Guard against cooperative black hole attack in Mobile Ad-Hoc Network
Texto
Imagem
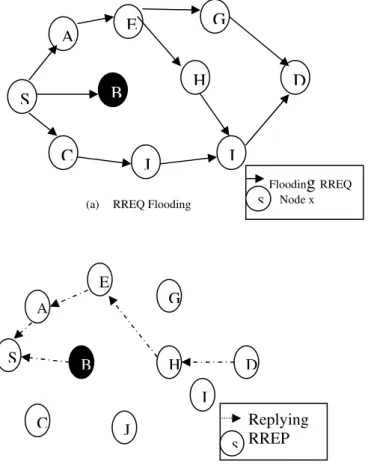

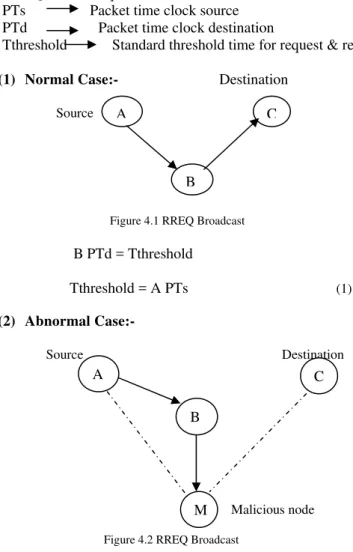
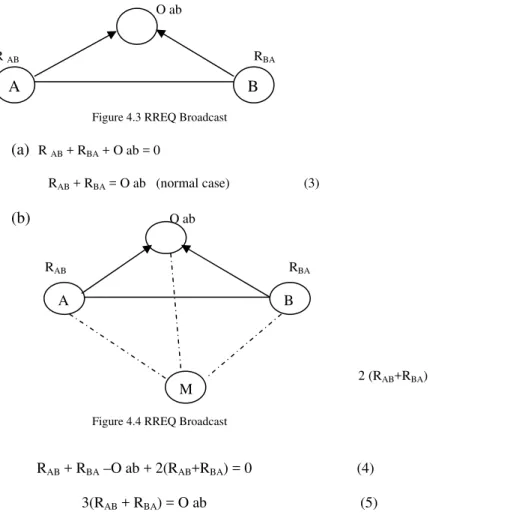
Documentos relacionados
In this paper, we study the effect of Grey Hole attack on Dynamic Source Routing (DSR) protocol in Mobile Ad-Hoc Network.. Keywords —Ad-Hoc Networks, Grey Hole
The elected cluster head will perform signature detection on all the member nodes along with running anomaly detection only on the backup node.. Similarly the backup will be
The best possible outcomes obtained from the above proposed fuzzy logic based protocol helps a mobile Ad- Hoc network to choose an efficient edge on the basis of
Routing is the critical issue in the MANET and focus based on routing protocols such as Ad hoc On-demand Distance Routing Protocol (AODV), Dynamic Source Routing (DSR),
Ad hoc On-demand Distance Vector Routing Protocol uses an on demand approach for finding routes, that is, a route is established only when it is required by a source node
The protocol performance evaluation for an ad-hoc network is necessary to be tested under realistic conditions, especially including the movement of the mobile nodes which
if timeout period of sender node is x then timeout period of receiver node will be (x-m), where m will be critical factor. This factor [16] helps us to control the
ADMR consists of 3 phases are Multicast State Setup, Multicast Packet Forwarding, Multicast State Maintenance .Like other tree based multicast routing protocols, it builds a