FORMULATIONS AND ALGORITHMS TO
FERNANDA SUMIKA HOJO DE SOUZA
FORMULATIONS AND ALGORITHMS TO
DESIGN COMMUNICATION NETWORKS
Tese apresentada ao Programa de Pós--Graduação em Ciência da Computação do Instituto de Ciências Exatas da Universi-dade Federal de Minas Gerais como req-uisito parcial para a obtenção do grau de Doutor em Ciência da Computação.
Orientador: Geraldo Robson Mateus
Belo Horizonte
FERNANDA SUMIKA HOJO DE SOUZA
FORMULATIONS AND ALGORITHMS TO
DESIGN COMMUNICATION NETWORKS
Thesis presented to the Graduate Program in Computer Science of the Federal Univer-sity of Minas Gerais in partial fulfillment of the requirements for the degree of Doctor in Computer Science.
Advisor: Geraldo Robson Mateus
Belo Horizonte
© 2012, Fernanda Sumika Hojo de Souza. Todos os direitos reservados.
Souza, Fernanda Sumika Hojo de.
S729f Formulations and algorithms to design communication networks / Fernanda Sumika Hojo de Souza. — Belo Horizonte, 2012.
xxv, 104 f. : il. ; 29cm
Tese (doutorado) — Universidade Federal de Minas Gerais – Departamento de Ciência da Computação.
Orientadora: Geraldo Robson Mateus.
1. Computação - Teses. 2. Redes de computadores – Teses. 3. Programação Inteira – Teses. I. Orientador. II. Título
Dedico esta tese a todos aqueles que me ajudaram durante esse percurso; em especial ao Daniel e aos meus pais Edina e Mauro.
Acknowledgments
Agradeço ao meu orientador, Prof. Geraldo Robson Mateus, pelos ensinamentos, paciência, compreensão e por acreditar na minha capacidade.
Ao Prof. Alexandre Salles da Cunha, agradeço pela dedicação a me ensinar, paciência e incentivo.
Ao Daniel, agradeço por estar sempre ao meu lado, apoiando e ajudando sempre que precisei.
Agradeço à minha família, Edina, Mauro e Natália, que sempre torceram pelo meu sucesso.
À tia Rô e tio It, que sempre foram presentes na minha vida, agradeço por todo apoio durante esse período da minha vida.
Agradeço aos meus amigos, que estiveram ao meu lado nos momentos de estudo e de lazer, compartilhando as dificuldades e as conquistas dessa caminhada.
Agradeço ainda ao Conselho Nacional de Desenvolvimento Científico e Tec-nológico (CNPq) e à Coordenação de Aperfeiçoamento de pessoal de Nível Superior (CAPES) por proporcionar apoio financeiro durante meu curso.
“A educação é a arma mais poderosa que você pode usar para mudar o mundo.”
(Nelson Mandela)
Resumo
O estudo de redes tem raízes na teoria dos grafos que remota a 1730. Desde então, redes tem sido utilizadas para modelar e simular interações entre elementos de sis-temas complexos, tais como de transporte, de comunicação e de computadores. Redes de comunicação são amplamente utilizadas para trocar informações entre entidades de um sistema. A importância das redes de comunicação aumentou dramaticamente nos últimos anos, chamando atenção para o estágio de projeto de um sistema real, dando origem a diversos problemas de otimização. Técnicas e soluções de Pesquisa Opera-cional tem desempenhado papel fundamental sobre uma vasta gama de problemas de projeto de redes. Nesta tese, nós estudamos como aplicar técnicas de otimização no pro-jeto de redes de comunicação. Primeiramente, nós abordamos o problema de projetar redes de telecomunicações hierárquicas assegurando resiliência contra falhas aleatórias e garantias de atraso na comunicação. Posteriormente, nós investigamos soluções para o problema de roteamento e alocação de comprimentos de onda com agregação de tráfego, proteção e qualidade de serviço em redes ópticas WDM. Finalmente, nós estu-damos como projetar redes de comunicação eficientes com base em características de redes complexas. Um conjunto de métricas é usado como critério de otimização no pro-jeto dessas redes. Diferentes formulações matemáticas para modelar os três problemas são propostas. Um algoritmo Branch-and-bound baseado nas formulações compactas é avaliado e comparado a uma abordagem Branch-and-price baseada nas formulações estendidas dos problemas. Uma análise comparativa é realizada, demonstrando que a abordagem Branch-and-price proposta é capaz de resolver problemas cujas dimensões estŃo fora do alcance de outras ferramentas tradicionais de otimização.
Palavras-chave: Branch-and-Price, Programação Inteira, Redes de Comunicação.
Abstract
The study of networks has roots in graph theory dating back to 1730s. From then on, networks have been used to model and simulate interactions among elements of intricate systems, such as transportation, communication and computer ones. Communication networks are widely used to exchange information among entities of a system. The importance of communication networks has dramatically increased over the past few years, drawing attention to the design stage of a real system, giving rise to many op-timization problems. Operations Research techniques and solutions have been playing a fundamental role across a wide range of network design problems. In this thesis, we study how to apply optimization techniques in the design of communication net-works. Firstly, we dedicate to the problem of designing hierarchical telecommunication networks ensuring resilience against random failures and maximum delay guarantees in the communication. Later, we investigate solutions to the routing and wavelength assignment problem with traffic grooming, protection and quality of service in WDM optical networks. Finally, we study how to design efficient communication networks based on complex networks features. A set of metrics is used as optimization cri-teria while designing such networks. Different mathematical formulations to model the three problems are proposed. A Branch-and-bound algorithm based on compact formulations is evaluated and compared to a Branch-and-price approach based on ex-tended formulations of the problems. Our comparative analysis demonstrates that the proposed Branch-and-price approach is able to solve problems whose dimensions are out of reach for other traditional optimization tools.
Keywords: Branch-and-price, Integer Programming, Communication Networks.
List of Figures
3.1 RMHND Problem . . . 17
4.1 Small Network Topologies . . . 51
4.2 30 Requests of Types OC-1, OC-3 e OC-12 . . . 53
4.3 60 Requests of Types OC-1, OC-3 e OC-12 . . . 53
4.4 90 Requests od Types OC-1, OC-3 e OC-12 . . . 54
4.5 Objective Function for 90requests . . . 54
4.6 Large Network Topologies . . . 57
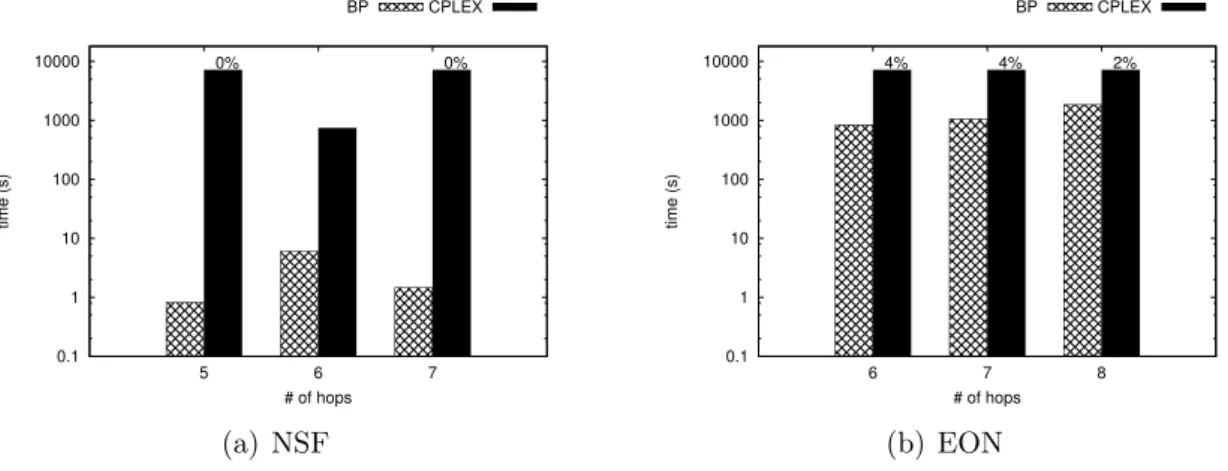
4.7 Computational Time . . . 58
4.8 GAP . . . 59
4.9 # of Columns . . . 60
4.10 # of Wavelegths vs. Traffic Lost . . . 61
5.1 Regular Networks . . . 68
5.2 Random Network . . . 69
5.3 WS Small World Network . . . 70
5.4 Scale Free Network . . . 72
5.5 Evolution of Network Topologies for |V|= 12 and D= 24 . . . 82
5.6 Network Construction . . . 83
5.7 Evolution of Network Topologies for |V|= 144 and D= 312 . . . 84
5.8 Path Length and Clustering Coefficient Analysis . . . 85
List of Tables
3.1 Real World Networks . . . 35
3.2 Summary of Random Instances with |N|= 16;|A|= 48;|K|= 120;|G|= 2 37 3.3 Summary of Random Instances with |N|= 25,|A|= 80,|K|= 300,|G|= 2 38 3.4 Summary of Real Instances with |G|= 3, pr = 2, se= 4 . . . 39
4.1 Summary of NSF and EON for 30requests . . . 52
4.2 Summary of NSF and EON for 60requests . . . 52
4.3 Summary of NSF and EON for 90requests . . . 52
5.1 Network Metrics . . . 66
5.2 Network Models’ Features . . . 72
5.3 Engineering Metrics ×Complex Metrics . . . 73
5.4 Summary of OTDP model . . . 81
5.5 Path Length Improvement . . . 93
Contents
Acknowledgments xi
Resumo xv
Abstract xvii
List of Figures xix
List of Tables xxi
1 Introduction 3
1.1 Motivation . . . 3 1.2 Objectives . . . 5 1.3 Contributions . . . 6 1.4 Outline . . . 7
2 Background 9
2.1 Linear and Integer Programming . . . 9 2.2 Delayed Column Generation . . . 10 2.2.1 Stabilization Methods . . . 11 2.2.2 Column Generation Primal Heuristics . . . 11 2.3 Branch-and-price . . . 12 2.4 Main Concepts on Communication Networks . . . 13
3 Resilient Multi-level Hop-constrained Network Design 15
3.1 Introduction . . . 15 3.2 Related Work . . . 18 3.3 Mathematical Formulations . . . 19 3.3.1 Arc-Flow Formulation (AFF) . . . 20 3.3.2 Aggregated Hop-Indexed Formulation (AHF) . . . 22
3.3.3 Arc-Path Formulation (APF) . . . 23 3.3.4 Considerations . . . 24 3.4 Branch-and-price Algorithm for the RMHND . . . 25 3.4.1 Lower Bounds given by the Arc-Path Formulation . . . 25 3.4.2 The Enumeration Tree . . . 27 3.4.3 Stabilization and Acceleration Strategies . . . 28 3.5 Equivalence of the LP Relaxations of AHF and APF . . . 29 3.6 Computational Experience . . . 34 3.7 Conclusion and Future Work . . . 38
4 Grooming Routing and Wavelength Assignment with Protection
and QoS in WDM Optical Networks 41
4.1 Introduction . . . 41 4.2 Related Work . . . 43 4.3 Problem Definition . . . 45 4.4 Mathematical Formulations . . . 46 4.4.1 Arc-Flow Formulation . . . 46 4.4.2 Arc-Path Formulation . . . 47 4.5 Branch-and-price Algorithm for the GRWA-PQoS . . . 49 4.5.1 Pricing Problem . . . 49 4.5.2 The Enumeration Tree . . . 50 4.5.3 Computational Experience . . . 50 4.6 Column Generation-based Heuristic . . . 54 4.6.1 QoS constraints . . . 55 4.6.2 Heuristic . . . 55 4.6.3 Computational Experience . . . 56 4.7 Conclusions . . . 60
5 Optimal Topology Design of Complex Networks 63
5.1 Introduction . . . 63 5.2 Measurements of Complex Networks . . . 65 5.3 Network Models . . . 66 5.3.1 Regular Networks . . . 67 5.3.2 Random Networks . . . 67 5.3.3 Small World Networks . . . 69 5.3.4 Scale Free Networks . . . 71 5.3.5 Summary of Network Models . . . 72
5.4 Optimization Models for Complex Networks . . . 73 5.4.1 The Optimal Topology Design Problem . . . 74 5.4.2 Arc-Flow Formulation . . . 74 5.4.3 Arc-Path Formulation . . . 76 5.5 Computational Experience . . . 80 5.6 Creating Optimized Communication Networks . . . 82 5.7 Exploring the Objective Function and Constraints . . . 85 5.8 Related Work . . . 89 5.8.1 Small World Optimization Algorithm . . . 89 5.8.2 Scale Free Optimization Algorithm . . . 91 5.8.3 Small World Topologies using GRASP . . . 92 5.9 Conclusion and Future Work . . . 93
6 Conclusion and Future Work 95
6.1 Final Remarks . . . 95 6.2 Future Work . . . 96
Bibliography 99
UNIVERSIDADE FEDERAL DE MINAS GERAISzyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
P P G C C
zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA PROGRAMA DE P6S-GRADUACJ.OEM CI£NCIA DA COMPUTA9AO
DCC-UFMGzyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
ATA DA DEFESA -DE TESE DA ALUNA
FERNANDA SUMlKA RaJa DE SOUZA
Realizou-se, no dia 11 de maio de dois mil doze, as 10:00 horas, na Sala 2077 do Instituto de Ciencias Exatas, da Universidade Federal de Minas Gerais, a 117a defesa de tese de Doutorado em
Ciencia da Computayao, intitulada FORMULAC;OES E ALGORITMOS PARA PROJETAR REDES DE COMUNICAC;AO, apresentada por Fernanda Sumika Hojo de Souza, graduada no curso de
Bacharelado em Ciencia da Computayao, como, requisito parcial para a obtenyao do grau de DoutorzyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
em Ciencia da Computayao, a seguinte Comissao Examinadora: PROF. GERALDO ROBSON MATEUS -Orientador (Departamento de Ciencia da Computayao - UFMG), PROF. ALEXANDRE SALLES DA CUNHA (Departamento de Ciencia da Computayao - UFMG), PROF. MARCUS VINiciUS SOLEDADE POGGI DE ARAGAO (Departamento de Informatica - PUC/Rio), PROF. MAURiCIO CARDOSO DE SOUZA (Departamento de Engenharia de Produyao - UFMG), PROF. NELSON MACULAN FILHO (COPPE -UFRJ).
A Comissao considerou a tese:
ex)
Aprovada( ) Aprovada condicionalmente, sujeita a alterayoes, conforme folha de modificayoes, anexa ( ) Reprovada, conforme folha de modificayoes, anexa
Finalizados os trabalhos, lavrei a presente ata que, lida e aprovada, vai assinada por mim e pelos membros omissao.
Belo Ho n, 11de maio de 2012.
ON MATEUS - ORIENTADOR
Doutor em Engenh ria de Sistemas e Computayao - Universidade Federal do Rio de Janeiro- Brasil
J.-zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
-r
c~·zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA...-b .--, ~ PROF. ALEXANDRE SALLES DA CUNHADout~;; :z;~uta~~~ade FederaldoRiodeJaneiro- Brasil
PROF. MARCUS VINiciUS SOLEDADE POGGI
~R 1'~
UNIVERSIDADE FEDERAL DE MINAS GERAISzyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
P P G C C
zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBAP R O G R A M A D E P 6 s ~ R A D U A C l ozyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
EM Cli!HC'A DACOMPIJTA~.\OzyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
DCC-UFMGzyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
dm
zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBAU /zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA;[Y ~ ~ ---.- ....
PRQf.)'1AURiCIO CARDOSO DE SO~
Dou~r em Informatica - Universite Blaise Pascal - Clermont-Ferrand - Franya
L
'l _PROF. NELSON MACULAN FILHO
Chapter 1
Introduction
In this Chapter, we provide a brief introduction to the main problems we are going to discuss along the present thesis. Section 1.1 is devoted to the motivation of this work while the main objectives are detailed in Section 1.2. In Section 1.3, we specify the main contributions of this work. Finally, in Section 1.4, the structure of the present thesis is described.
1.1
Motivation
The study of networks has roots in graph theory dating back to 1730s, when Leonard Euler formulated the Königsberg Bridge Problem as a graph optimization problem [Bondy and Murty, 1976; Diestel, 2005]. From then on, networks have been used to model and simulate interactions among elements of intricate systems (transportation, communication and computer, just to name a few ones). In the context of transporta-tion, consider a road network as an illustrative example. Cities are crossing points among different roads enabling vehicles to create their own routes along the network. Rail networks and airline networks work in a similar fashion. One ancient well known network is the postal network, in which messages are exchanged among different peo-ple regardless how far they might be located. On the other hand, with the advent of technology, today we also have other huge networks such as data distribution, cellular and the Internet.
Communication networks [Frank et al., 1972] are widely used to exchange infor-mation (or a packet, a commodity) among entities of a system. We usually call these entities as “nodes” or “vertices”1, which may be classified into source, destination (or
even both) and transhipment, depending on their role in the network. A general
com-1The terms “nodes” and “vertices” will be treated interchangeably in this work.
4 Chapter 1. Introduction
munication network is composed of a large number of nodes, which may not necessarily be connected to all other nodes of the network. The idea is that a node also works as a connection point between different incoming and outgoing paths. The communication among the entities is possible by transmission media (also called “links” or “edges”). Usually, links are associated to variable capacities. In a single communication network, links may have different types of facilities and associated capacity.
The importance of telecommunication networks has dramatically increased over the past few years. We have been facing evolving technologies which offer a variety of services such as audio, video and general data transmission. Moreover, the increasing demand from customers and the concern about service reliability in order to avoid customer complaints require grades of organization, leading to hierarchical telecommu-nication networks. The basic idea is that priorities are associated to sets of customers so that network providers can offer higher levels of service in both serviceability (e.g., high bandwidth) and survivability (failure protection) to certain key customers.
In this context, quality of service (QoS) [Srikitja et al., 1999] arises to provide special guarantees to different applications or customers. QoS refers to the ability of a network to deliver predictable results. Elements of network performance within the scope of QoS often include availability (uptime), throughput, latency and failure rate. A set of QoS metrics is discussed along this work. We show how issues like delay, load balancing, resilience and vulnerability can be taken into account while designing communication networks.
Network survivability is another key issue that may not be disregarded in the de-sign of networks. Under failure conditions, protection mechanisms enable the network to maintain maximum connectivity and quality of service. These mechanisms lie in the topological level, protocol design or even additional bandwidth allocation. In the topological level, for instance, a two-connected network is robust against random single link/node failures. Other examples include the usage of dynamic routing protocols to reroute traffic against network dynamics during the transition of network dimensioning or equipment failures. A bandwidth allocation mechanism proactively allocates extra bandwidth to avoid traffic loss under failure conditions.
1.2. Objectives 5
related to a small data communication latency. Thereby, engineered networks could take advantage of being modelled to present specific complex features, to improve their overall efficiency. Several network models were proposed and studied in an attempt to represent elements of a system and their relationships [Lewis, 2009; Newman, 2003; Watts, 2004; Thadakamalla et al., 2008]. Early models include regular [Lewis, 2009] and random networks [Erdös and Rényi, 1959; Gilbert, 1959]. In the late 1990s, new network models were proposed, and complex network concepts began to be formalized. One important stage while creating engineered networks concerns the topological design of the network, in which critical decisions must be taken. This problem is referred as a “network design problem” in the Operations Research (OR) community [Magnanti and Wong, 1984]. This stage may involve determining where to place the components and how to connect them. Moreover, most of the time, fixed and variable costs are involved, giving rise to many optimization problems. Operations Research techniques and solutions have been playing a fundamental role across a wide range of network design problems. Considering the set of requirements to be met while designing such networks, an optimization phase is certainly of great importance. The fulfillment of these requirements is becoming increasingly challenging, once entities have been demanding high standards of service, including hierarchy, serviceability, survivability and extreme efficiency. Optimization techniques have been successfully applied in designing engineered networks [Magnanti and Wong, 1984; Resende and Pardalos, 2005; Chinneck et al., 2009].
1.2
Objectives
The main goal of the work described in this thesis is to design communication networks by means of optimization techniques in an exact approach. Therefore, the following issues compose our general objectives:
• Proposal of alternative mathematical formulations to model three network design problems, such that they can be based on network flows or path variables.
• Performance comparison between a Branch-and-bound algorithm for compact formulations and a Branch-and-price algorithm devised by applying a Delayed Column Generation approach to the problem.
6 Chapter 1. Introduction
• Evaluation of acceleration strategies while solving a Delayed Column Generation algorithm, such as stabilization and column management.
Based on these issues, we are investigating how state of the art algorithms may be improved or complemented by alternative approaches. In this context, the specific objectives of this thesis are:
• Propose an exact solution approach to design a hierarchical network with re-silience and delay guarantees. The implied solution must deal with different sets of nodes which have different requirements, single failure resilience constraints and hop constraints to assure a maximum delay.
• Propose an exact solution to design optical networks considering routing, wave-length assignment, traffic grooming, protection and quality of service.
• Propose an exact algorithm to design efficient communication networks based on complex network features. By optimizing desired metrics such as shortest path length and maximum vertex degree, the overall efficiency of engineered networks may be improved.
1.3
Contributions
The contributions of this thesis were partially published/submitted and are listed be-low.
• Souza et al. [2008], published in the XL Simpósio Brasileiro de Pesquisa
Opera-cional (SBPO’08). In this work, a GRASP-based algorithm to generate small
world topologies is proposed.
• Souza et al. [2009], published in the First IEEE International Workshop on Net-work Science For Communication NetNet-works (NetSciCom’09) in conjunction with
IEEE Infocom (INFOCOM’09). This work addresses the problem of designing
complex networks based on two mathematical formulations and a column gener-ation algorithm.
• Souza et al. [2010b]1, presented at the10th INFORMS Telecommunications Con-ference. This work concerns a column generation algorithm for the resilient
1.4. Outline 7
• Souza et al. [2010c]1, presented at the Journées de l’Optimisation/Optimization
Days 2010 (JOPT’10). This work concerns a column generation algorithm for
the resilient multi-level hop-constrained network design problem.
• Souza et al. [2010a], published in the IEEE GLOBECOM Workshop on Complex
and Communication Networks (CCNet’10). In this work, a Branch-and-price
algorithm for the design of complex networks is developed.
• Souza et al. [2012a], published in the Handbook of Optimization in Complex Net-works: Theory and Applications. In this chapter we review optimization
algo-rithms to design complex communication networks.
• Souza et al. [2012b], to be published in the IEEE Symposium on Computers and
Communication (ISCC’12). In this work, we compare solutions for the routing
and wavelength assignment problem with traffic grooming, protection and quality of service in WDM optical networks.
• Work1 submitted to the European Journal of Operational Research. In this
pa-per we propose three formulations for the resilient multi-level hop-constrained network design problem, evaluate algorithms to solve the problem and prove the equivalence of two distinct formulations.
In parallel with his research topic, the student has been participating as a co-author in other works related to her research topic: complex communication networks. As a result of this iteration another work has been published and is listed below.
• Guidoni et al. [2010], published in IEEE Global Communications Conference
(GLOBECOM’10). This work studies the channel assignment problem over a
Heterogeneous Sensor Network with small world features.
• Guidoni et al. [2012], to be published in IEEE Symposium on Computers and
Communication (ISCC’12). This work proposes a framework based on small
world features to provide QoS in Heterogeneous Sensor Networks.
1.4
Outline
This thesis is organized as follows. In Chapter 2, a background of the methods adopted in our methodology is provided, along with the main concepts on communication net-works that we study in this work. We start giving a contextualization of Linear and
8 Chapter 1. Introduction
Integer Programming, followed by a Delayed Column Generation overview. We also introduce the Branch-and-price algorithm based on a combination of Delayed Column Generation and Branch-and-bound methods. Finally, we introduce some concepts on communication networks.
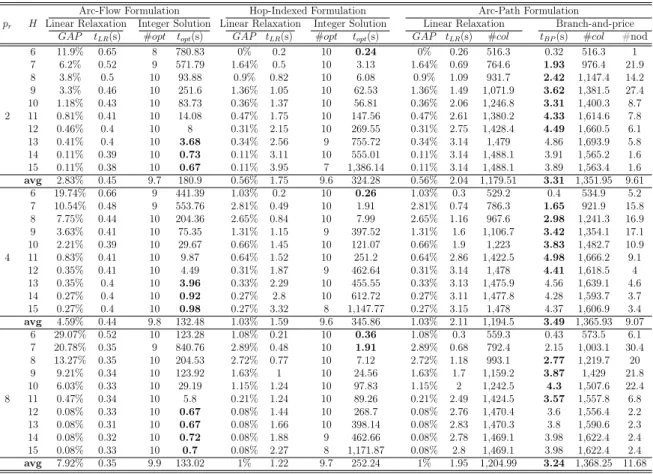
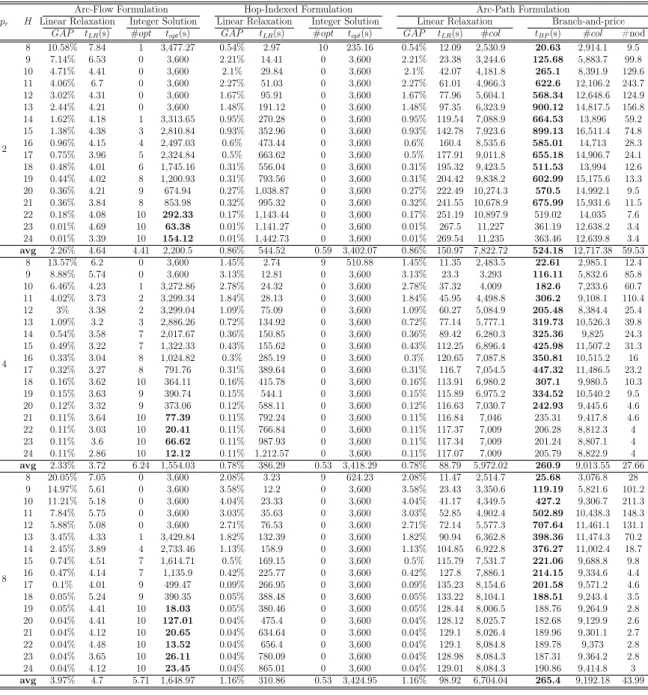
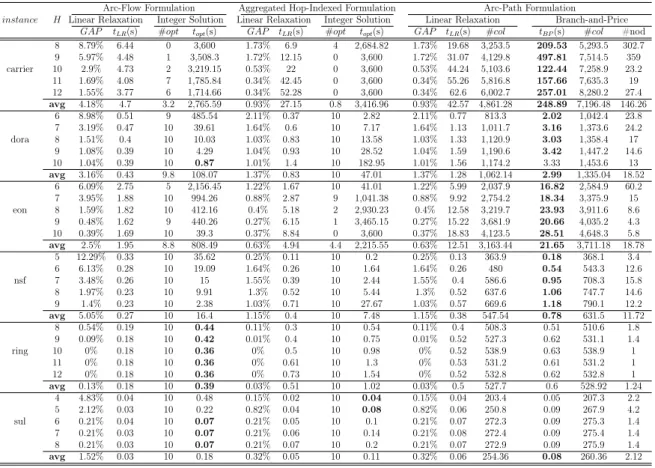
Chapters 3, 4 and 5 concern three different network design problems in the con-text of communication networks. All of them are tackled using a similar methodology. Chapter 3 addresses the Resilient Multi-level Hop-constrained Network Design prob-lem, which consists of designing a hierarchical network with resilience and delay guar-antees. The problem is introduced and contextualized in the literature. Two compact mathematical formulations based on network flows are proposed as well as an extended formulation based on a exponential number of path variables. A Branch-and-price al-gorithm based on the last formulation is developed and computational experiments are run, allowing a comparative analysis on the efficiency of the Branch-and-price algorithm and a Branch-and-bound algorithm for the former formulations.
Chapter 4 concerns formulations based on network flows and path variables for the Grooming, Routing and Wavelength Assignment problem with Protection and QoS in WDM optical networks in order to minimize the number of wavelengths used. We compare the performance of different algorithms over real world instances.
Chapter 5 is dedicated to the Optimal Topology Design of Complex Networks problem. We review some models, heuristics as well as exact solution approaches based on Integer Programming methods to generate topologies owning complex fea-tures. Two mathematical formulations are proposed, such that the former is based on network flows and the latter corresponds to an extended formulation with path vari-ables. A comparative study between a Branch-and-bound algorithm for the flow-based formulation and a Branch-and-price algorithm for the path-based formulation is also performed.
Chapter 2
Background
This chapter is devoted to the fundamental aspects of Operations Research techniques and the basic concepts on communication networks. We start contextualizing Linear and Integer Programming. Next, we provide a general idea of the methods applied in our solution approach. The Delayed Column Generation method is presented as well as some related issues. In the following, we introduce the Branch-and-price algorithm. Finally, we review the main concepts on communication networks in order to provide a better understanding along this work.
2.1
Linear and Integer Programming
Linear Programming (LP) consists in the optimization of a linear objective function, subject to linear equality and inequality constraints. The idea of solving a linear programming problem is usually associated with a way to achieve the best outcome when different activities compete for a set of scarce resources. The conception of linear programming is credited to George Dantzig, who proposed the problem around 1947. In this context, the simplex algorithm [Dantzig, 1963] was also proposed by Dantzig
in the late 1940s, for solving LP problems. The simplex method is widely known for its practical ability to solve diverse management decision problems. Moreover, the theoretical importance of the method cannot be disregarded since it is a basis for other methods in Integer and Nonlinear Programming [Bazaraa et al., 2004].
Integer Linear Programming (ILP) extends the Linear Programming in the par-ticular case that variables are all required to be integers. In contrast to Linear Pro-gramming, which can be usually solved efficiently, Integer Programming problems are still a challenging field of research. These decision problems modelled as Integer Pro-grams are classified as NP-hard. Even the special cases, where variables are required to
10 Chapter 2. Background
be0or1(binary integer programming) or when only some of the variables are required to be integers (mixed integer programming), are generally also NP-hard. This means that there are no known polynomial time algorithms to solve (optimally) a general Integer Programming problem.
Several approaches have been proposed to solve Integer Programs in the last decades. Early work in this direction accounts for the cutting-plane method intro-duced by Gomory [1958]. Another approach is the well known Branch-and-bound (BB) algorithm proposed by Land and Doig [1960], which consists of an implicit enu-meration procedure of all candidate solutions. These pioneer methods gave rise to other sophisticated approaches such as the Branch-and-cut (BC) and Branch-and-price (BP) algorithms. Roughly speaking, these approaches are hybrids of Branch-and-bound plus cutting-plane and Branch-and-bound plus Delayed Column Generation, respectively. For further details regarding Integer Programming, see [Wolsey, 1998].
2.2
Delayed Column Generation
The Delayed Column Generation is a technique for solving Linear Programming prob-lems, in which we do not need to consider all columns (variables) explicitly at once. In doing so, an extended reformulation of the problem (having exponentially many variables) works as the basis of the procedure. In order to derive lower bounds for a given formulation, we must deal with the excessive number of columns (variables) implicitly. Therefore, the method starts with a restricted set of columns and add new columns on-the-fly, as needed. This Linear Program is usually referred to as the Re-stricted Master Program (RMP). A new ReRe-stricted Master Program, enlarged with new columns is solved iteratively until no further columns need to be added. At this point, the Linear Program has been solved. Typically, the total number of columns at the end of the procedure is just a tiny fraction of the total number of columns. This method is known for providing stronger LP bounds compared to the linear relaxation of a compact formulation for many problems.
2.2. Delayed Column Generation 11
violate the dual constraints is usually called pricing problem. The violation checking is based on the computation of the reduced cost of a new column. Every time a new RMP is solved, it enables dual prices for each of the constraints, which are used in the pricing problem in a mutual feeding strategy.
The Delayed Column Generation method will be explored in more detail in Chap-ters 3, 4 and 5, applied to specific problems. For further information, see [Desrosiers and Lübbecke, 2005; Lasdon, 1970; Barnhart et al., 1998].
2.2.1
Stabilization Methods
Stabilization methods for column generation emerged as an attempt to reduce the total time spent while solving the algorithm due to degeneracy and convergence difficulties. One of the problems faced in column generation arises when a primal solution is as-sociated to multiple dual solutions. As the subproblems are totally dependent on the dual values, the choice of which dual values to use becomes a relevant issue.
Many stabilization methods have been proposed in the literature [Merle et al., 1997; Lübbecke and Desrosiers, 2005; Rousseau et al., 2007; Amor et al., 2009]. To understand how stabilization works, let us consider the interior point stabilization method proposed by Rousseau et al. [2007]. The main idea of this method is to select a dual optimal solution interior to the optimal face of the dual polyhedron rather than retrieving an extreme point. In order to achieve the centralization of dual values, several extreme points of the optimal dual polyhedron need to be generated, so that an interior point corresponding to a convex combination of all these extreme points may be computed. This is accomplished by solving an auxiliary Linear Programming problem that exploits complementary slackness conditions given by the optimal RMP primal-dual solution. The literature reports significant gains when such dual values are used to price columns.
2.2.2
Column Generation Primal Heuristics
Primal heuristics are generally referred to as methods based on truncated exact opti-mization procedures or constructive processes using relaxation [Barnhart et al., 1998; Joncour et al., 2010]. Being able to derive “good” primal feasible solutions, they become an effective algorithm when optimality is not the major concern.
12 Chapter 2. Background
or even by a mixture of both. The main drawback of this approach is that feasibility is not guaranteed, and thus, an ad-hoc strategy needs to be used to repair infeasibility. Rounding heuristics are another way to find approximated solutions. For this, the master LP solution is taken as a base for column selection. Greedy heuristics have also been proposed. They consist of iteratively adding a greedy selected column to the partial solution until a feasible solution is achieved.
The Branch-and-price tree may be used to develop a diving heuristic, which consists of a searching depth-first heuristic. Different from how the exact approach explores the tree, in a diving heuristic we do not need to be concerned in balancing the tree. At each node, a branch is heuristically selected based on greedy or rounding strategies. For additional details, see [Joncour et al., 2010].
2.3
Branch-and-price
and-price [Barnhart et al., 1998, 2000] considers a combination of the Branch-and-bound and Delayed Column Generation. In a simple view, the procedure consists in applying the Delayed Column Generation method to derive lower bounds to be used during the enumerative search. As mentioned before, the Delayed Column Generation is expected to provide strong LP bounds through the Branch-and-bound search, al-lowing a higher number of subproblems to be pruned by bounds. The fewer created subproblems, more efficient the algorithm tends to be.
A Branch-and-price algorithm starts solving the linear relaxation of the root node of the Branch-and-bound tree through the Delayed Column Generation procedure. As mentioned in the last section, when no more columns with negative reduced costs are found, the LP relaxation of the problem has been computed in the root node. If the LP solution is integer, it also solves the original integer problem. Otherwise, being fractional, we must resort to branching.
It should be clear that applying a traditional Branch-and-bound algorithm for the RMP obtained at the end of the column generation approach does not guarantee that an optimal (nor even feasible) solution to the problem will be found. In contrast to that, we embed the whole column generation procedure in an Branch-and-bound framework, leading to a BP algorithm, where new columns are likely to be generated at each node in the enumeration tree.
2.4. Main Concepts on Communication Networks 13
of the computing times in BP algorithms, ideally, thebranching rule should not destroy the structure of the pricing subproblems. Another aspect while branching, involves how variables are chosen. Once the branching rule over a certain variable is defined, we must adopt a branching policy, in order to choose which variable on which to branch. This
choice can be based on the fractional variable farthest or closest to integrality, or even at random.
Finally, in order to choose a node to explore from the list of outstanding nodes in the branching tree, many approaches may be considered. The main node selection policies include the breadth first, depth first and best bound. In the breadth first, the nodes of the tree are explored in the same order in which they were created. Depth first selection policy explores the last node created, going deeper in the BB tree. The best bound or best first chooses the node having the lowest value (in a minimization problem) of the LP relaxation among all BB nodes.
For a more complete review regarding Branch-and-price implementations, see [Barnhart et al., 1998, 2000; Desrosiers and Lübbecke, 2005].
2.4
Main Concepts on Communication Networks
Many network measurements have been established aiming to characterize the perfor-mance and general operational conditions of a network. The main metrics are closely related to the communication in the the network, i.e., the exchange of information (or packets). Some of them are listed in the following.
• Delay: time interval elapsed between the data departure time from the source
vertex to the arrival time at the destination vertex.
• Jitter: time variation among packets arriving at a destination vertex. • Throughput: data rate supported by the network.
• Loss: amount of data that did not reach its destination vertex.
The concept of quality of service emerged in an attempt to provide guarantees of performance in communication networks. We present two important requirements in the QoS context:
• Serviceability: the ability of a service to be obtained when requested, and continue
14 Chapter 2. Background
• Survivability: the ability of a system to continue to function during and after a natural or man-made disturbance. It is usually associated to fault tolerance mechanisms. In this case, a system is said to be resilient and reliable. Otherwise, vulnerability begins to be an issue.
In order to provide survivability in a network, some mechanisms have been pro-posed.
• Protection: uses pre-assigned capacity to ensure survivability. Two schemes can
be defined:
– Dedicated: all the traffic is allocated twice in the network capacity, i.e., different protection paths do not share common resource.
– Shared: multiple protection paths may go through common resources; when one protection path is activated, other protection paths that share common resources with it may have to be rerouted.
• Restoration: reroutes the affected traffic after failure occurrence by using
avail-able capacity.
In the following, we present the main concepts in Optical Networks:
• Wavelength Division Multiplexing (WDM): is a technology which multiplexes a
number of optical carrier signals onto a single optical fiber by using different wavelengths.
• Lightpath: sequence of optical “hops” defined by a physical path through which the optical signal bypasses intermediate nodes, creating a virtual connection be-tween its end nodes.
• Routing and Wavelength Assignment (RWA): problem of setting up lightpaths
by routing and assigning a wavelength to each request that must be attended by the network.
• Traffic Grooming: technique to group several requests for traffic on the same
wavelength.
– Static: considers the case in which all requests are known in advance and do not change by long periods of time.
– Dynamic: demands appear dynamically, according to a probability
Chapter 3
Resilient Multi-level
Hop-constrained Network Design
In this chapter we investigate the Resilient Multi-level Hop-constrained Network De-sign (RMHND) problem, which consists of deDe-signing hierarchical telecommunication networks, assuring resilience against random failures and maximum delay guarantees in the communication. Three mathematical formulations are proposed and algorithms based on the proposed formulations are evaluated.
3.1
Introduction
In the telecommunication context, we have been facing evolving technologies which offer a variety of services such as audio, video and general data transmission. The increasing demand from customers and the concern about service reliability in order to avoid customer dissatisfaction require grades of organization, leading to a hierar-chical telecommunication network. The basic idea is that priorities are associated to sets of customers so that network providers can offer higher levels of service in both serviceability (e.g., low delay, high bandwidth) and survivability (failure protection) to certain key customers.
The importance of telecommunication networks has dramatically increased over the past few years. Consequently, Operations Research techniques and solutions have been playing a fundamental role across a wide range of telecommunication problems [Magnanti and Wong, 1984; Resende and Pardalos, 2005]. Considering the set of re-quirements to be met while designing such networks, the employment of an optimization phase is certainly of great importance.
16 Chapter 3. Resilient Multi-level Hop-constrained Network Design
applied to the Resilient Multi-level Hop-constrained Network Design. The Multi-level Network Design (MLND), introduced by Balakrishnan et al. [1991], generalizes several well-known optimization models and addresses design decisions for hierarchical telecom-munication, transportation, and electric power distribution networks. The nodes in this network have different levels of importance (priorities are associated to the nodes), re-quiring different levels of technologies in communication. Given an undirected graph whose nodes are partitioned intoLlevels, each edge can contain one of the Ldifferent
levels of technology, with higher level requiring higher fixed costs. The goal is to select a connected subset of edges assigned to a technology level so that each source-destination pair communicate via its minimal necessary level or higher level, minimizing the total cost of the assigned technologies. We extended this problem to the RMHND, such that the subgraph implied by the selected edges provides two edge disjoint paths with up toH hops for each pair of nodes, i.e., it assures single-edge failure resilience and a
maximum delay.
In the present study, we devise two compact formulations for the RMHND whose solution is accomplished by solving a Mixed Integer Program (MIP) to optimality through a Branch-and-Bound solver. Given the complexity of the problem, the main drawback of both compact formulations of a MIP is certainly the very limited size of the instances likely to be solved. In order to overcome this, we propose a column gener-ation embedded in a Branch-and-bound algorithm, leading an exact Branch-and-price algorithm which has been applied successfully in the solution of large-scale problems [Lasdon, 1970; Barnhart et al., 1998].
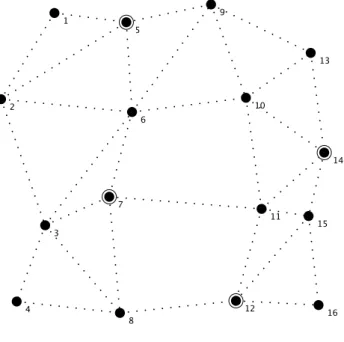
Figure 3.1 shows a RMHND example for a network with 16 nodes, two sets of nodes and edges (two different levels) and a hop constraint whereH= 9. Figure 3.1(a)
3.1. Introduction 17
(a) Original network
(b) Solution network
18 Chapter 3. Resilient Multi-level Hop-constrained Network Design
Branch-and-price algorithm is described. Section 3.5 is devoted to present the equiva-lence between two formulations for the problem. Our computational experiments are presented and discussed in Section 3.6. Finally, the conclusion and future directions are given in Section 3.7.
3.2
Related Work
The Multi-level Network Design has theoretical importance since it generalizes the well-known Steiner Tree [Chopra and Rao, 1994] problem and the Hierarchical Network Design (HND) problem - defined by Current et al. [1986], which designates exactly two nodes of the network in the first level (also referred to as primary nodes) and the others in the second level. The MLND was first introduced by Balakrishnan et al. [1994b], which describes alternative model formulations for the problem and analyzes the worst-case performance for heuristics based upon Steiner and spanning tree computations. For the HND special case with only two primary nodes, the worst-case performance ratio of the heuristic is 4/3. For the general case, the composite heuristic’s worst-case
performance ratio ofr+1depends on the worst-case performance ratiorof any Steiner
network heuristic.
By the same time, Balakrishnan et al. [1994a] have developed an optimization-based heuristic methodology for solving the MLND problem. This method first applies certain preprocessing tests to reduce the problem by eliminating or installing primary or secondary technologies before solving the problem. The core of the method consists of a dual ascent algorithm to generate good linear programming based lower bounds and heuristic upper bounds. Computational results on large-scale problems (containing up to 500 nodes and 5000 edges) show that the method provides very good approximated solutions (guaranteed to be within 0.9% from optimality).
In [Balakrishnan et al., 1998], the survivability idea is incorporated to the MLND. For this, backup paths are provided for pairs of nodes belonging to the primary level. The authors propose and analyze the worst-case performance of tailored heuristics for several special cases of the two level problem. Depending upon the particular problem setting, the heuristics have worst-case performance ratios ranging between 1.25 and 2.6.
3.3. Mathematical Formulations 19
linear programming value of the new formulation is proved to be theoretically weaker than the LP bound given by a flow based formulation, although for certain classes of in-stances the two LP bounds are quite close. In addition, a Lagrangian based relaxation is presented, where an arborescence minimization problem is solved as the relaxed sub-problem. Computational results indicate that the Lagrangian relaxation based method is quite efficient, providing a reasonable alternative to handle the problem.
As an extension of [Gouveia and Telhada, 2001], a new formulation for the Multi-Weighted Steiner Tree (a general case of TLND) problem is proposed in [Gouveia and Telhada, 2008]. In the previous work, the authors propose a non-symmetric formula-tion for the problem in the sense that depending on the node selected as a root of the tree, the corresponding LP bounds could vary. Thus, a reformulation by intersection is proposed, obtained by the intersection of feasible sets of the models corresponding to each root selection for the problem. It is shown that the linear programming relax-ation of the reformulrelax-ation dominates the linear programming relaxrelax-ation of the previous formulation for all possible root selections. They also present a Lagrangian relaxation scheme derived from the reformulation, with quite favourable results, on instances with up to 500 nodes and 5000 edges.
An optimal approach for the HND problem is devised in [Obreque et al., 2010] using a Branch-and-cut procedure. They show how to find valid cuts and how their separation works. A Branch-and-bound procedure completes the algorithm when no more cuts can be added. Computational results show that large instances are likely to be solved in a short CPU time.
To the best of our knowledge, it was not found in the literature the problem of Multi-level Network Design with hop constraints and resilience against single-edge failure, as proposed in our work.
3.3
Mathematical Formulations
Let us now formally introduce the Resilient Multi-level Hop-constrained Network Design problem. For the sake of convenience, we define our problem over a di-rected graph to allow an easier transition over the different formulations. Given a directed graph D = (N, A) with set of nodes N and arcs A, installation costs {cgij = cgji ≥ 0 : ∀(i, j) ∈ A,∀g ∈ G} assigned to the arcs of A, where G denotes the set of different technologies, numbered from 1 to |G|. A technology g on arc (i, j) costs cgij, with cgij > cgij′ if g < g′.
Let K ⊆ N ×N be a set of requests; K = S
20 Chapter 3. Resilient Multi-level Hop-constrained Network Design
requests with technology g. The technology g of a request k is defined by the lowest level of the end-nodes of k. This means that the communication for request k must take place in the highest technology between its end-nodes. The RMHND problem consists in finding a subset of arcsS ⊆A, such that each arc is assigned to exactly one
technology and the subgraph of D implied by (N, S) provides two arc disjoint paths with length at most H for each request.
Three Integer Programming Formulations for RMHND are presented here. In the first two formulations, named Arc-Flow Formulation and Aggregated Hop-Indexed Formulation, connectivity between each pair of nodes is enforced through network flow [Ahuja et al., 1993] arguments. In the third one, Arc-Path Formulation, connectivity is guaranteed by imposing that two arc disjoint paths connecting every pair of nodes must be available in the subgraph ofDimplied by the selected arcs. These formulations are discussed next.
3.3.1
Arc-Flow Formulation (AFF)
Let us assume that, given D= (N, A), A−j and A+j respectively denote the set of arcs arriving and leaving j ∈ N. To model RMHND, we make use of the following sets of decision variables: (i) xkpij ∈ R+, indicating the amount of flow of request k that
passes through arc (i, j) which composes path p ∈ {1,2}; (ii) yijg, taking value 1 if arc (i, j) = (j, i) is assigned to technology g and therefore included in the solution (0,
otherwise). RMHND can now be stated as:
min X
(i,j)∈A:i<j
X
g∈G
3.3. Mathematical Formulations 21
s.t.
X
p∈{1,2}
X
j∈A+
s
xkpsj ≥2 ∀k∈K, s=source(k) (3.2)
X
p∈{1,2}
X
i∈A−
t
xkpit ≥2 ∀k∈K, t=dest(k) (3.3)
X
i∈A−
j
xkpij − X
l∈A+
j
xkpjl = 0 ∀k∈K,∀j ∈N, j6=source(k)6=dest(k),∀p∈ {1,2}, (3.4)
X
g∈G
ygij ≤1 ∀(i, j) = (j, i)∈A, (3.5)
X
p∈{1,2}
xkpij ≤ X
g′≤g(k)
yijg′ ∀k∈K,∀(i, j) = (j, i)∈A,∀p∈ {1,2}, (3.6)
X
(i,j)∈A
xkpij ≤H ∀k∈K,∀p∈ {1,2}, (3.7)
yijg =ygji ∀(i, j)∈A,∀g∈G, (3.8)
0≤xkpij ≤1 ∀k∈K,∀(i, j)∈A,∀p∈ {1,2}, (3.9)
ygij ∈ {0,1} ∀(i, j)∈A,∀g∈G. (3.10)
Constraints (3.2)-(3.4) are flow balance constraints for each request k. Note
that inequalities(3.2) imply that at least two units of flow will leave the source node of request k, while inequalities (3.3) indicate that every unit of flow for request k
will arrive its destination node. Constraints (3.4) guarantee the flow conservation in transshipment nodes. Inequalities (3.5) assure that on each arc (i, j) ∈ A at most one of the technologies is installed. Inequalities (3.6) couple flow and design variables, imposing thatg(k)flows are only allowed to crossg′arcs (arcs with higher technologies),
where g′ ≤g(k). Note that inequalities (3.5) along with inequalities (3.6) impose that
paths p ∈ {1,2} are arc disjoint. Constraints (3.7) assure that paths implied by the flows are no longer than H. Constraints (3.8) impose whenever arc (i, j)is selected to be in a solution, so is (j, i). Finally, objective function (3.1) minimizes the total cost
of selected arcs. Note that whenever arcs (i, j) and (j, i) are included in the solution, the cost cgij is considered only once in the objective function.
Formulation (3.1)-(3.10) has O(n4)variables and constraints and therefore, only
22 Chapter 3. Resilient Multi-level Hop-constrained Network Design
3.3.2
Aggregated Hop-Indexed Formulation (AHF)
In this formulation, previous constraints (3.7) are treated by an additional index on flow variables, as proposed in [Gouveia et al., 2006], except that we do not make use of “loop” variables. Through this indexing strategy, even when we are dealing with the LP relaxation of the problem, the paths imposed by the flows are guaranteed to have no more than H hops, making the bounds stronger than in the former formulation.
In addition to variables ygij previously defined, our second formulation uses vari-ables whk
ij indicating the amount of flow of request k that crosses arc (i, j) in the hth
hop of one of the paths. Thus, the problem can be stated as:
min X
(i,j)∈A:i<j
X
g∈G
cgijyijg (3.11)
s.t.
X
j∈A+
s
wsj1k ≥2 ∀k∈K, s=source(k) (3.12)
H
X
h=1 X
i∈A−
t
whkit ≥2 ∀k∈K, t=dest(k) (3.13)
X
i∈A−
j
wijhk− X
l∈A+
j
wjlh+1k = 0 ∀k∈K,∀j∈N, j 6=source(k)6=dest(k),
h={1, ..., H−1}, (3.14)
X
g∈G
yijg ≤1 ∀(i, j) = (j, i)∈A, (3.15)
H
X
h=1
wijhk≤ X
g′≤g(k)
yijg′ ∀k∈K,∀(i, j) = (j, i)∈A, (3.16)
yijg =yjig ∀(i, j)∈A,∀g∈G, (3.17)
0≤whkij ≤1 ∀k∈K,∀(i, j)∈A, h={1, ..., H}, (3.18)
yijg ∈ {0,1} ∀(i, j)∈A,∀g∈G. (3.19)
Flow balance constraints for each requestkare given by constraints (3.12)-(3.14). Inequalities (3.12) ensure that at least two units of flow will leave the source node of requestk, indexed by the1st hop. Inequalities (3.13) guarantee that every unit of flow
for request k will arrive its destination node disregarding the number of hops used to
3.3. Mathematical Formulations 23
its arrival. Inequalities (3.15) assure that on each arc (i, j) ∈ A at most one of the technologies is installed. Inequalities (3.16) couple flow and design variables, as in the previous formulation. Note that inequalities (3.15) along with inequalities (3.16) impose that the paths implied by the flows are arc disjoint. Constraints (3.18) impose that arcs (i, j) and (j, i) are symetric. The objective function (3.11) minimizes the total cost of selected arcs, as in the Arc-Flow Formulation.
Formulation (3.11)-(3.19) also has O(n4) constraints and far more variables
(O(n5)) than the Arc-Flow Formulation. Although the LP bounds provided by this
formulation are tighter, once again, the size of RMHND instances expected to be solved is limited.
A third formulation, named Arc-Path Formulation is presented in the sequence. Despite having exponentially many variables, this formulation is suitable for the im-plementation of a Branch-and-price [Barnhart et al., 1998] method.
3.3.3
Arc-Path Formulation (APF)
In this formulation, we assume that Pk denotes the set of admissible directed paths
connecting the endpoints of requestkinD, including a hop constraint (length(p)≤H :
p∈Pk). The main idea of the Arc-Path Formulation to enforce connectivity and single
arc failure resilience is to impose that, at least two paths connecting every request in the corresponding or higher level technologies must be available in the subgraph implied by the selected assignment whose cost we aim to minimize.
Assume thatapij ∈ {0,1}indicates that arc(i, j)or(j, i)belongs to pathptaking value 1 (0, otherwise). In addition to variables ygij previously defined, we make use
of the following set of decision variables: λk
p taking value 1 if path p ∈ Pk is selected
for request k (0, otherwise). The Arc-Path Formulation for RMHND is given by the
Integer Program:
min X
(i,j)∈A:i<j
X
g∈G
24 Chapter 3. Resilient Multi-level Hop-constrained Network Design
s.t.
X
p∈Pk
λkp ≥2 ∀k∈K, (3.21)
X
g∈G
ygij ≤1, ∀(i, j)∈A:i < j, (3.22)
X
p∈Pk
apijλkp ≤ X
g′≤g(k)
ygij′, ∀k∈K,∀(i, j)∈A:i < j, (3.23)
λkp ∈ {0,1} ∀k∈K,∀p∈Pk, (3.24)
yijg ∈ {0,1} ∀(i, j)∈A:i < j,∀g∈G. (3.25)
The objective function (3.20) minimizes the total cost of the selected arcs. Con-straints (3.21) ensure that at least two paths connecting each request will be selected. Inequalities (3.22) assure that on each arc (i, j) ∈ A at most one technology is in-stalled. Inequalities (3.23) imply that g(k) paths are only allowed to cross g′ arcs,
where g′ ≤ g(k), i.e., arcs with higher technologies. Following the same idea of the
other formulations, inequalities (3.22) along with inequalities (3.23) guarantee that the selected paths are arc disjoint.
3.3.4
Considerations
For solving RMHND by a LP based BB algorithm, we have chosen the state-of-the-art commercial solver CPLEX [2011]. The advantage of the LP based BB approach is that little programming effort is needed, once one has in hand an Integer Programming solver like CPLEX.
However, the Arc-Flow Formulation and the Aggregated Hop-Indexed Formula-tion have O(n4) variables and constraints and O(n5) variables and O(n4) constraints,
respectively. Therefore, even with the help of a highly sophisticated optimization package like CPLEX, only RMHND instances of limited size are expected be solved to proven optimality by LP based BB algorithms that rely on these formulations. Conse-quently, the drawback of this approach is that, in practice, only limited size instances of RMHND can be actually solved in a reasonable amount of time.
3.4. Branch-and-price Algorithm for the RMHND 25
3.4
Branch-and-price Algorithm for the RMHND
The exponentially many columns in (3.20)-(3.25) does not refrain us to use the Arc-Path Formulation in an exact BB approach to solve RMHND. That could be attained by embedding a Delayed Column Generation in a BB algorithm.
3.4.1
Lower Bounds given by the Arc-Path Formulation
To understand how the LP bounds given by (3.20)-(3.25) are evaluated, let πk ≥ 0,
βij ≤0and γijk ≤0be the dual variables associated with constraints (3.21), (3.22) and
(3.23), respectively. The dual problem associated to the LP relaxation of (3.20)-(3.25) is given by:
maxX
k∈K
2πk+ X
(i,j)∈A:i<j
βij (3.26)
s.t.
βij−
X
g′≥g X
k∈Kg′
γijk ≤cgij ∀(i, j)∈A:i < j,∀g∈G, (3.27)
πk+ X
(i,j)∈A:i<j
apijγijk ≤0, ∀k∈K,∀p∈Pk, (3.28)
πk≥0 ∀k∈K, (3.29)
βijk ≤0 ∀k∈K,∀(i, j)∈A, (3.30)
γijk ≤0 ∀k∈K,∀(i, j)∈A. (3.31)
(3.32)
The LP relaxation of (3.20)-(3.25) can be computed as follows. Assume that sets of simple directed paths Ck ⊂ Pk,∀k ∈ K (|Ck| << |Pk|) are made available. Also,
assume that the Restricted Master Problem
min X
(i,j)∈A:i<j
X
g∈G
26 Chapter 3. Resilient Multi-level Hop-constrained Network Design
s.t.
X
p∈Ck
λkp ≥2 ∀k∈K, (3.34)
X
g∈G
ygij ≤1, ∀(i, j)∈A:i < j, (3.35)
X
p∈Ck
apijλkp ≤ X
g′≤g(k)
ygij′, ∀k∈K,∀(i, j)∈A:i < j, (3.36)
λkp ≥0 ∀k∈K,∀p∈Ck, (3.37)
yijg ≥0 ∀(i, j)∈A:i < j,∀g∈G. (3.38)
has one basic feasible solution y,ˆ ˆλ. Let π,ˆ β,ˆ γˆ be the corresponding dual optimal solution. If, for all requestsk, no path p∈Pk\Ck violates the dual constraints
ˆ
πk+ X
(i,j)∈A:i<j
apijγˆijk ≤0, (3.39)
then, y,ˆ λˆ solves the LP relaxation of (3.20)-(3.25) and the corresponding optimal LP
function gives a lower bound on (3.20). Otherwise, for a given resquest k there must
be a path inPk\Ck that violates (3.39) that must be included in Ck. The new RMP,
enlarged with the sets of paths associated to violated constraints (3.39), is re-optimized. The procedure goes on, until no inequality (3.39) is violated.
In our implementation, the initial sets Ck are generated as follows. In order to
guarantee a feasible solution for the problem, two arc disjoint paths must be provided for each requestk ∈K. Therefore, we computed the first two minimum disjoint paths
connecting requestkin terms of number of hops (seeking a feasible solution). Whenever
the length of the maximal path in the generated sets is no greater thanH, (3.20)-(3.25)
admits at least one solution. Otherwise, there is no feasible solution for the problem. The pricing problem, consists in finding a path p ∈Pk\Ck that violates (3.39)
or proving that such path does not exist. Therefore, if there is no path for any request
k ∈K yielding negative reduced costs ckp =−πˆk−P
(i,j)∈A:i<ja p
ijγˆkij, the LP relaxation
is solved. Since γˆk
ij ≤ 0,∀k ∈ K,∀(i, j) ∈ A : i < j (and therefore −ˆγijk ≥ 0),
the pricing problems could be solved by any shortest path algorithm with resource constraints (note that in fact, it is a “longest” path, since γˆk
ij ≤ 0). In order to deal
3.4. Branch-and-price Algorithm for the RMHND 27
3.4.2
The Enumeration Tree
As previously described, when no more columns with negative reduced costs are found, the associated solution corresponds to the optimal value for the LP relaxation of the root node. If the LP solution is integer, it also solves the original problem (3.20)-(3.25). Otherwise, being fractional, an enumeration algorithm is required.
One important issue in the implementation of BP algorithms is how branch-ing is performed. Since the pricbranch-ing subproblems are iteratively solved along the BP procedure, ideally, the branching rule should not destroy the structure of the pricing subproblems. In this case however, it is irrelevant, as we use an exponential algorithm to deal with the subproblems, and the complexity will not increase.
We chose to branch on fractional ygij variables. Next, we show that branching
on variables yijg will lead us to an optimal integer solution, and no branching in λk p is
needed, due to the property of elementary paths. Clearly, whenever λ∗ is an optimal
integral solution, variables y∗ will also be. Although the contrary is not true, we can
state that:
Proposition 1. Given an optimal solution λ∗, y∗ to RMHND with objective value O∗;
if y∗ is integral, λ∗ is either integral or there exists an integral feasible solution with
the same objective value.
Proof. Suppose thaty∗ is integral. LetU∗
k be the set of variablesλfor requestk having
positive values, i.e., U∗
k = {p ∈ Pk : λkp > 0}. For each request k, if |Uk∗| = 2, there
exist two non-zero variables assuming value 1, ensuring an integral solution. Otherwise (|U∗
k| > 2), one may select two variables among the elements of Uk∗ and fix them to
1 and the others to 0. It is important to point out that as the paths represented by the selected variables must be arc disjoint, the selected couple cannot share common arcs. Once variables λ∗ assume positive values, it is guaranteed that arcs belonging
to the selected paths are included in the solution (remember that y∗ is integral) and
moreover, computed in the objective function. Therefore, we can obtain an integral solution with the same objective value O∗. To demonstrate that there exist two arc
disjoint elementary paths among the elements of U∗
k for every request k, observe the
following properties of the resulting subgraph implied by the solution of RMHND. Subgraph D = (N, S) is bridgeless; otherwise, a flow of two units must be traversing the cut-edge (bridge) to guarantee the set of constraints, which is impossible since variables yijg ∈ {0,1}. Thus, we can state that D = (N, S) is a two edge connected graph. According to Menger’s theorem 1, for every pair source/destination there are
28 Chapter 3. Resilient Multi-level Hop-constrained Network Design
at least two edge disjoint paths inD.
The idea of branching on yijg variables is the creation of as many branches as
the number of technologies |G|+ 1. The first branch concerns the case in which all technologies g of arc (i, j) = (j, i) are forbidden, i.e., arc (i, j) = (j, i) is actually forbidden to belong to the solution. The other|G| branches treat the cases where one of the technologies is imposed to be 1 and the remainder 0. The main advantage of this branching rule is that it does not affect the pricing subproblem, requiring only the elimination of the corresponding arc from the input graph when necessary.
The selection of the next fractional variable to branch on is performed at random. Moreover, the Branch-and-bound tree is explored choosing a node according to abest bound policy. According to our experiments, the best bound policy presents a better
performance than the breadth first or depth first ones.
3.4.3
Stabilization and Acceleration Strategies
In order to evaluate the behaviour of our algorithm under stabilization, we apply an interior point stabilization method proposed by Rousseau et al. [2007]. The main idea of this method is to select a dual solution inside the optimal space rather than retrieving an extreme point. To obtain a point inside the polyhedron, one can simply define a random objective function and solve the associated dual problem imposing complementary slackness conditions. If the problem is solved with a simplex method, then the optimal solution obtained will always be an extreme point. Solving the dual problem for a number of random values, we obtain a set of extreme points, whose convex combinations will lead to an interior point that gives much more centered dual values. The only parameter to set is the number of points to identify in order to calculate an interior point of the dual optimal space. The trade-off is that a larger number of points will produce a more centered point, but also requires more computing time (since a LP has to be solved for each point).
Evaluating our experiments, it is observed that although the number of iterations of the procedure indeed decreases, the computational times are not improved. Different values for the number of points to be calculated were tested, but no advantage was achieved. The reason for that consists in the fact that the bottleneck of our problem is the time spent while solving the LP. Since the stabilization method is based on a number of runs of the associated dual LP, the gain obtained in the number of iterations of the column generation does not pay off the time spent to compute better dual values.
3.5. Equivalence of the LP Relaxations of AHF and APF 29
A common acceleration strategy in column generation concerns the addition of a large set of good columns in the beginning of the procedure. As presented in Section 3.4.1, the set of initial paths for each request is initialized with only two arc disjoint paths. A larger set of paths was also tested to initialize the algorithm, but according to our computational results, this strategy does not improve our current solutions.
3.5
Equivalence of the LP Relaxations of AHF and
APF
Theorem 1. The LP relaxations of AHF and APF provide the same solution set and objective function values for RMHND.
The proof for the theorem is based on showing that for each continuous solution to AHF (APF) there is a corresponding solution in APF (AHF) and both of them lead to the same continuous value for RMHND. Let F(.) be the feasible solution set for problem (.) and AHFLP and AP FLP denote the LP relaxations of AHF and APF,
respectively. Let the solutions in AHFLP and AP FLP be represented by
(w, y)≡(whk ij , y
g
ij)∀k∈K,∀h∈I,∀(i, j)∈A,∀g ∈G and
(λ,y¯)≡(λk p,y¯
g
ij)∀k∈K,∀p∈Pk,∀(i, j)∈A:i < j,∀g ∈G,
respectively. For (w, y) ∈ F(AHFLP) and (λ,y¯) ∈ F(AP FLP), consider ZAHF(w, y)
and ZAP F(λ,y¯) the corresponding linear objective function values of AHF and APF,
respectively.
Proof. The equivalence of F(AHFLP) and F(AP FLP) and the equality of the continuous
solutions of AHFLP and AP FLP are shown in three parts.
Part 1. To show F(AP FLP) ⊆F(AHFLP), we take a solution(λ,y¯)∈ F(AP FLP) and
construct a solution (w, y)∈ F(AHFLP).
Letbhpij be a binary constant assuming value1if arc(i, j)is theh-th arc belonging
to path p and 0, otherwise. It is easy to see that the binary constant apij presented in
APF can be given by
apij =X
h∈I