Int ernat ional journal of Comput er Science & Network Solutions De c.2015 -Volume 3 .No.12
htt p:/ / ww w.ijcsns.com ISSN 2345 -3397
Abstract
In this article the use of Simulated Annealing (SA) algorithm for creating a consistent intrusion detection system is presented. The ability of fuzzy systems to solve different types of problems has been demonstrated in several previous studies. Simulated Annealing based Fuzzy Intrusion Detection System (SAF-IDS) crosses the estimated cognitive method of fuzzy systems with the learning capability of SA. The objective of this paper is to prove the ability of SAF-IDS to deal with intrusion detection classification problem as a new real-world application area which is not previously undertook with SA-based fuzzy system. Here, the use of SA is an effort to efficiently explore and exploit the large examines space usually related with the intrusion detection problem, and finds the optimum set of fuzzy if-then rules. The proposed SAF-IDS would be capable of extracting precise fuzzy classification rules from network traffic data and relates them to detect normal and invasive actions in computer networks. Tests were performed with KDD-Cup99 intrusion detection benchmark which is widely used to calculate intrusion detection algorithms. Results indicate that SAF-IDS provides more accurate intrusion detection system than several well-known and new classification algorithms.
Keywords:Simulated Annealing, Fuzzy Systems, Fuzzy Rule Extraction, Intrusion Detection, Pattern
Classification
I. Introduction
An intrusion is defined as any set of actions that challenge to compromise the reliability, confidentiality, or disposal of a resource (R. Heady et al., 1990). An Intrusion Detection System (IDS) observers and limits user access to the computer system by applying definite rules. These rules are based on professional knowledge mined from skilled managers, who build attack situations and apply them to find system activities. The system classifies all intrusions by users and incomes or recommends essential action to stop an attack on the database.
The problem of intrusion detection has been studied widely in computer security (N.B. Idris and B. Shanmugam, 2005), and has received a lot of kindness in machine learning and data mining (S. Shamshirband et al., 2013). As argued in(N.B. Idris and B. Shanmugam, 2005), misuse detection and irregularity detection are two methods of the intrusion detection system.
Misuse detection is the capability to classify intrusions based on a known design for the hateful activity. Constructors of IDS (using misuse detection) confirm that users have the most up to date patterns, also known as signs, by sending them updates to keep against new weaknesses (M.S. Abadeh et al., 2007).
Intrusion Detection in Computer Networks using
a Fuzzy-Heuristic Data Mining Technique
Hamid Saadi, MohamadBagherKeley
Department of Computer Engineering, Islamic Azad University, Masjed-Soleiyman Branch
Masjed-Soleiyman, Iran, email: saadi.hamid@gmail.com
Department of Computer Engineering, Islamic Azad University, Dezful Branch
Int ernat ional journal of Comput er Science & Network Solutions De c.2015 -Volume 3 .No.12
htt p:/ / ww w.ijcsns.com ISSN 2345 -3397
In anomaly discovery, the system administrator defines the baseline, or normal state of the
network’s traffic load, breakdown, protocol, and typical packet size. The anomaly sensordisplays
network sections to compare their state to the normal standard and looks for irregularities (A.A.E. Ahmed and I. Traore, 2005).
Fuzzy systems based on fuzzy if-then rules have been effectively used in many applications
zones (C.C. Lee, 1990). Fuzzy if–then rules were usually increased from human specialists.
Newly, numerous approaches have been proposed for automatically producing and correcting fuzzy if–then rules without using the assistance of human specialists(H. Ishibuchi et al., 1992). One of the key challenges in structure fuzzy systems is to guarantee that it can automatically extract ideal classification rules from training data, and the mined rules should be precise and linguistically interpretable for human knowledge.
Simulated annealing is an iterative search method motivated by the annealing of metals. It was firstly projected by Metropolis et al. in 1953. The first effort to bring SA into optimization problems was by Kirkpatrick et al. in 1983, who used SA as a new optimization search example to escape local goals and optimistically meet to the global optimum. In complex combinatorial optimization problems, it is usually easy to be confined in local goals. The main objective here is to give the procedure more time to discover the search space truly. Since then, SA has been used on an extensive variety of combinatorial optimization problems and attained good results. In data mining the SA has been used for feature selection, organization, and grouping (S. Bandyopadhyay, 2005).
There are several methods for explaining intrusion detection problem. Lee built an intrusion detection model using suggestion rule and recurrent event techniques on system review data (W. Lee et al., 1998). Neural networks have been widely used to perceive both misuse and irregular designs (Z. A. Baig et al., 2013) and (C. R. Pereira et al., 2012). Some scientists have applied Artificial Resistant Systems to detect invasive performances in a computer network (D. Dasgupta
and F. González, 2002). Some other applied techniques on intrusion detection problem are text
mining systems (S. Shamshirband et al. 2013), Genetic Fuzzy Rule-Based Systems [4, 20], Agent-based systems (S. Shamshirband et al. 2013) and clustering (H. GunesKayacik et al., 2007).
In this paper, we have utilized the simulated annealing based fuzzy system to develop an intrusion detection system based on misuse detection approach. Note that, this application is the main involvement of this article. In other words, there are no earlier works about smearing simulated annealing based fuzzy system for intrusion detection problem. The use of SA in IDS is an effort to efficiently discover and activity the large search space related with intrusion detection problems. SA tries to find the best set of fuzzy if-then rules and smears them to detect normal and invasive performance in computer networks. In the rest of paper, we call our proposed algorithm SAF-IDS.
The proposed SAF-IDS has two main structures to find an best set of rules; examination to examine new and unknown sets of fuzzy if-then rules in the state space of intrusion detection problem, and misuse to make use of knowledge found at solutions before visited, to help find better set of rules. These two features are controlled by a variable called temperature and, assist SAF-IDS to achieve competitive results in intrusion detection as a high-dimensional classification problem.
Int ernat ional journal of Comput er Science & Network Solutions De c.2015 -Volume 3 .No.12
htt p:/ / ww w.ijcsns.com ISSN 2345 -3397
The rest of the paper is as follows. Sections IIand III describe the presented simulated annealing based fuzzy system for intrusion detection. Experimental results and comparison of the proposed approach with other algorithms are reported in SectionIV. Section V is conclusion.
II. Fuzzy rule base for pattern classification
Our fuzzy classifier system examines for a comparatively small number of fuzzy if–then rules with high organization capability. Since the resulting class and the confidence evaluation of each
fuzzy if–then rule can be determined from exercise patterns by a simple experiential
procedure(H. Ishibuchi et al., 1992), the duty of our fuzzy classifier system is to produce mixtures of precursor fuzzy sets for a set of fuzzy if–then rules. While this task seems to be simple at first look, in fact it is very difficult for high-dimensional pattern organization problems,
since the search space involves 6nmixtures.
In our fuzzy classifier system, the resulting Class Cj and the grade of inevitabilityCFj of each
fuzzy if–then rule are resolute by an improved version of the heuristic method which is debated
in(H. Ishibuchi et al., 1992).
A. Determination of Cj and CFj
Step 1: Compute the compatibility of each exercise pattern xp =(xp1,xp2,...,xpn) with the fuzzy if–
then rule Rj by the following product action:
1 1
(
)
(
)
. . .
(
),
j
x
p jx
p jnx
pnµ
=
µ
×
×
µ
p =1, 2,. . .,m, (1)whereµji(xpi) is the association purpose of it quality of pth pattern.
Step 2: For each class, compute the comparative sum of the compatibility marks of the training designs with the fuzzy if–then ruleRj :
( ) ( ) , 1, 2,. . .,
p
Class h j j p Class h x Class h
R x N h c
β µ
∈
=
∑
= (2)whereβClass h(Rj) is the sum of the compatibility grades of the preparation patterns in Classhwith
the fuzzy if–then rule Rj and NClass his the number of training patterns which their matching
class is Class h.
The defined adjustment of the heuristic procedure has arisen in this step, since in the technique deliberated in (H. Ishibuchi et al., 1992) the sum of the compatibility marks is intended instead of scheming the comparative sum of the grades. This is because in intrusion detection problem some of the classes are very similar to each other. Furthermore the number of training patterns for each of the classes is meaningfully different. So if we use the old-fashioned heuristic
technique of(H. Ishibuchi et al., 1992), the resulting class of Rj might be specified incorrectly.
Step 3: Find Class hˆj that has the maximum value of βClass h(Rj) :
{
}
ˆ ( ) max 1( ),..., ( ) .
j j Class j Class c j
Class h R R R
Int ernat ional journal of Comput er Science & Network Solutions De c.2015 -Volume 3 .No.12
htt p:/ / ww w.ijcsns.com ISSN 2345 -3397
If two or more classes take the supreme value, the resulting Class Cj of the fuzzy if–then rule
j R
cannot be strong-minded exclusively. In this case, let Cj beϕ. If a single class takes the
supreme value, let Cj be Classhˆj . If there is no training pattern well-matched with the fuzzy if–
then rule Rj (i.e., if βClass h(Rj)=0forh=1,2,...,c) the resulting Class Cj is also specified asϕ. Step 4: If the resulting Class Cj isϕ, let the mark of certainty CFj of the fuzzy if–then rule Rj be CFj =0. Otherwise, the grade of certainty CFj is determined as follows:
(
ˆ)
1
( ) ( )
j
c
j Class h j Class h j h
CF β R β β R
=
= −
∑
(4)Where
ˆ
( ) ( 1)
j
Class h j h h
R c
β β
≠
=
∑
− (5)The next section will discuss about the proposed simulated annealing based fuzzy system for intrusion detection.
Figure. 1. Structure of SAF-IDS (Single Winner Rule method is applied to perform the decision fusion procedure).
The technique of coding fuzzy if-then rules which is used in this article is the same as the technique which is engaged in (M.S. Abadeh et al., 2007). The following signs are used for meaning the five dialectal values: (Figure. 1) 1: small, 2: medium small, 3: medium, 4: medium large, 5: large, and 6: don't care. For example, the following fuzzy if-then rule is coded as “13426”: If x1 is small and x2 is medium and x3 is medium large and x4 is medium small and
5
x is don't care, then Class Cjwith CF =CFj.
By considering the above feature of proposed SAF-IDS, the goal classifier consists of c classifiers. The structure of the SAF-IDS is presented in Figure. 1. According to this figure the
Intrusion Detection Data Set Train Set Test Set Simulated
Annealing Best Set of Fuzzy Rules
Performance Evaluator Classifier #1
Set of rules for class #1
Classifier #2
Set of rules for class #2
Classifier #c
Set of rules for class #c
. . . Decision Fusion Detected Class Main Classifier Single Winner Rule Intrusion Detection Data Set Train Set Test Set Simulated
Annealing Best Set of Fuzzy Rules
Performance Evaluator Classifier #1
Set of rules for class #1 Classifier #1
Set of rules for class #1
Classifier #2
Set of rules for class #2 Classifier #2
Set of rules for class #2
Classifier #c
Set of rules for class #c Classifier #c
Set of rules for class #c
mixture of the gained fuzzy rule sets are used in the construction of the final classification system.
III. Simulated Annealing based Fuzzy Intrusion Detection System
Simulated annealing is an iterative search method motivated by the annealing of metals. The process can be described as follows. Primarily, a solid is heated from a high temperature and then cooled slowly so that the system at any time is approximately in thermodynamic symmetry. At symmetry, there may be many shapes with each one matching to a precise energy level. The chance of compliant a change from the current formation to a new formation is related to the difference in energy between the two states. Kirkpatrick et al. were the first to familiarize simulated annealing to optimization problems (S. Kirkpatrick et al., 1953). Since then, SA has been extensively used in combinatorial optimization problems and has attained good results on a variety of problem instances.
Presume that En and Ecdenote the new energy and current energy correspondingly. Enis always
accepted if it gratifiesEn <Ec, but if En ≥Ec the new energy level is only accepted with the
Boltzmann probability delivery as specified by:
( ) /
e
− En−Ec T (6)where T is the current temperature. Hence, worse answers are known based on the change in explanation quality which allows the search to avoid fetching ensnared at local minima. The temperature is then decreased gradually and the annealing process is frequent until no more development is reached or any conclusion standards have been met.
Outline of the SA-based intrusion detection algorithm is presented as follows:
Step 1: Generate an initial set of fuzzy if–then rules and set the temperature of system to initial
temperature. (Initialization)
Step 2: Evaluate current set of fuzzy if-then rules by Evaluation Function (EF). (Evaluation) Step 3: Generate new set of fuzzy if–then rules from initial set using one of the perturb operations. (Perturbation)
Step 4: Accept new set of rules, if EFnew <EFcurrent, else accept new set of rules with the Boltzmann
probability distribution given by (7). (Acceptance)
Step 5: Repeat step 2-4, k times at each temperature. (Iteration) Step 6: Decrease temperature using cooling rate parameter. (Cooling)
Step 7: Dismiss the algorithm if a discontinuing condition is content, otherwise return to Step 2. (Termination)
The proposed algorithm is shown in Figure. 2. Each stage of this fuzzy classifier system is designated as follows:
A. Initialization
Let Ninit denote the number of fuzzy if-then rules in the initial set. To create an initial set, one
approach is to generate Ninit fuzzy if-then rules by randomly specifying the antecedent fuzzy sets
max
Algorithm Simulated_Annealing_based_Fuzzy_ Intrusion_Detection_System // is the initial set of rules
// is the best set of rules // is the initial tem
init best S S T min perature // is the final temperature // is the cooling rate // is a constant
// is the total iterations of Metropolis so far // i
T Time k α β max
s the number of calls of metropolis at each temperature Begin
1) ; 2) ;
3) ; // is the best set of rules seen so far 4)
current init best current best
c
T T
S S
S S S
EF = = = min ( ); 5) ( ); 6) 0;
7) While ( )
8) For i=1 to 9)
urrent current best best
NNCP S
EF NNCP S
Time T T k = = = ≥
Call Metropolis( , , , , ); 10) ;
11) ; 12) ; 13) End;// While 14)
current current best best
S EF S EF T
Time Time k
k k T T β α = + = × = ×
Return ( ); End.//
best
S
Figure. 2. Procedure for SAF-IDS.
In computer simulations, we take the probability of "don't care" PDC ≥36 / 41. After generation of
init
N fuzzy if-then rules as initial set of rules Sinit, the consequent class and the certainty grade of
each are specified from training patterns by method described in previous section. The fitness value of the fuzzy if–then rule Rj is assessed by the next fitness function:
(
j)
(
j)
fitness R
=
NCP R
(7)whereN CP R( j) is the number of correctly classified training patterns by the fuzzy if-then rule
j
R .
B. Initial temperature
The SAF-IDS algorithm needs to start from a high temperature (line 1 of Figure. 2). The infection restriction is initialized using the technique described in (H. Youssef et al., 2001). Before the start of actual SAF-IDS technique, a continuous number of moves, say M, in the district of the initial set of rules are made, and the individual evaluation function values of these moves are determined. The evaluation function difference for each move i, ∆EFi, is given by
1
i i i
EF EF EF−
∆ = − . Suppose Mg and Mb be the number of good and bad moves, respectively (
g b
M =M +M ). The average ∆EFb is then given by:
1 1 Mb
b b
i b
EF EF
M =
Since we wish to keep the probability, say Pinit, of accepting bad moves high in the initial stage
of SAF-IDS, we estimate the value of the temperature parameter by substituting the value of Pinit
in the following expression derived from the Metropolis function:
max
ln( )
b
init
EF T
P −∆
= (9)
wherePinit ≈1(Pinit =0.999). C. Evaluation
The set of fuzzy if-then rules should have high accuracy. Thus we use following assessment purpose for each set:
( ) ( )
EF S =NNCP S (10)
where S is set of rules and NNCP S( ) is the number of non-correctly classified training patterns by S. NNCP S( )obtains from:
1
( ) ( )
N
j j
NNCP S m NCP R
=
= −
∑
(11)wherem is the number of all patterns in the training set and 1
( ) N
j j
NCP R
=
∑
is the number of all correctly classified training patterns by S.
D. Perturbation
The procedure of disturbing a current rule set included three purposes (line 1 Figure. 3). They are: modifying a rule in the set of rules (Modify), deleting one rule from the set of rules (Delete) and creating new rule from the rule set (Create). The three functions are described below. The above perturb functions enables the SAF-IDS to perform efficient moves in the state space.
E. Modify
A rule in the rule set is selected randomly. This rule is then adapted through altering one or more linguistic value(s) of its antecedent part. Because the search space of the problem is very complex, altering more linguistic values may cause escaping from the global optimum. Thus we set the probability of changing linguistic values for the selected rule to a very small percentage of all 41 features. The selected rule is then replaced with the adapted rule, if the resulting class of it equals to consequent class of selected rule, otherwise the modify function is repeated.
In computer simulation, the probability of changing for linguistic values in the antecedent part (
cM odify P
) has been taken 5% of all of 41 parts.
F. Delete
max
max min
( ) ( )
( )
( ) ( )
Class h
Class h Class h
fitness S fitness R
P R
fitness S fitness S
− =
− (12)
where fitnessmax(SClass h) and fitnessmin(SClass h) are the maximum and minimum fitness values of
fuzzy if-then rules in the selected class of rule set, Classh, respectively. Then, the selected rule is
deleted from the set of fuzzy if-then rules.
G. Create
The Modify trouble function allows SAF-IDS to recover a subset of rules by changing linguistic values from one of its rules, so that it will be stronger in competition with rules of other classes. The Delete function removes weaker rules in a subset of rules, which these rules may be the winner in competition with other subset of rules. Although organization rate of the reduced subset of rules may be decreased, the total classification rate will be increased. The Create trouble function enables the obtainable algorithm to escape from local goals by execution small jumps in the state space of the problem.
The core of the procedure is the Metropolis processviii, which simulates the annealing process at
aassumed temperature T (Figure. 3). At each call of the Metropolis technique one of the above
functions was randomly chosen and a new set of rules, Snew , is created from the current set of
rules,
S
current .H. Acceptance
If the value of evaluation function for the new rule set Snew is less than the value of the current
set of rules Scurrent . If the value of assessment function for the new set of rules is less than the
best set of rules
S
best seen thus far, then we also replace Sbest by Snew . If the new set of ruleshas a better value for assessment function in contrast to the current set of rules, Metropolis will receive the new set of rules on a probabilistic basis (lines 4-7 of Figure. 3).
Procedure Metropolis( , , , , )
// is the new set of rules Begin
1) ( );
2) ( );
3) ( );
current current best best new
new current new new
new current
S EF S EF T
S
S Perturb S
EF NNCP S
EF EF EF
= =
∆ = −
4) If ( 0) Then
;
5) If Then
;
EndIf 6)
current new new best best new
EF
S S
EF EF
S S
∆ < =
< =
/
Else If ( (0,1) ) Then
; 7) EndIf
End. //
EF T
current new
random e
S S
Metropolis
−∆
< =
I. Iteration
At each temperature the Metropolis technique is called a continuous number of times, k (line 8-9 of Figure. 2). A substitute is to animatedly change the number of repetitions as the algorithm progresses. At higher temperatures the number of repetitions can be less, but at lower temperatures it is significant that a large number of repetitions are done so that the local
optimum can be fully discovered. Parameter β is used for this aim (line 11 of Figure. 2). Here,
β is set equal to 1.
J. Cooling
Cooling rate parameter α, used for updating the temperature. The temperature should reduction
slowly so that the algorithm could explore the state space of the problem completely. In
computer simulation αtakes on the value of 0.97 (line 12 of Figure. 2).
K. Termination
When the temperature reaches to the final temperature the algorithm terminates. In computer simulation, Tmin is set equal to 0.0001 (line 13 of Figure. 2).
IV. Experiments using SAF-IDS
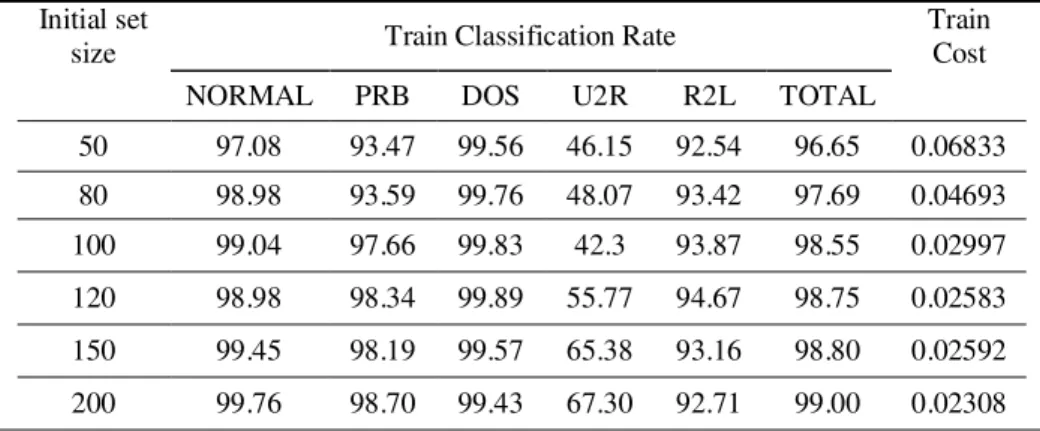
TABLE 1 shows parameter requirement that we have used in our computer simulations for SAF-IDS. The classification rate progress for total classification rate using SAF-IDS are shown in Figure. 4, respectively. The average correctness rate gained from the SAF-IDS differs from 96% to 99% with the number of rules ranging from 50 to 200. The simulated annealing based fuzzy system which extracts 120 fuzzy if-then rules from training data and obtains 98.75% accuracy rate is applied for test validation.
TABLE1:PARAMETERS SPECIFICATION IN
COMPUTER SIMULATIONS FOR SAF-IDS
Parameter Value
initial set of rules size (Ninit) 120
initial temperature (Tmax) 100
final temperature (Tmin) 0.0001
cooling rate (α) 0.97
# iteration at each temperature (k ) 200
iteration increment rate (β) 1
% of changed antecedent part for Modify 5%
% of changed antecedent part for Create 20%
probabilistically. The mentioned acceptance probability decreases according to the cooling rate factor of the SA algorithm. Therefore, the progress of classification rate might be decreased slightly specifically at the first iterations of SAF-IDS.
Figure. 4. Total classification rate progress for training data set using SAF-IDS.
TABLE 2 shows the classification rate of each partial classifier, the total classification rate, and cost of the training data set with the number of rules for initial set of fuzzy if-then rules. From this Table, we can see that the accuracy of U2R attacks is obviously low as compared with other classes. This is because some new rules of other classes that are generated by the SAF-IDS outperform U2R class rules in classifying some patterns associated with U2R class. These rules degrade U2R accuracy rate, but the overall classification rate has been increased effectively. On average, stable accuracies can be obtained using about 118 rules each of which has approximate rule length of 7.04 and the total lengths of fuzzy rules 831. The results show that increasing the number of rules may continuously improve the average accuracy and cost but the interpretability of simulated annealing based fuzzy system is reduced. Here, the proposed SAF-IDS applies accuracy based criterion to evaluate the modified rule set in each step of main algorithm. This criterion is the NNCP as mentioned in previous section.
TABLE2:CLASSIFICATION RATE AND COST FOR TRAINING DATA SET
WITH THE NUMBER OF RULES
Initial set
size Train Classification Rate
Train Cost
NORMAL PRB DOS U2R R2L TOTAL
50 97.08 93.47 99.56 46.15 92.54 96.65 0.06833
80 98.98 93.59 99.76 48.07 93.42 97.69 0.04693
100 99.04 97.66 99.83 42.3 93.87 98.55 0.02997
120 98.98 98.34 99.89 55.77 94.67 98.75 0.02583
150 99.45 98.19 99.57 65.38 93.16 98.80 0.02592
200 99.76 98.70 99.43 67.30 92.71 99.00 0.02308
V. Comparison of SAF-IDS with other algorithms
This subsection will compare the performance of the proposed simulated annealing based fuzzy intrusion detection system with other approaches in the intrusion detection problem.
0.8 0.84 0.88 0.92 0.96 1
0 20000 40000 60000 80000 100000
C
la
ss
if
ic
a
ti
o
n
R
a
te
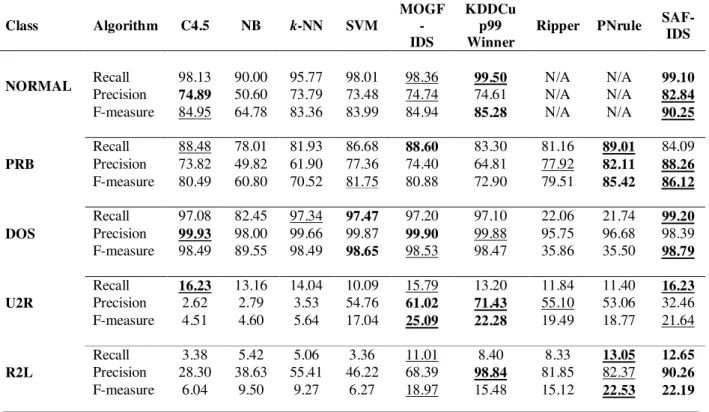
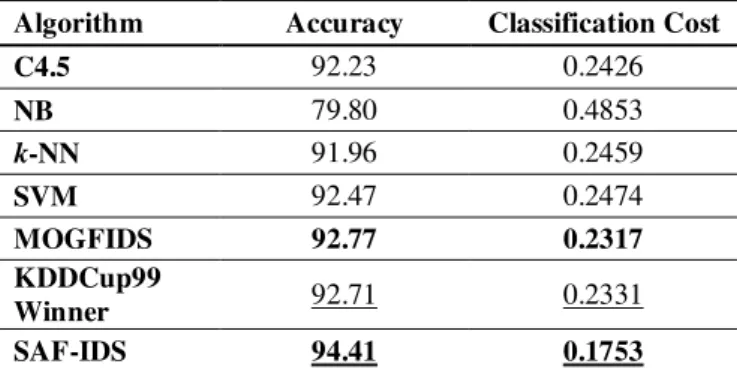
Classification presentation of SAF-IDS is restrained and associated with that of different classification procedures including pruning C4.5, Naïve Bayes (NB), k-Nearest Neighbor (k-NN), Support Vector Machine (SVM), and Multi-Objective Genetic Fuzzy Intrusion Detection System (MOGFIDS) (C.H. Tsang et al., 2007). In k-NN parameter k is fixed to 5, and the SVM is skilled using the well-known fast consecutive minimal optimization technique with a polynomial core. The results are also associated with the conqueror of KDD-Cup99 contest (C. Elkan, 2000), RIPPER and an improved PNrule(R. Agarwal and M. V. Joshi, 2001) classifier recently proposed in the literature. The results of Recall, Precision, and F-measure of diverse classifier for each class are obtainable in TABLE 3, and TABLE 4 exhibits the overall accuracy rates and classification costs of the above algorithms.
TABLE 3 shows that for normal traffic recognition, SAIDS obtains better Precision and F-measure rates than other classifier and both KDD-Cup99 Winner and SAF-IDS can achieve high recall rates. For the class of PRB attacks, SAF-IDS outperform other classifiers in terms of both Precision and F-measure. As the major class such DOS attacks, the suggested procedure can realize the highest Recall and F-measure rates. Regarding the rare classes of U2R and R2L attacks, SAF-IDS obtains better Recall for U2R attacks and also obtains competitive results for
R2L attacks in comparison with PNrule.
From TABLE 4, we can see that the SAF-IDS gain the maximum accuracy and the lowest classification cost among other classifiers. This is because the SAF-IDS explores the state space of the high-dimensional classification problem better than other algorithms and with adequate initialization, perturbation, evaluation, and acceptance tries to reach the global optimum and escape from local optima. The overall results demonstrate that SAF-IDS achieves robust performance by detecting attacks with high detection rate and recognizing normal traffic with low false positive rate.
TABLE3: RECALL, PRECISION, AND F-MEASURE FOR DIFFERENT CLASSIFIERS. THE BEST VALUES
ARE BOLD-UNDERLINED, THE SECOND ARE IN BOLD, AND THE THIRD ARE UNDERLINED.
Class Algorithm C4.5 NB k-NN SVM
MOGF - IDS
KDDCu p99 Winner
Ripper PNrule SAF-
IDS
NORMAL Recall 98.13 90.00 95.77 98.01 98.36 99.50 N/A N/A 99.10
Precision 74.89 50.60 73.79 73.48 74.74 74.61 N/A N/A 82.84
F-measure 84.95 64.78 83.36 83.99 84.94 85.28 N/A N/A 90.25
PRB
Recall 88.48 78.01 81.93 86.68 88.60 83.30 81.16 89.01 84.09
Precision 73.82 49.82 61.90 77.36 74.40 64.81 77.92 82.11 88.26
F-measure 80.49 60.80 70.52 81.75 80.88 72.90 79.51 85.42 86.12
DOS
Recall 97.08 82.45 97.34 97.47 97.20 97.10 22.06 21.74 99.20
Precision 99.93 98.00 99.66 99.87 99.90 99.88 95.75 96.68 98.39
F-measure 98.49 89.55 98.49 98.65 98.53 98.47 35.86 35.50 98.79
U2R
Recall 16.23 13.16 14.04 10.09 15.79 13.20 11.84 11.40 16.23
Precision 2.62 2.79 3.53 54.76 61.02 71.43 55.10 53.06 32.46
F-measure 4.51 4.60 5.64 17.04 25.09 22.28 19.49 18.77 21.64
R2L
Recall 3.38 5.42 5.06 3.36 11.01 8.40 8.33 13.05 12.65
Precision 28.30 38.63 55.41 46.22 68.39 98.84 81.85 82.37 90.26
TABLE4:ACCURACY AND CLASSIFICATION COST OF DIFFERENT CLASSIFIERS
Algorithm Accuracy Classification Cost
C4.5 92.23 0.2426
NB 79.80 0.4853
k-NN 91.96 0.2459
SVM 92.47 0.2474
MOGFIDS 92.77 0.2317
KDDCup99
Winner 92.71 0.2331
SAF-IDS 94.41 0.1753
According to the above discussion, it is clear that our proposed SA-based learning algorithm outperforms several other classification methods in the intrusion detection problem. By adjusting
α as the cooling rate parameter, it is possible to apply SAF-IDS on other classification problems
as well. However, it is important to note that the main disadvantage of the proposed algorithm is its high training time, which is due to the nature of Simulated Annealing Meta heuristic. The mentioned problem rises specifically by choosing higher values for the cooling rate parameter. Therefore, it is possible to accelerate the learning process of the proposed SAF-IDS by choosing faster cooling schedules for SA (I. Bezakova et al., 2006).
VI. Conclusion
In this paper, we have introduced the SAF-IDS approach for detecting intrusive behaviors in a computer network. Computer imitations on DARPA data sets determine that SAF-IDS achieves strong performance for classifying both intrusion attacks and normal network traffic.
As intrusion detection is a high-dimensional classification problem, one of the important properties of the proposed SAF-IDS in this paper is that the main classifier consists of c classifiers each belongs to a class. This feature allowed the algorithm to focus on learning of each class regarding the overall classification rate. Therefore, the simulated annealing based fuzzy intrusion detection algorithm is repeated for each of the classes in the classification problem.
The perturb functions (i.e., modify, delete, and create) of the SAF-IDS guaranteed to generate valid set of rules. To achieve this, after performing modify and create, consequent class of the each set of rules is determined. If the consequent class is the same as the parent class then the generated rule is accepted, otherwise the function is repeated.
As discussed in the paper, intrusion detection is a new real-world application area, which is not previously tackled with simulated annealing based fuzzy system. Therefore, it is important to investigate other SAF-IDS architectures with faster cooling schedules for this complex classification problem. Moreover, the use of multi-objective simulated annealing based fuzzy systems to extract an understandable fuzzy classifier for intrusion detection is another substantial investigation topic which is left for our future work.
Acknowledgment
Many thanks to the vice-chancellor of research at Islamic Azad University, Masjed-Soleiyman Branch for the financial support of this research project with title:
“Investigating the intrusion in Computer Networks and detecting the intrusion in them using a
References
i. R. Heady, G. Luger, A. Maccabe, and M. Servilla, “The architecture of network level
intrusion detection system,” Technical Report, Department of Computer Science,
University of New Mexico, 1990.
ii. N.B. Idris and B. Shanmugam, “Artificial Intelligence Techniques Applied to Intrusion
Detection,” Annual IEEE INDICON, 2005, pp. 52-55.
iii. S. Shamshirband, N. Anuar, M. L. Mat Kiah, and A. Patel, “An appraisal and design of
a multi-agent system based cooperative wireless intrusion detection computational
intelligence technique,” Engineering Applications of Artificial Intelligence, Volume 26,
Issue 9, October 2013, pp. 2105-2127.
iv. M.S. Abadeh, J. Habibi, and C. Lucas, “Intrusion Detection Using a Fuzzy
Genetics-Based Learning Algorithm,” Journal of Network and Computer Applications, 2007, pp.
414-428.
v. A.A.E. Ahmed and I. Traore, “Anomaly Intrusion Detection based on Biometrics,”
Proceedings of the 2005 IEEE Workshop on Information Assurance and Security United States Military Academy, West Point, NY, 2005, pp. 452-453.
vi. C.C. Lee, “Fuzzy logic in control systems: fuzzy logic controller, Part I and Part II,”
IEEE Transactions on Systems, Man, and Cybernetics, 20(2), 1990, pp. 404–435.
vii. H. Ishibuchi, K. Nozaki, and H. Tanaka, “Distributed representation of fuzzy rules and
its application to pattern classification,” Fuzzy Sets and Systems, 52(1), 1992, pp. 21-32.
viii. N. Metropolis, A.W. Rosenbluth, M.N. Rosenbluth, A.H. Teller, and E. Teller,
“Equation of state calculation by fast computing machines,” Journal of Chemical
Physics, vol. 21, 1953, pp. 1087-1092.
ix. S. Kirkpatrick, C.D. Gelatt, and M.P. Vecchi, “Optimization by simulated annealing,”
Science, vol. 220, 1983, pp. 671-680.
x. S. Bandyopadhyay, “Simulated Annealing Using a Reversible Jump Markov Chain
Monte Carlo Algorithm for Fuzzy Clustering,” IEEE Transactions on Knowledge and
Data Engineering, vol. 17, no. 4, Apr. 2005, pp. 479-490.
xi. W. Lee, J.S. Salvatore, and K.W. Mok, “Mining audit data to build intrusion detection
models,” In: Proceedings of ACM SIGKDD international conference on knowledge
discovery and data mining, 1998, pp. 66-72.
xii. Z. A. Baig, S. M. Sait, and A. Shaheen, “GMDH-based networks for intelligent
intrusion detection,” Engineering Applications of Artificial Intelligence, Volume 26, Issue 7, August 2013, pp. 1731-1740.
xiii. C. R. Pereira, R. Y.M. Nakamura, K. A.P. Costa, and J. P. Papa, “An Optimum-Path
Forest framework for intrusion detection in computer networks,” Engineering
Applications of Artificial Intelligence, Volume 25, Issue 6, September 2012, pp. 1226-1234.
xiv. D. Dasguptaand F. González, “An Immunity-Based Technique to Characterize
Intrusions in Computer Networks,” IEEE Transactions on Evolutionary Computation,
vol. 6, no. 3, Jun. 2002, pp. 1081-1088.
xv. C.H. Tsang, S. Kwong, and H. Wang, “Genetic-fuzzy rule mining approach and
evaluation of feature selection techniques for anomaly intrusion detection,” Pattern Recognition, Volume 40, Issue 9, September 2007, pp. 2373-2391.
xvi. H. GunesKayacik, A. NurZincir-Heywood, and M. I. Heywood, “A hierarchical
xvii. H. Youssef, S.M. Sait, and H. Adiche, “Evolutionary algorithms, simulated annealing
and tabu search: a comparative study,” Engineering Applications of Artificial
Intelligence, Volume 14, Issue 2, Apr. 2001, pp. 167-181.
xviii. J. Gomez and D. Dasgupta, “Evolving Fuzzy Classifies for Intrusion Detection,”
Proceedings of the 2002 IEEE Information Assurance Workshop, Jun. 2001.
xix. C. Elkan, “Results of the KDD'99 classifier learning,” ACM SIGKDD Explorations 1,
2000, pp. 63–64.
xx. R. Agarwal and M. V. Joshi, “PNrule: a new framework for learning classifier models
in data mining (a case-study in network intrusion detection),” In: Proc. First SIAM Conf. on Data Mining, Apr. 2001.
xxi. I. Bezakova, D. Stefankovic, V. V. Vazirani, and E. Vigoda, “Accelerating simulated
annealing for the permanent and combinatorial counting problems,” In Proceedings of