This presents a challenge to the management of a software development company if it is not prepared with a risk management approach. This leads to an assessment of the current state of information security activities in the company from a risk management perspective. It also mandates work within the company to improve information security.
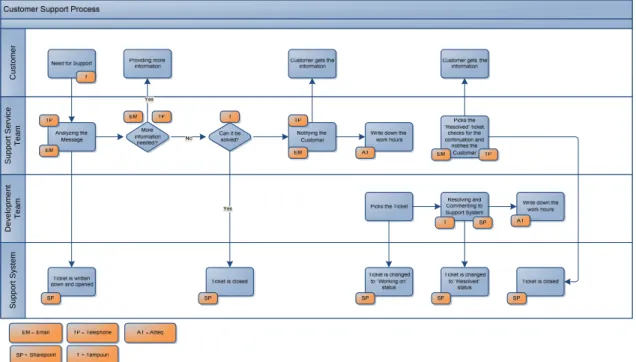
Agenteq Oy's information security policy specifies the goals, requirements of the operating environment, risk management, the importance of information security and information security activity in the company. The feature is installed to the client within the software distribution version and this is done in the operator process described in the next subsection. Each participant in the process also records his working hours in the billing system.

2 SECURITY RISK MANAGEMENT
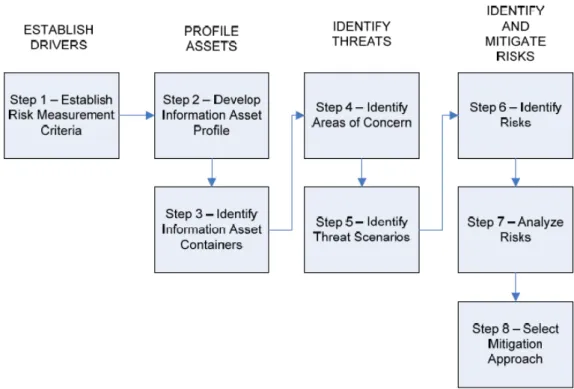
Known vulnerabilities can be mitigated by implementing controls that reduce the risk to the assets. Its role is to address how risk is responded to after it has been determined based on the risk assessment results. An important task is to also identify the changes in the risk environment and consider an organization's information systems.
Information System Scope is defined by the task/business process level context and the SDLC. The next issue to be addressed is the process of risk assessment in a security context. A risk analysis is a review of the collected data, and the result is a risk analysis for the organization.
An organization can ignore the risk which means that nothing is performed for the risk. An organization can mitigate the risk when controls are implemented to reduce the risk to an acceptable level. This usually happens when the cost of implementing controls outweighs the potential impact of the risk itself.
This may be the case when the cost of implementing security controls exceeds the cost of the potential impact of the risk itself. Although the risk assessment team may have a good view of the risks affecting the organization, this must be communicated to the entire organization (Landoll 2011, 395).

3 INFORMATION SECURITY CHALLENGES IN A SOFTWARE COMPANY
Strategy and resources An organization supports information security work by having an information security strategy. An organization needs at least one information security policy, but other policies, as well as risk management, may be required. In the steps of the software development life cycle it is good to review. threats to software being developed and con-. trols/safeguards to mitigate these risks.
An organization must have people who are in se‐. accuracy and to be able to advise the other employees Technical software develop‐. The software development environment must also be protected. It should already be in the soft-. true design phase and in the risk management and continuity planning phase. The root causes of the problems must be found and the employee's own responsibility in the course of action must be emphasized.
Organizational learning is also an interesting factor in the context of this development work, as action research is about learning in action (Coghlan and Brannick 2010, 5). In this case, information security is also about learning as an organization. It also supports the view that management is also at the heart of organizational learning regarding information security.
The internal information security development project started with this development work and has a lot to do with risk management activities in general, and creates a basis for the initial information security management system. The company's steps towards a managed future from an information security perspective have been developed based on this work.
4 DEVELOPMENT PROCESS OVERVIEW
The group also checked that the process diagrams were up-to-date and represented the real environment in which people work. The group then conducted a current security risk assessment and these sessions concluded with a self-assessment of a set of current information security practices at Agenteq Oy. The results gathered through these steps were documented and structured in the steering group work area for further processing.
The results were then discussed with the research group with best practice security knowledge as a reference to find the potential solutions and make suggestions to the group itself. The overall process started in February 2012 with the project launch carried out by Agenteq Oy's CEO during the first steering group meeting. The process took place in the three main iterations which were preceded by initiation iteration and followed by the closing iteration.
The model for this type of action research iteration reporting is taken from a publication by Iversen et al. The main initial literature and prior knowledge for this development work was collected in the spring of 2012. Thanks to the action research methodology, new information was continuously generated and found.
The new information security policy was launched in August 2012, which also started the action phase of this development process.

5 DEVELOPMENT PROCESS DETAILS
Through the implementation of the information security policy and risk assessment for the SDLC, an initial understanding of the level of risk is achieved. Management goals should be communicated to end users through policy (Paul 2011, 27). The activities in the initial iteration were related to the first two steps of the risk assessment process described in Chapter 2.
This meant that the risk assessment would focus on assets based on the information security policy. The project preparation step was also carried out, which includes the selection of the risk assessment team and its implementation. An information security management system (later called an ISMS) is a documented entity based on the operations and business risks of an organization formed by practices.
This work consisted of collecting the ideas of Agenteq Oy's assets in the research group, which was accompanied by the lines of information stated by the information security policy. In chapter 2 it was said that the second step of risk assessment, - project preparation - includes asset mapping. At the same time, the management group was appointed as the information security authority at Agenteq Oy.
One of Agenteq Oy's main customers had a safety audit done on the Tampuuri product. These results were documented in the risk action list for steering group review and analysis.
6 RESULTS
The launch of the new information security policy also created change in the information security climate of Agenteq Oy. The conclusion is that the implementation of the information security policy demonstrated the kind of leadership management explained by Suominen and that is why it worked so well. This was supported by the results of the subsequent self-assessment, which suggested that the overall actions based on the implementation of the new information security policy have raised the level of information security awareness at Agenteq Oy.
The emphasis on processes, the embrace of information security culture and recognition of the new EU data protection regulation proposal were the most important findings. This suggests that management processes must obtain data from the processes in the organization to make information-based decisions that support information security. Agenteq Oy does not have an ISMS as stated in the information security policy discussion.
Information security responsibilities are not listed in a practical way to make sense to staff. The information security policy states that every person working at Agenteq Oy is responsible for information security, but the practical point is missing. The integration of information security into the SDLC consists of practical activities carried out by people in the company's processes.
The result of the change was the introduction of a new information security policy and further related measures. The information security policy allowed work for information security in the company, which is a very important factor for future development activities.

7 DISCUSSION
During the research process, new information was found as a result of the action research methodology. This made comparing the situation-specific information with the theory challenging because the business itself required fast action. The cumulative understanding of the original theory and learned new theory was sometimes difficult to understand in practice.
Simultaneously with the results, a detailed development suggestion material was submitted to the management of Agenteq Oy. The first suggestion was to have a stronger integration of risk management into the company's current management processes. The implementation of these suggestions is strongly related to the ongoing enterprise resource planning (ERP) system renewal project at Agenteq Oy.
They are sides of the same coin and related to the software development life cycle, and they need each other. Due to the approach to researching the problem from a company-specific point of view, the generalizability of the results is limited. This research is valid because it produced answers to the research problem which was to find solutions for the development of information security in Agenteq Oy.
The results of the risk assessment and the further actions only apply to Agenteq Oy. Software development companies do develop ERP systems for their customers, but an ERP system for a software development company is an interesting concept from many research perspectives, in addition to the information security.
Evaluation of the effectiveness of information security training on the information security behavior of individuals and organizations.