Guard against cooperative black hole
attack in Mobile
Ad-Hoc Network
Harsh Pratap Singh Sanjeev Sharma
School of IT, Rajiv Gandhi Proudhyogiki HOD, School of IT, Rajiv Gandhi Proudhyogiki
Vishwavidyalaya, Bhopal (M.P.) Vishwavidyalaya, Bhopal (M.P.)
singhharshpratap@gmail.com sanjeev@rgtu.net
ABSTRACT
A mobile ad-hoc network is an autonomous network that consists of nodes which communicate with each other with wireless channel. Due to its dynamic nature and mobility of nodes, mobile ad hoc networks are more vulnerable to security attack than conventional wired and wireless networks. One of the principal routing protocols AODV used in MANETs. The security of AODV protocol is influence by the particular type of attack called Black Hole attack. In a black hole attack, a malicious node injects a faked route reply claiming to have the shortest and freshest route to the destination. However, when the data packets arrive, the malicious node discards them. To preventing black hole attack, this paper presents RBS (Reference Broadcast Synchronization) & Relative velocity distance method for clock synchronization process in Mobile ad-hoc Network for removal of cooperative black hole node. This paper evaluates the performance in NS2 network simulator and our analysis indicates that this method is very suitable to remove black hole attack.
Keyword
Black hole attack, Routing Protocol, AODV, Mobile ad hoc network, RBS technique, Relative Velocity Distance.
1. INTRODUCTION
A mobile ad-hoc network [1] [2] is a self organizing network that consists of mobile nodes that are capable of communicating with each other without the help of fixed infrastructure. On the contrary to traditional wired networks that use copper wire as a communication channel, ad-hoc networks use radio waves to transmit signals. Mobility, an advantage of wireless communication, gives a freedom of moving around while being connected to a network environment. Ad-hoc networks are so flexible that nodes can join and leave a network easily. But this flexibility of mobile nodes results in a dynamic topology, open medium, distributed cooperation and constrained capability that makes it very difficult in developing secure ad-hoc routing protocols. Security being a serious issue, the nature of ad-hoc networks makes them extremely vulnerable to adversary’s malicious attacks. First of all, the use of wireless links renders a mobile ad-hoc network to be vulnerable to attacks of various types - black hole attack being one of them.
In black hole attack, black hole node acts like black hole in the universe. In this attack black hole node absorbs all the traffic towards itself and doesn't forward to other nodes whenever, source node wants to send packet to the destination node. To attract all the packet towards it, this malicious node advertise that it has shortest path through it to the destination node. There are two types of black hole attack-
• Black hole attack with single malicious node- Zone with single black hole node.
• Black hole attack with multiple malicious node- Zone with multiple black hole nodes.
To understand the functioning of the black hole node and for more details see [4, 5].
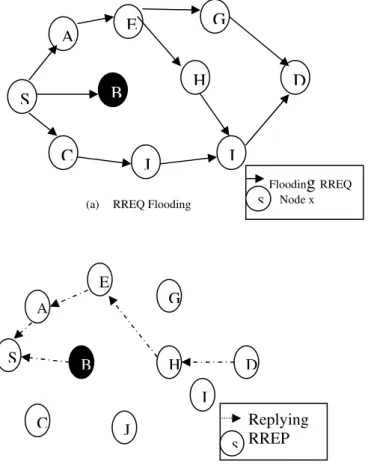
(a) RREQ Flooding
Figure 1. Diagram of a black hole attack.
2. AD-HOCROUTINGPROTOCOLSANDBLACKHOLEATTACK
AODV is one of the most common ad-hoc routing protocols used for mobile ad-hoc networks. As its name indicates AODV is an on-demand routing protocol that discovers a route only when there is a demand from mobile nodes in the network.
In an ad-hoc network that uses AODV as a routing protocol, a mobile node that wishes to communicate with other node first broadcasts an RREQ[6] (Route Request) message to find a fresh route to a desired destination node. This process is called route discovery. Every neighbouring node that receives RREQ broadcast first saves the path the RREQ was transmitted along to its routing table. It subsequently checks its routing table to see if it has a fresh enough route to the destination node provided in the RREQ message. The freshness of a route is indicated by a destination sequence number that is attached to it. If a node finds a fresh enough route, it unicast an RREP (Route Reply) message back along the saved path to the source node or it re-broadcasts the RREQ message otherwise. The same process continues until an RREP message from the destination node or an intermediate node that has fresh route to the destination node is received by the source node.
Route discovery is a vulnerability of on-demand ad-hoc routing protocols, especially AODV, which an adversary can exploit to perform a black hole attack [4] on mobile ad-hoc networks. A malicious node in the network receiving an RREQ message replies to source nodes by sending a fake RREP message that contains desirable parameters to be chosen for packet delivery to destination nodes. After promising (by sending a fake RREP to confirm it has a path to a destination node) to source nodes that it will forward data, a malicious node starts to drop all the network traffic it receives from source nodes. This deliberate dropping of packets by a malicious node is what we call a black hole attack.
E
Floodin
g
RREQNode x
S
G
B
C
J
D
A
I
H
S
S
A
H
C
E
G
D
J
I
B
Replying RREP
A malicious node sends RREP messages without checking its routing table for a fresh route to a destination. As shown in Fig. 1 above, source node 0 broadcasts an RREQ message to discover a route for sending packets to destination node 2. An RREQ broadcast from node 0 is received by neighbouring nodes 1, 3 and 4. However, malicious node 4 sends an RREP message immediately without even having a route to destination node 2. An RREP message from a malicious node is the first to arrive at a source node. Hence, a source node updates its routing table for the new route to the particular destination node and discards any RREP message from other neighbouring nodes even from an actual destination node. Once a source node saves a route, it starts sending buffered data packets to a malicious node hoping they will be forwarded to a destination node. Nevertheless, a malicious node (performing a black hole attack) drops all data packets rather than forwarding them on.
D
RREP
RREQ
RREP
RREQ
S RREP
RREQ
M
RREQ RREP
S – Source D-Destination M-Malicious Node
Figure 2. RREQ Broadcast
3. RELATED RESEARCH
Although various methodologies have been proposed to tackle the problem of black hole attacks. We survey them in the following:
Hesiri Weerasinghe [7] proposed the solution which discovers the secure route between source and destination by identifying and isolating cooperative black hole nodes. This solution adds on some changes in the solution proposed by the S. Ramaswamy to improve the accuracy. This algorithm uses a methodology to identify multiple black hole nodes working collaboratively as a group to initiate cooperative black hole attacks. This protocol is a slightly modified version of AODV protocol by introducing Data Routing Information (DRI) table and cross checking using Further Request (FREQ) and Further Reply (FREP). Most of the papers have addressed the black hole problem on the protocol such as AODV.
Chen Hongsong et al [8] proposes a security agent scheme for AODV routing protocol based on thread state transition utilizing network processor (NP) with architectural parallel features and special circuit for packet processing. In it one thread of NP is used as a security agent. It also requires the construction of the trace link list having the complete information about the source, destination, sequence numbers, RREQ count, Papadimitratos et al proposed Secure Routing Protocol based on the security association between the source node S and the destination node D utilizing the concept of MAC and the shared secret keys. The number of replies and the time – window the destination allocates for replies to a specific query are the design parameters. More over the source could provide an indicator of the required diversity so that D can regulate the number of replies. In it the intermediate nodes provide feedback in the event of a path breakage, and in some cases they may provide route replies [9].
Chen and U. W. Pooch [10] Proposes a neighbourhood based method to defend against black hole attack. The solution can be briefly described as follows: once the normal path discovery procedure in the routing protocol is done, the source node sends a special control packet to request the destination to send its current neighbour set. By comparing the received neighbour sets, the source node can determine whether there is a black hole attack in the network. To mitigate the impact of the black hole attack, they designed a routing recovery protocol to establish the path to the correct destination.
3
0
1
2
H. –Y. Chang [11] Knowledge-based intrusion detection systems accumulate knowledge about attacks, examine traffic and try to identify patterns indicating that a suspicious activity is occurring. This approach can be applied against known attack patterns only and the utilized knowledge base needs to be updated frequently.
4. PROPSOED METHOD
In This Paper, RBS (Reference Broadcast Synchronization) is very famous technique for clock synchronization process in Mobile-ad hoc Network, now this paper used RBS technique for removal of cooperative black hole attack.
Black-Hole attacks generate two cases:
(1) The node exploit the ad hoc routing protocol such as AODV to advertise itself as having a valid route to a
destination even though the route is suspicious with the intention of intercepting packet.
(2) The node consumes the intercepted packet; a black hole node absorbs the network traffic and drops all
packets.
The First step of solution is compare the internal clock time with external clock time sequence. The time sequence of internal and external clock if compared with standard threshold time clock the clock time of normal mobile node is greater than the threshold time initialization time duration. The normal nodes just behave like a malicious node (Black hole node) and list all these nodes in black hole node.
Some standard notations are used for comparison of the time clock:
RREP Reply Packet RREQ Request Packet
PTs Packet time clock source
PTd Packet time clock destination
Tthreshold Standard threshold time for request & response
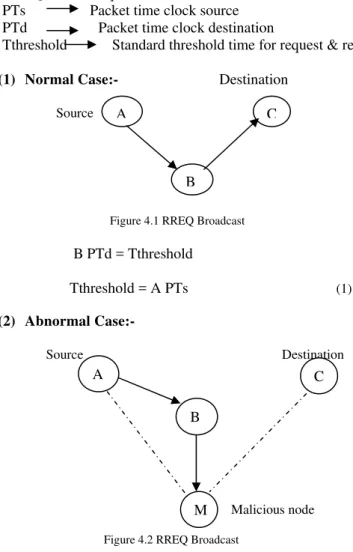
(1) Normal Case:- Destination
Source
Intermediate Node
Figure 4.1 RREQ Broadcast
B PTd = Tthreshold
Tthreshold = A PTs (1)
(2) Abnormal Case:-
Source Destination
Malicious node
Figure 4.2 RREQ Broadcast
If (B PTd = Tthreshold && A PTs> Tthreshold) A
B
C
A
B
C
Then these packets are added into malicious node.
Some time the clock synchronization is not work properly now the detection process of worms are failed. Now in this case this paper imposed another method for black hole detection using Relative Velocity distance.
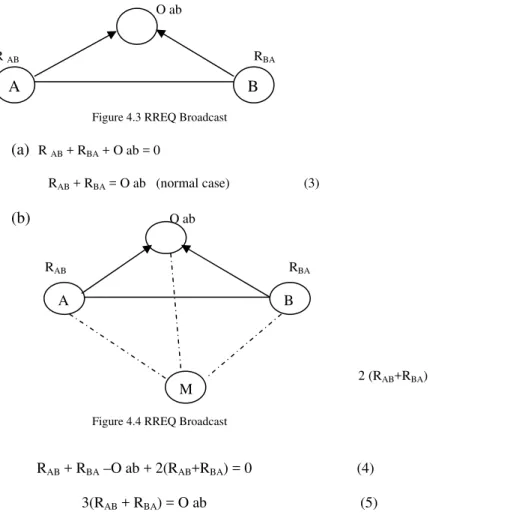
Step 1: First find Relative average distance through reference point. This is called standard Threshold distance.
Step 2: Now compare distance of source node to destination node with threshold distance- O ab
R AB RBA
Figure 4.3 RREQ Broadcast
(a) R AB + RBA + O ab = 0
RAB + RBA = O ab (normal case) (3)
(b) O ab
RAB RBA
2 (RAB+RBA)
Figure 4.4 RREQ Broadcast
RAB + RBA –O ab + 2(RAB+RBA) = 0 (4)
3(RAB + RBA) = O ab (5)
The distance of M node is increase and the value of malicious node is greater than average threshold value.
5. CONCLUSION
In the process of finding a malicious node (Black hole attack) we have imposed two method packet time clock synchronization with the help of RBS method and second one is the relative velocity reference distance method for the finding of malicious node. These methods are very efficient for the process of finding a malicious node in a mobile ad hoc network. this proposed technique is simulated these approach in NS2 network simulator and getting very good results in compare of threading technique instead of these feature it has some limitation such as we have find a wrong reference distance of the reference node now all the node found as a malicious node . Now in future we have minimized the process of finding exact process for relative reference distance.
6. REFERENCE
[1] Deng, Hongmei, Li, Wei and Agrawal, Dhrama P, Routing security in wireless ad hoc networks, IEEE Communications magazine, Oct. 2002, pp.70-75.
[2] Junhai luo; Mingyu Fan,Research on trust model based on game theory in mobile ad-hoc networks, Journal of Computer Research and Development,Vol 45, No. 10 2008, pp 1704-1710.
[3] C. E. Perkins, S, R, Das, and E. Royer: “Ad-hoc on Demand Distance Vector (AODV)”, RFC 3561.
A B
A B
[4] Hongmei Deng, Wei Li and Dharma P. Agrawal, “Routing Security in wireless ad hoc network” IEEE Communications Magazine, vol 40 no 10, October 2002.
[5] Sanjay Ramaswamy, Huirong Fu, Manohar Sreekantaradhya, John Dixon and Kendall Nygard, “Prevention of Cooperative Black Hole Attack in Wireless Ad Hoc Network”, 2003 International Conference on Wireless Networks (ICWN’ 03), Las Begas, Nevada, USA.
[6] Yibeltal Fantahun Alem, Zhao Cheng Xaun: Preventing Black Hole Attack in Mobile Ad-Hoc Networks Using Anomaly Detection. Department of Computer Science Tianjin University of Technology and Education Tianjin 300222, China.
[7] Hesiri Weerasinghe and Huirong fu, Member of IEEE, Preventing Cooperative Black Hole Attacks in Mobile Adhoc Networks: Simulation implementation And Evaluation, IJSEA, Vol 2, No.3, July 2008.
[8] Chen Hongsong, Ji Zhenzhou and Hu Zhenzhou and Hu Mingzeng, “ A Novel Security Agent Scheme for AODV Routing Protocol based on Thread State Transition”, Asian Journal of Information Techonolgy, Vol. 5, No. 1, 2006, pp 54-60.
[9] Panagiotis Papadimitratos and Zygmunt J. Haas- “ Secure Routing for Mobile Ad Hoc Networks”, Proceedings of the SCS Communication Networks and Distributed System Modelling and Simulation Conference (CNDS 2002), San Antonio, TX, January 27-31, 2002.
[10] B. Sun, Y. Guan, J. Chen and U. W. Pooch, “ Detecting black- hole attack in mobile ad hoc networks”, in Proc. Of the 5th European
Personal Mobile Communications Conference, Glasgow, UK, April 2003.