A05] Нови подходи при изследване на киберзаплахите 49 Румен Трифонов1, Славчо Манолов1, Радослав Йошинов',. Владимир Становов, Шахназ Ахмедова, Евгений Семенкин Решетнев Сибирски държавен университет за наука и технологии, Красноярск (Руска федерация).
Case 3. BDA based prediction of software (SW) reliability and security
- INTRODUCTION
- HOW THE SOFTWARE CAN BECAME GREEN?
- STRUCTURE OF INFORMATION TECHNOLOGY
- Theoretical basis and models
- Methodology
- Program Tool
- CONCLUSION
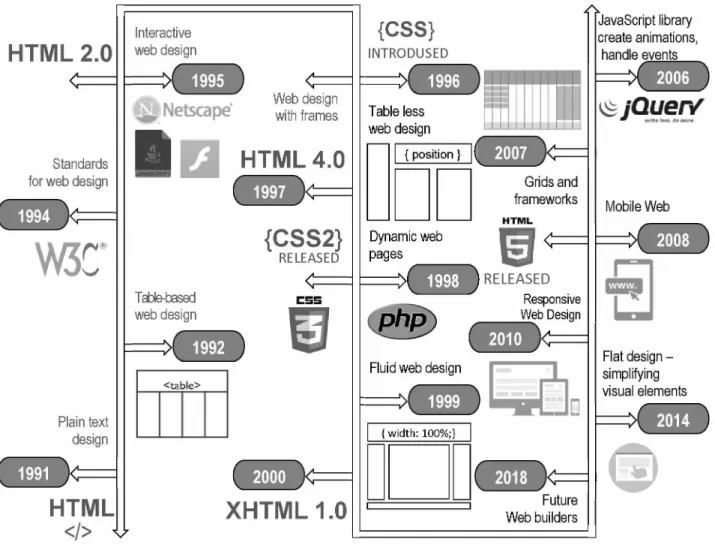
- EVOLUTION OF WEB DESIGN 1. In the beginning
The growth in the number of tablets in the coming years is important. This model is based on the calculation of the transient in the RAM cell and is described in detail in [14].
CSS2}
HTML
XHTML 1.0
- Developing web design
- Column grids
- Responsive web design and frameworks
- MODERN WEB DESIGN
- CSS Flexible Box Layout
- CSS Grid Layout
- A NEW STAGE IN THE EVOLUTION OF CYBER-SECURITY THREATS
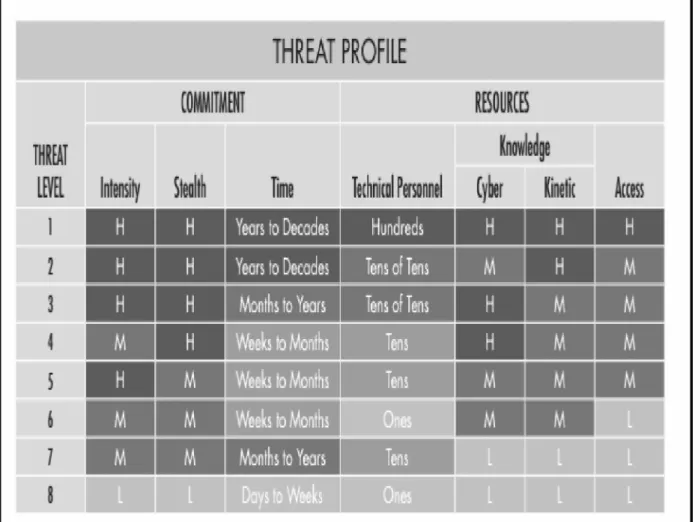
- NEW C LA SSIFICA TIO N S AND CO N C EPTS IN TH R EA T ANALYSIS To enable systematization, unification and classification o f cyber-security
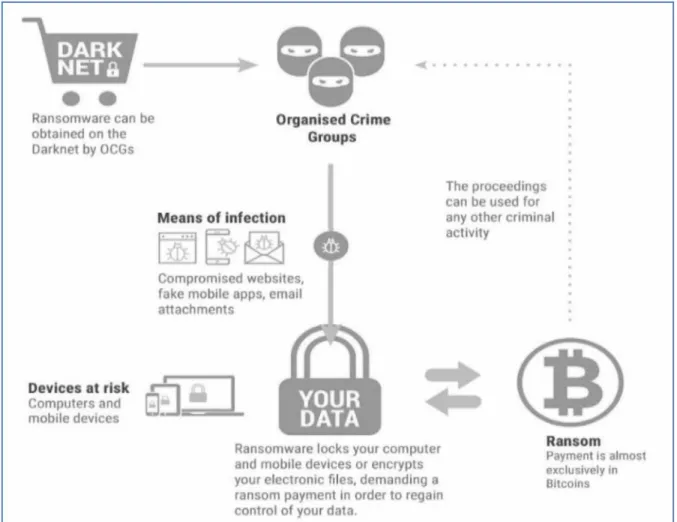
This can be achieved using the new concepts and classifications in the field of cyber threat research. The following image (Fig. 1) shows the organization of a Ransomware attack using the CaaS. The radical changes in the field of Cyber Security over the past two to three years have been formulated and adequately described in the remarkable ENISA report 'Threat Landscape Report.

Treat agents
CONCLUSIONS
Ultimately, this predetermined the choice of Artificial Intelligence methods for experiments in the subsequent stages of the project (Multi-Agent System - for the case of Tactical Cyber Intelligence and Recurrent Neural Networks - for the case of Operational Cyber Intelligence. Abstract: The present paper describes some of the results of received at the Technical University of Sofia in the implementation of the project related to the application of intelligent methods for increasing security in computer networks. The analysis of the feasibility of different methods of artificial intelligence has shown that a method that is equally effective for all stages of Intelligence Cybernetic cannot be identified.
While for Tactical Cyber Threats Intelligence a Multi-Agent System has been selected and experimented with, the recurrent neural networks are offered for the needs of Operational Cyber Threats Intelligence. Over the past few years, the trends in the transition of cyber threats from the cyber crime phase to the cyber war phase have also prompted a corresponding transition of cyber defense techniques to military technology [1].
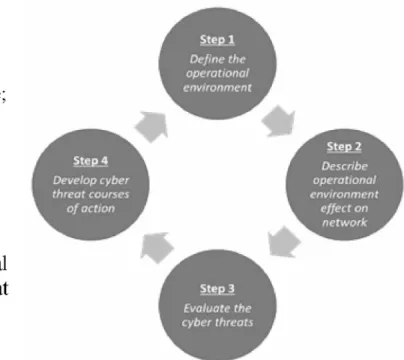
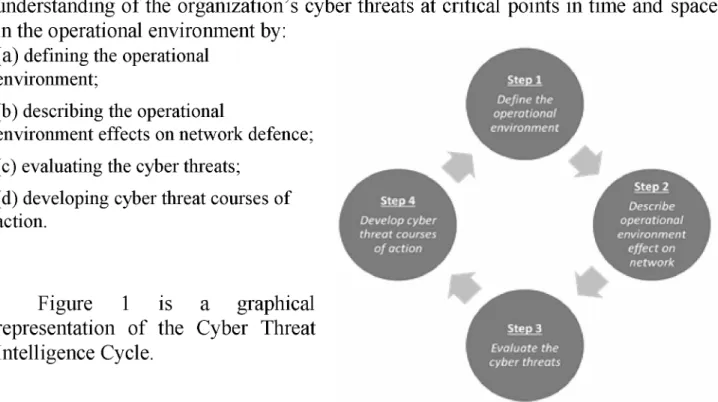
That is why, according to the vast majority of experts, the qualitative transition to new Cyber Defense tools should include the extensive use of Artificial Intelligence methods to analyze shared information, network flows, sources of threats, and plan countermeasures. effective influence, including proactive ones. -September 21, 2018, BULGARIA 59 understanding of the organization's cyber threats at critical points in time and space in the operational environment by:. environmental effects on network protection; d) developing cyber threat action courses. Like its military counterpart, Cyber Threat Intelligence is developed at three levels: strategic, operational and tactical.
For the purposes of this study, the second is considered: INSA defines [5] the operational level as: “The level at which campaigns and major operations are planned, executed, and sustained to achieve strategic objectives within theaters or other operational areas. At the operational level, the operational environment of the organization can be described in terms of physical, logical, information and social layers.
With a rapid pace of development and the desire for more effective countermeasures, artificial intelligence comes as a natural solution to the problem of coping with the ever-growing number of network attacks. As mentioned in the introduction to this article, world practice has already noted a significant number of different artificial intelligence applications in the field of computer security. Given this diversity of methods, it is of particular importance that appropriate criteria are selected for the assessment and selection of a specific application for each specific solution.
In the above project, the specification was carried out for two of the main components of CTI. It should be noted that within the project the application of Multi-Agent systems was chosen and experimented as the most suitable method for the needs of Tactical Cyber Intelligence.
Our main idea was that the basis for automating operational CTI can be the behavior model of the potential adversary. Currently, in the absence of references to such studies, it is assumed that this behavior can be divided for the time being into two basic types: hostile and non-hostile. Thus, feature extraction can be defined as an operation which transforms one or several signals into a feature vector.
Of course, many other more complex and advanced preprocessing methods can be proposed and used. The state of the art of the works described in this article can be defined as a transition from the development of a theoretical model to an experimental setting.
CO N CLU SIO N
However, it is a computationally difficult and time-consuming process, which was the main motivation for searching for a less computationally intensive alternative. As the trials are in their early stages, it should be emphasized that the results are encouraging, but it is too early to draw definitive conclusions. Abstract: The paper proposes an artificial intelligence-based approach for thyroid cancer detection in the Internet of Medical Imaging Things (IoMIT) ecosystem.
Keywords: Internet of Things (IoT), Medical Imaging Internet of Things (IoMIT), Artificial Intelligence (AI), Big Data (BD), Thyroid Cancer Detection. Abstract: The paper describes the application of differential evolution with a modified mutation strategy to global trajectory optimization problems.
Macedonia
- IN TR O D U C TIO N
- IN SIG H T IN TH E M AIN ISSUES
- CO N CLU SIO N
- R ELA TED W O R K
- PR O B L E M D E FIN IT IO N
- EX PER IM EN TS
The Engineering Universities and Faculties, especially in ICT, must be at the forefront of the following in their curriculum, and understand and apply new trends in project management. Fustik, The benefits of agile methodologies applied in the ICT development projects, International Journal on Inform. The extended text-based crisis plan cannot be used to inform and train civilians in the crisis area and first responders.
Our assumption is that some flood events are stored as prototypes in people's collective memory. It shows that 19 students were able to correctly fill in the text labels and summarize similar stories.
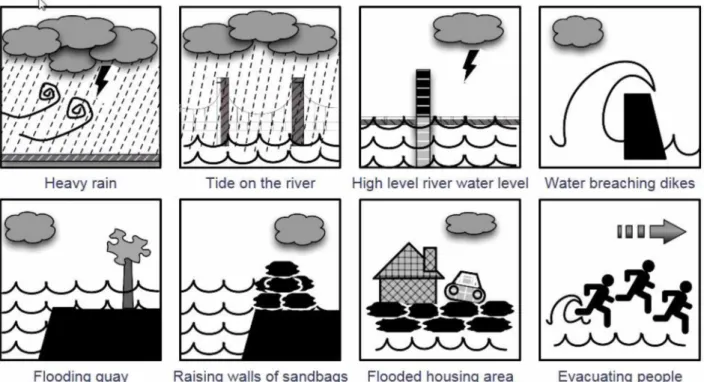
Flooding quay Raising walls of sandbags Flooded housing area Evacuating people
- CONCLUSION
- R ESEA R C H O B JE C T
- M O D EL IN M ATLAB / SIM U LIN K F O R ANALYSIS OF SIM PA TIC IN TER A C TIO N B ETW EEN TRA N SFO RM ERS
- SIM U LA TIO N RESULTS
This is the result of the saturation of already connected transformers, which is the result of an unexpected voltage drop in the system [3]. The calculated switching times of both transformers are taken at the moment when the current has its maximum value and when the voltage drops to zero. In the other two phases, the amplitude of the transient starting current is smaller than in phase A.
In the simulation, both transformers are set at turn-on so that there is no residual magnetism in their magnetic circuits. 8, we notice that the starting current in phase A of transformer T2 is more difficult to suppress than in the case when T1 was switched on as the first transformer in the network.

L hlkfth
Indirect voltage source frequency converters are a little more expensive in practice and are used when charging IM with a cage and synchronous motors (ventilation pumps, extruders, cranes, scrapers, surface treatment machines, etc.) The voltage in the circular current circuit can be constant ( the output converter has PWM and the output frequency is limited to 200Hz) or variable (the output converter is constantly driven and the output frequency goes up to 600Hz or even up to 1000Hz with reduced load). Each of these modulations is defined by the way of generating the switching functions of the switches sa,sb,sc of the converter (Figure 3). Sine wave modulation is such a technique that uses a comparison between a reference sinusoidal fundamental frequency signal and a carrier (triangle) signal with an increased frequency. In contrast to indirect vector control systems, the direct system is based on measuring, capturing and (or) estimating the spatial angle of the rotor flux.
The orientation of the control structure to the A - f 2 model of the induction motor in a stationary a -^ coordinate system avoids the need to transform the coordinates of the machine's space angles that participate in the analysis and synthesis of the control circles [ 27]. Consequently, due to the complexity of the nonlinear differential equations that describe the dynamic model of the induction motor, signal processing in the control system becomes complicated.
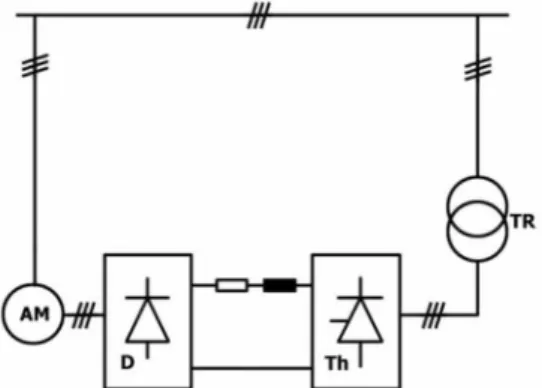
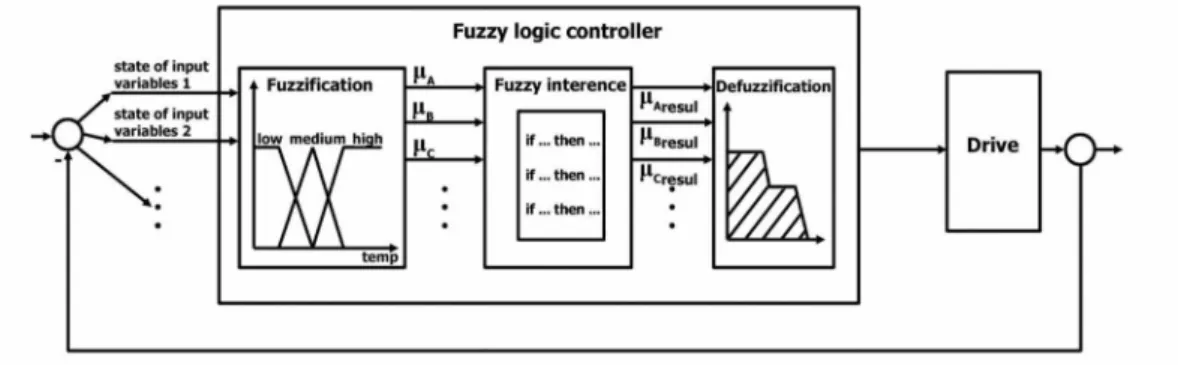
The induction motor is a high-level non-linear system and its vector control by means of linear techniques and controllers requires the use of complicated mathematical models. On the other hand, the power converter is also a non-linear element, because it is composed of 6 (six) power switches (Fig. 8) which are also non-linear elements. With this input, generalization or a logical explanation is made about the variable or the state of the input variables.
Determination of Membership Functions and Estimation of the Membership Coefficient On the other hand, the artificial neural network (ANN) based control finds its greatest application in nonlinear system identification and control. Artificial neural networks represent a nonlinear adaptive dynamic structure that contains highly interactive processing elements called neurons.
CONCLU SIO N
9] Depenbrock M.: Direct self control (DSC) of inverter fed induction machine, IEEE Power Electronics Specialists Conference 1987 p.632-641. 14] Gastli Adel, Motsui Nobuyoki: Stator flux controlled V/f PW M inverter with identification of IM parameters, IEEE Trans. 20] Jotten R., Mader G: Control methods for induction motor drives with good dynamic performance based on current and voltage as measured quantities, IEEE Trans.IA 1983 No.3 p.356.
Andrzej: Improved direct torque and flux vector control of PW M inverter-powered IM drives, IEEE Trans. 30] Takahaschi I., Moschikava A.: A new fast response and high efficiency control strategy of an induction motor, IEEE-IAS Annual Meeting, Toronto 1985 pp.496-502.
InfoTech-2018 is organized with the support of
Sofia 1000, Bulgaria Web site: http://www.ceec.fnts-bg.org CEEC is a non-governmental, non-political and non-profit professional association - part of civil society, Member of the Scientific Federation and Technical Trade Unions in Bulgaria. A not-for-profit organization, IEEE is the world's leading professional association for the advancement of technology. The name IEEE was originally an acronym for the Institute of Electrical and Electronics Engineers, Inc.
Today, the universal nature of the IEEE, as the diverse array of educators, engineers, scientists, innovators, leaders, entrepreneurs and practitioners, exemplifies the IEEE's mission to advance technology for the benefit of humanity. To promote interest in engineering, IEEE also serves students at colleges and universities around the world.
Conference Proceedings Dissemination, Referring and Indexing
Authors Index
PROCEEDINGS