Proposed protocol for secured multi path routing in ad hoc networks
Texto
Imagem
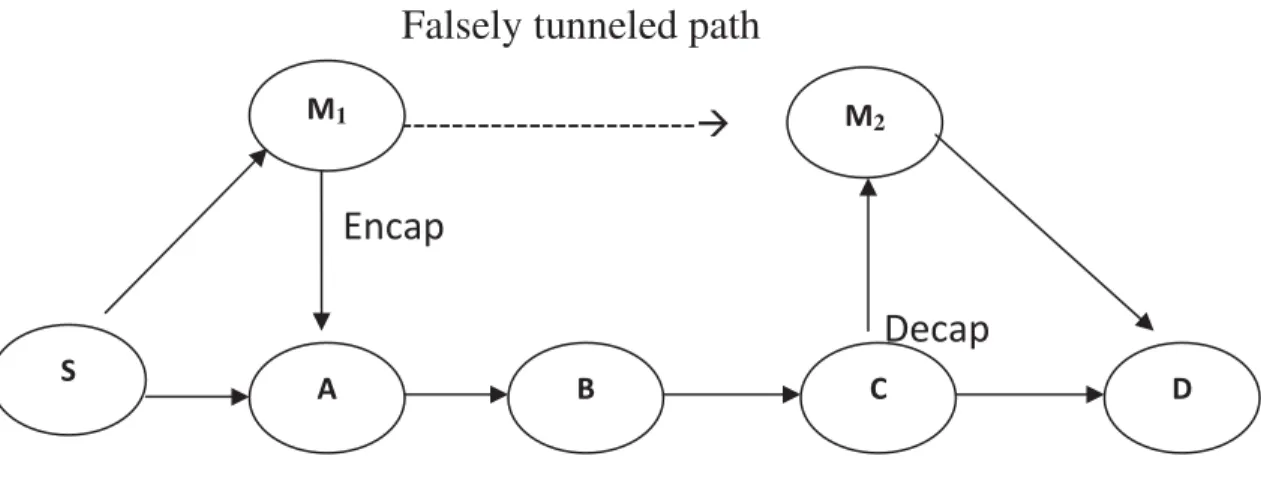
Documentos relacionados
Source peer s, once gathering swarm agent RCSA, updates the secretion table with the pheromone indicator value g ni of every relay hope peer ni which
Topology Based routing approach has Route instability, this is because an established route consists of a set of nodes between the source and the destination that are affected
They used a simple mobility scenario (random waypoint model) and a small number of network-centric metrics, such as the packet delivery ratio and the routing
To address the problem of achieving both efficient load balancing and energy efficiency we design and proposed novel algorithm called EELAR (energy efficient load aware
So, i propose a simple heuristic, called fixed RTO, to distinguish betien route loss and network congestion and thereby improve the performance of the routing algorithms.. The
Since the network relies on multi-hop transmissions in its communications, new challenges are derived to determine the multi-hop route over which data packets
if timeout period of sender node is x then timeout period of receiver node will be (x-m), where m will be critical factor. This factor [16] helps us to control the
In Case 1, i,e., for high level of security ( sec_ level = 1), during routing process, the source and destination nodes separately verify the authenticity of all other nodes in