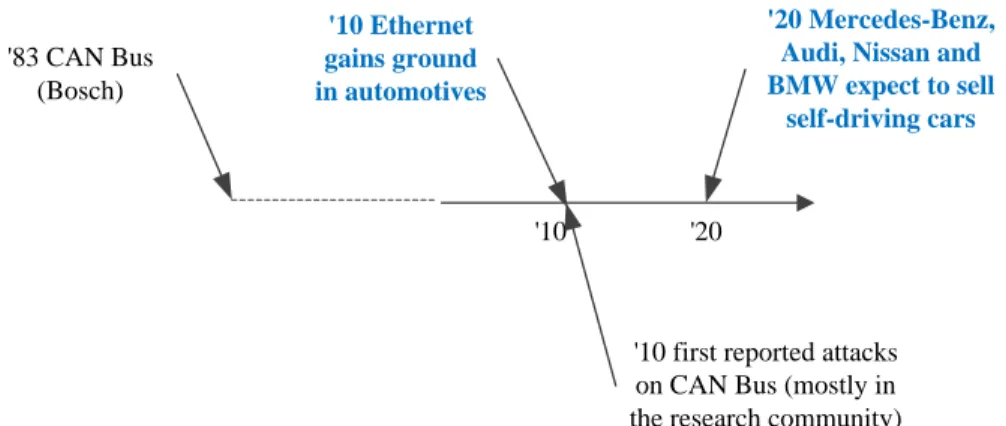
The thesis deals with our research between 2010 and 2015 at the Polytechnic University of Timisoara, focusing on the design of cryptographic protocols to ensure security on vehicle buses (e.g. CAN bus) and various automotive components or functionalities (e.g. tire pressure). surveillance sensors, vehicle access control with smartphones). I am grateful to all of the above for allowing me to work with them.
Research results in automotive security
Designing security for wireless tire pressure monitoring systems (TPMS) for vehicles has been a topic we have been following since 2010, when the first attacks were reported. Recently (May 2015) I was invited to present our work at an industry conference in Vienna, held by Vector GmbH (a top manufacturer of diagnostics and simulation tools).

Research results in other areas of cryptography and systems security
This line of research was started in collaboration with Marius Minea (UPT) in the framework of the AVANTSSAR and SPaCIoS FP7 research projects. Attack traces like the one in Figure 1.3 can then be found by the model checker.
![Figure 1.2 shows a graphical depiction of the approximate bounds compared to the tight bounds of the previous two theorems and the bounds in [78]](https://thumb-eu.123doks.com/thumbv2/pdfplayerorg/203362.39595/15.918.135.795.81.381/figure-graphical-depiction-approximate-bounds-compared-previous-theorems.webp)
In-vehicle connectivity (networks)
Cars are no exception, and all security issues stem from the communication interfaces, i.e. the in-vehicle network. CAN (Controller Area Network) is the driving force behind most existing networks in vehicles.
Challenges, why is it difficult to design in-vehicle security?
The latest high-end automotive devices have two 32-bit cores running at 100–300 Mhz (eg the Infineon TriCore TC1797 and its siblings are a well-used microcontroller in the automotive industry [39]), but this never happens. that such devices are the only devices in cars and the presence of low-cost devices with a single 8 or 16 bit core operating at 20-40 Mhz should always be expected (e.g. Freescale S12X is an important example from the automotive industry [ 22 ]). There is no doubt that sooner or later the automotive industry will open up at least some of their specifications.
State-of-the-art, overview of recent proposals
- Generic Description of the Protocol
- Efficiency parameters
- Practical versions of the scheme
- Synthetic efficiency evaluation
We now list some of the recent proposals (part of this synthesis is also present in one of our publications [30] but here we update it according to the most recent progress, including some results from [95]). Our personal contribution consists of designing the protocols presented in the thesis. The efficiency of the protocol can be evaluated with respect to memory, CPU and bandwidth.
This evaluation has to be done during the entire time period of the protocol, which can be divided into two parts: the initialization time Tini and the execution time Trun.
![Figure 2.6: MSE separation values with a first transceiver fingerprint from 2 × 10 4 values (as de-picted in [60])](https://thumb-eu.123doks.com/thumbv2/pdfplayerorg/203362.39595/31.918.116.801.87.225/figure-mse-separation-values-transceiver-fingerprint-values-picted.webp)
One-time signature based schemes
The employed signature schemes: a Merkle based scheme and HORS
The generic principle behind both one-time signature schemes is to apply a simple on-way function, say a hash function, to an input playing the role of a secret key and use the output as a public key. Ver is a deterministic algorithm that takes as input the signature and public key and outputs message m = mµ..m2m1 if and only if ∀i = 1.µ, fλ−mi(si) = fλ(ui), fmi(si ) = fλ(vi)or⊥other. Sign is a deterministic algorithm that takes the private keypv and messagem as inputs, then calculates h = hash(m) and splits h into k substrings h1, .., hµ each of the log2(t) bits and outputss = (sh1, . ., shµ)(where Eachhi is interpreted as an integer index), .
Ver is a deterministic algorithm that takes as input the signature s, the public key pb and messagem, then outputs 1 if and only iff(s0i) =vivir each extracted as integer index from h(m).
The broadcast protocol
Initialization: Gets the sender's initialization information, i.e., kn, discovery interval, and public key. Message Verification: RrunsVer(pki, sigi) for any valid public key and considers any output other than ⊥ to be authentic. 2.Authentic transmission: S sends at any time in [tstart+i·δ, tstart+ (i+ 1)·δ−ξ]malong message with its signature calculated with HORS keeping as secret key input the keys from the current discovery interval0 ,ki1, . .,kil(the number of signed messages in each time interval depends on the security level and signature parameters);.
4. Message Verification: RrunsVer(pki, sigi) for any signature received in the correct time interval and any input that is correctly verified is considered authentic.
Efficiency analysis and comparison
Obtaining keys and commitments: R receives ki and checks if (ki) = ki−1 and discards it otherwise. Any public key for which a valid MAC key exists and can verify is considered authentic, 4. 3. Key discovery: Sends at timetstart+i·δ all keys from the current interval that were not discovered as HORS signature (to to save some bandwidth, sending these keys can be skipped since recipients can validate future signatures with previously received keys, but note that this will increase verification time at the receiver).
3. Receive keys and commitments: R receives keys kji and checks if f(kj−1i ) = kji, otherwise discards it.
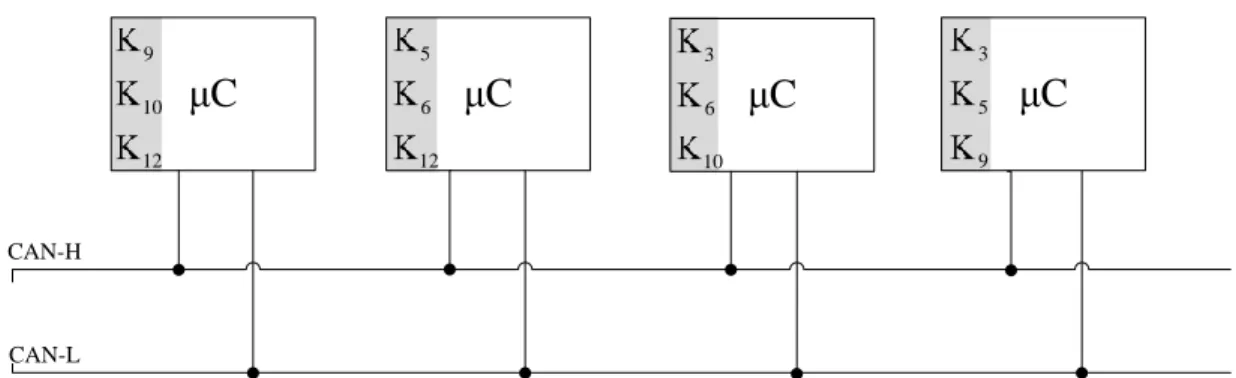
Group keying (LiBrA-CAN)
Assumptions and goals
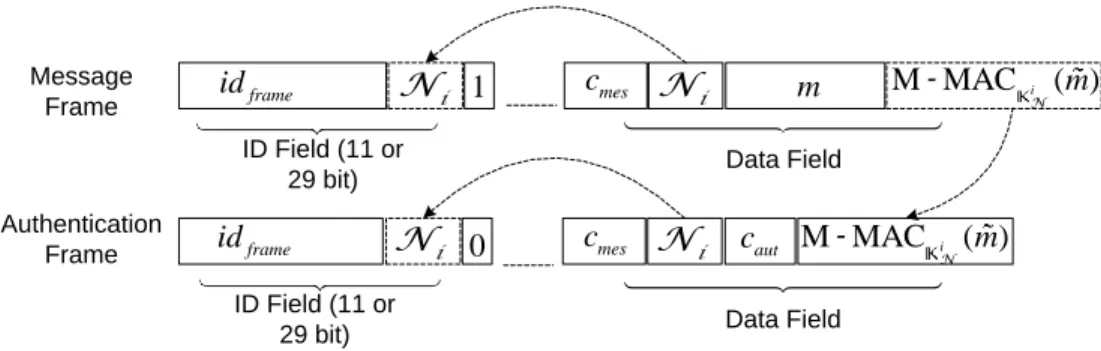
N(m).e Additionally, in the case of authentication frames, a new countercaut specifies the number of the authentication frame (calculated for protocol variants where there is more than 1 authentication frame for a message). In the experimental results from [30], we used separate authentication frames with CAN-compatible boards, while in the CAN-FD simulation from CANoe, the data frames also carry the authentication tag (allowing immediate authentication). For this reason, we work with counters as explicitly shown in the frame structure.
In the main scheme, we use Mixed Message Authentication Codes (M-MACs), which combine multiple MACs into one.
LiBrA-CAN - the main scheme
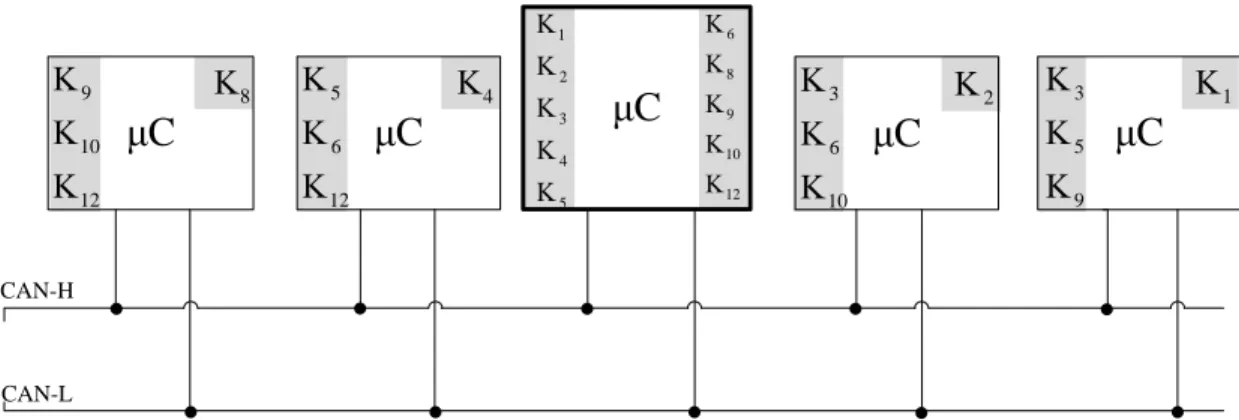
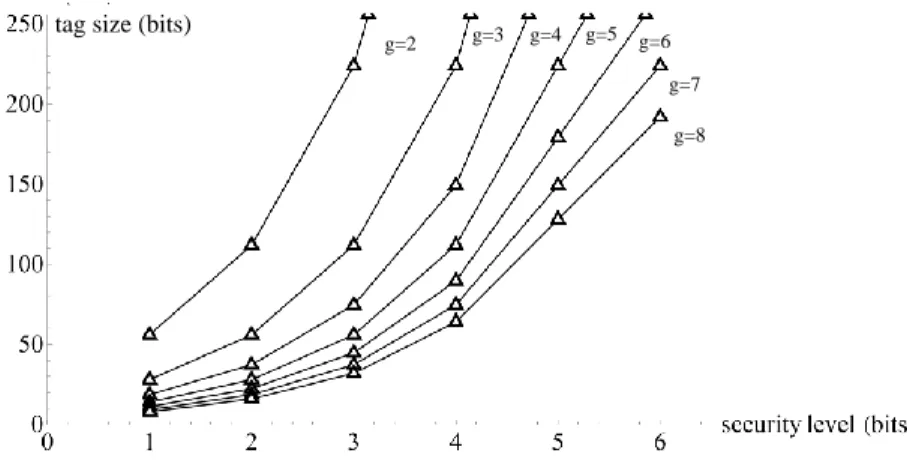
If the tag is correct for all keys in the common key set, i.e. Ki,j, then messageme is considered authentic and the message counter is updated. But if we share the keys between groups of size g, then each node owns n−1g−1. In contrast, in the case of groups of size g = 2, there are 64 bits for each node; even if there is 1 bad node, 54 bits still remain untouched (although this is not much, it may be enough for real-time protection).
Obviously this grows exponentially, but at smaller g's the number of keys is decent and provides huge security benefits.
Variations of the main scheme
While this introduces an additional delay δ, similar to the case of the TESLA protocol, this delay can be chosen as small as necessary to cover the application's requirements. Unlike the TESLA protocol, the delay is not strongly limited by external parameters (such as oscillator accuracy, synchronization error, bus speed, etc.). In such a case, a load-balanced version of the scheme can be used, in which the master communication supervisor can send a flag (verified along the message) indicating a specific slave device(s) that will perform additional authentication.
In this case, each node can start broadcasting by sending a tag that includes only part of the keys for the subgroups of which it is a part and a second node (pointed out by some flag, or predefined in protocol actions ) continue with the verification.
Proposed protocols, a comparison
- Revisiting protocols from a keying perspective
- Overview of experimental results
- Analysis of previous proposals
- Protocol design (LiMon)
- Overview of experimental results
In any case, the patent shows that the industry is aware of the problem and the solution can be seen as an improvement on the no-security option. The same ambiguities are in describing the exact level of security expected, i.e. size of the secret seed, CRC polynomial, etc. This only entails a small computational cost of the order of an additional coding and can be easily built upon the primitives we deploy for the rest of the protocol.
The main purpose is to ensure privacy for the user, e.g. the ID of the sensors is hidden and therefore cannot be detected (this is the motivation of.
Smartphone based car access via NFC
System overview and protocol design
Our initial choice was to rely on a visual channel using a master reset key stored as a data matrix on the cover of the key. This of course requires safe deposit of the token wrapper and may have some similarities to the PIN-PUK pair in mobile phones where the PUK (PIN Unlock Key) is a longer key needed to unlock the smaller PIN (Personal Identification Number) set. The list is also supplemented with the lifetime of the rights (i.e. number of attempts) and determines whether the user can further delegate part of high rights.
Haptic feedback is a response of a user's action to the token to eliminate jamming attacks (at least in part) by letting the user know if the function was correctly received by the car.
Randomness, a relapsing issue
These are all concatenated with the output of the initiation stage and feed as input to an OWF. The minimum entropy of one byte is the base 2 logarithm of the inverse of the guess probability. The size of the corrupted memory and the average entropy of each byteev are determined by experimental results.
The guess probability was calculated for each byte from the 65535 byte memory after 200 low-power conditions at four temperatures: −20◦ Celsius, 0◦ Celsius, 20◦ Celsius and 20◦ Celsius.
![Figure 4.5: Suggested handshake for rights delegation to another smartphone (based on [68]) procedure started as a joint work with George Tipa (Continental Corportation) and later a patent submission was made by Continental Corporation [88] based our resea](https://thumb-eu.123doks.com/thumbv2/pdfplayerorg/203362.39595/74.918.137.838.105.759/suggested-delegation-smartphone-continental-corportation-submission-continental-corporation.webp)
Education and research at UPT
Niels Bohr is sometimes credited with the following (humorous) remark: "Prediction is very difficult, especially about the future". For this reason let us be moderate in the prospect of the future of cars, a decade ago it would have been sufficient to have a car that ran cheaply on fuel, nowadays one wants a hybrid electric vehicle that playing favorite songs, automatically adapting the environment by recognizing the driver, teaching him about weather conditions, self-driving, etc.
Formal proofs of security
Resilience to side-channels
Challenges with key distribution
Given the current image, it is likely that PKI will return as the only viable solution for the automotive industry. But there are many reasons why a car owner might not want to receive updates. Do you still want to receive updates given the possibility that these are backdoored in case of some future cyber conflict?
These issues will not be easy to resolve, and as keys remain at the core of all security protocols, it is clear that key distribution will be a major problem for cyber-physical systems.
Challenges related to freshness
One of them is the particular long-term use of components inside the car, which is somehow incompatible with the rather short-term validity of security software, which needs to be updated and bug-fixed frequently. The software development in recent years is not very helpful as it turns out that all devices (phones, tablets, notebooks, computers, etc.) need to be patched periodically. Meanwhile, cryptographers and securitisers will publish papers that assume key distribution is a solved problem.
Contrary to the limited interest in modeling freshness for protocol security, as underlined in the previous section of our work [27], for control systems and thus car security, this objective is probably critical.
Security implications of future automotive paradigms
In Proceedings of the 11th International Conference on Cryptology and Network Security, CANS 2012, Springer-Verlag, LNCS, 2012. Kaiser, editor, Proceedings of the 4th International Workshop on Real-Time Networks (RTN05) in conjunction with the 17th Euromicro International Conference on Systems in Real Time (ECRTS05), pages 35–38. In Proceedings of the Eighth ACM Conference on Computer and Communications Security (CCS-8), pages 28–37, Philadelphia PA, USA, 2001.
In Proceedings of the 7th Australian Conference on Information Security and Privacy, ACISP ’02, pages 144–153, London, UK, 2002.
![Figure 1.3: STS and the corresponding attack trace shown by CL-Atse (based on our work from [A14])](https://thumb-eu.123doks.com/thumbv2/pdfplayerorg/203362.39595/17.918.113.785.87.515/figure-sts-corresponding-attack-trace-shown-atse-based.webp)
![Figure 1.5: Clock offsets for: a) Samsung Google Nexus S; b) Motorola Motoluxe; c) Samsung Galaxy Mini S5570; d) two Samsung I9000 Galaxy S (based on our work from [A16])](https://thumb-eu.123doks.com/thumbv2/pdfplayerorg/203362.39595/18.918.285.639.490.697/figure-offsets-samsung-google-motorola-motoluxe-samsung-samsung.webp)
![Figure 1.6: The clock skew recorded on 3 different access points (based on our work from [A16])](https://thumb-eu.123doks.com/thumbv2/pdfplayerorg/203362.39595/18.918.272.649.813.921/figure-clock-skew-recorded-different-access-points-based.webp)

![Figure 2.7: MSE separation values with a sec- sec-ond transceiver fingerprint from 2×10 4 values (as depicted in [60])](https://thumb-eu.123doks.com/thumbv2/pdfplayerorg/203362.39595/31.918.108.803.276.449/figure-mse-separation-values-transceiver-fingerprint-values-depicted.webp)
![Table 2.1: Identification rates for TJA1054T nodes with ID set to 0x000 (as depicted in [60]) Target T 1 USB T 1 USB T 2 USB T 2 USB T 3 USB T 3 USB T 4 USB T 4 USB T 5 USB T 5 USB](https://thumb-eu.123doks.com/thumbv2/pdfplayerorg/203362.39595/32.918.181.742.124.363/table-identification-rates-tja-nodes-depicted-target-usb.webp)