A Technique to improve Security of Data in Multilevel Trust
Texto
Imagem
Documentos relacionados
Em diversos momentos da tese, Cristiano Ferronato interroga-se sobre a morfologia da instituição educativa, enquanto instância material, orgânica, pedagógica, portadora de
Thus, the methodology consists in presenting a set of images of edible (natural and cooked) and inedible products (objects), testing the role of colour saturation by varying
Future prediction of pollution levels in an area depending on past pollution and weather data using machine learning..
2 experimental data and the exact mathematical technique of Rios and Villa 3 it is in principle possible to obtain the individual data for each texture component and use this data
METHODS: This cross-sectional study used the intercensal technique to estimate, in the absence of longitudinal data, healthy life expectancy that is conditional and unconditional
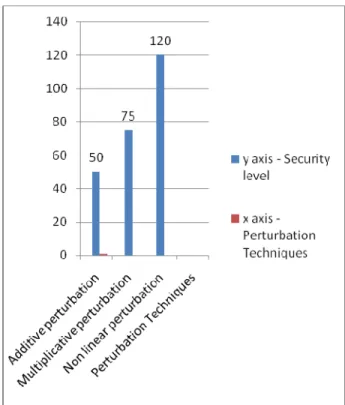
1) Protection from Data Breaches: Various security mea- sures and techniques have been proposed to avoid the data breach in cloud. One of these is to encrypt data before storage
The DES algorithm takes as input a 64-bit input block and a 64-bit key (56 key bits and 8 parity bits) and uses these two values to produce a 64- bit output. The cipher text output
Factor analysis is a statistical method that is widely used to identify dietary patterns (or fac- tors) that are not directly observable by aggregat- ing original data on