Inimitability of Fingerprint for Establishment of
Identity
Samayita Bhattacharya 1, Kuntal Barua 2, Kalyani Mali 3,
1, 2, 3Department of Computer Science & Engineering
University of Kalyani, Kalyani, West Bengal, India
Email-1samayita.bhattacharya@gmail.com,2kuntal.barua@gmail.com, 3kalyanimali1992@gmail.com
Abstract-To uniquely identify a single person, different types of information can be used with other sources. This concept is ancient, and it has become much more important as information technology and the Internet have made it easier to collect identifiable documents. In this paper we have discussed different types of identify documents and their merits and dis-merits eventually proving that fingerprint is unique, inimitable and easier to access.
Keywords: Biometric, Fingerprint, Identification, Unique, AFIS.
1-INTRODUCTION
Identity is to establish the identity of a person, or to ascertain the origin, nature, or definitive characteristics of a particular person. Personally Identifiable Information (PII), as used in information security, refers to information that can be used to uniquely identify, contact, or locate a single person or can be used with other sources to uniquely identify a single individual. The following data, often used for the express purpose of distinguishing individual identity:
• Full name (if not common) • National identification number • IP address (in some cases) • Vehicle registration plate number • Driver's license number
• Face, fingerprints, or handwriting • Credit card numbers
• Digital identity • Birthday • Birthplace
• Genetic information
The following are less often used to distinguish individual identity, because they are traits shared by many people. However, they are potentially PII, because they may be combined with other personal information to identify an individual.
• First or last name, if common • Country, state, or city of residence • Age, especially if non-specific • Gender or race
• Criminal record
To uniquely identify a person, the recent trend is to use biometric. Different biometric features can uniquely identify a person unless there are identical twins. In case of identical twins many biometrics fail to distinguish them as separate person, but fingerprint still can distinguish as two different persons. In recent technology more than one biometric feature is also being used in a combination to have more robust indentifying system. Several research projects have shown that multimodal biometrics (e.g. fingerprints and voiceprints combined) can improve the performance and the reliability of biometric authentication.
2. Different Identification Techniques
2.1. Names
People can be identified by an assigned or innate form of classification. One example is the name of their family, or surname which can indicate those persons to whom they are related. The surname may also provide information about their background or the geographic area in which their ancestors lived. The first, or given, name provides a unique identifier that distinguishes one person from other members of the same family. Names and surnames often tell about the geographic belonging, and culture of the person. Surnames and given names may also provide information about some of the person’s physical features. Names like Rudy, Edward, Steve, and Bill are male names, just as Joyce and Jane are female names. It would not be unreasonable to assume that someone named Steve is a man, and thus a mental framework or picture of that person would begin to develop.
Names themselves, then, provide some information about a person that may be useful in helping to make identification. In addition to sex and size, there are other features that may come to mind with a particular name. It may provide an indication of someone’s skin color or skin tone; height and weight might also be inferred from a name. These assumptions, however, are often incorrect. Plus, some names are ambiguous. Names are given at birth, but can be (voluntarily) changed later in life. People change their names for a variety of reasons.
2.2. Identification documents
Names provide only a casual identifier. In many situations, a person’s name is a sufficient identifier that can be recognized by another party; most will believe that the name is authentic. But when an additional degree of information is required, a form of documentation, such as a driver’s license or passport, can be used. These forms of identification are improvements over one’s name alone because they provide a unique identification number (i.e., the driver’s license number or the passport number). They are issued by a government agency that has created specific requirements for their issuance. Not all government-issued documents are equally reliable as forms of personal identification. A library card, for example, is issued by an agency of government (the county, city, or university) but is intended only to permit the bearer to borrow books, movies, and other media from a library for a limited period of time. Although a borrower may need to present a driver’s license as identification and proof of residency in order to be issued a library card, the card is an inexpensive and insecure method for the library to account for its holdings, as the value of the item borrowed is relatively minor (the price of the book, plus administrative fees and recovery costs). The library assumes that the borrowers are members of the community served by the library (residents, university students, etc.) and thus are likely to return the borrowed items in good order; this also reduces the need for a more reliable form of identification.
As the reliability of a form of identification increases, more security is involved in generating it and authenticating the person it represents. While library cards have a low level of security and require only modest proof of residency, they are only good for borrowing books from the library. A driver’s license requires stronger proof of identification (such as a birth certificate), but it has more uses than just permitting one to legally operate a motor vehicle. Not everyone is completely honest about their identity; nor is everyone completely honest about their personal history, their criminal history in particular. While a library card may be sufficient to borrow a book, other organizations, such as the airline industry, require a more authoritative form of identification. The Transportation Security Administration (TSA) requires a government-issued form of identification with a photograph, along with a boarding pass, to clear security at the airport. Simply announcing “I am John McNeil” will not convince a TSA official that John McNeil is really John McNeil, and that he is the John McNeil who has a ticket on the next flight.
Not only does driver’s license allow for the legal operation of a motor vehicle, but it also is becoming an increasingly important form of identification. To obtain a driver’s license, one of the most widely recognized forms of identification; the applicant has to present other supporting forms of identification. The driver’s license includes a feature that the other documents required to obtain it may not: a biometric, in this case, a photograph.
The driver’s license is, of course, also used for its intended purpose in verifying both the identification of a driver and his or her legal authority to operate a motor vehicle.
Closer inspection might reveal that the photo on the license does not match the driver. The license is valid, but it does not belong to the person stopped by the officer. There are many stories of individuals who obtained false driver’s licenses by bribing officials or providing false documentation, combined with social engineering (i.e., gaining trust by appearing to be a known or accepted person), which resulted in the false driver’s license being issued. From these examples, it is apparent that driver’s licenses cannot be counted on as an irrefutable form of identification.
2.4. Passport
A driver’s license provides one level of identification, at least if the photo matches the face of its holder. But the name on the license may not be the name of the individual holding the license. Do passports provide any better identification? A passport is considered to be a very secure document. To obtain a passport, the applicant must have proof of citizenship in the form of a birth certificate, Certification of Birth; a form of identification; two photographs meeting the application specifications; and money for the application fee [3]. The applicant must present these items, in person to the office. This must be done in person to ensure that the photographs can be compared by the official with the face of the applicant and that the documents are consistent in terms of name and other identification items. The Passport Services Office of the different countries may accept any of the following for the required form of identification:
• Previous passport • Certificate of Citizenship • Driver’s license
• Government ID • Military ID
These security checks are designed to ensure that the individual named on the passport is actually the person holding the passport. This usually is the case, but not always. A determined person can overcome several of these checks. For example, the photograph on the applicant’s driver’s license may not be valid, or the driver’s license itself may not be valid. As the example above showed, it is relatively easy to obtain a fraudulent driver’s license. Fraudulent passports come in all shapes and sizes, sometimes even from fictional countries or authorities. These are known as phantom passports.
2.5. Smart cards
A smart card, chip card, or integrated circuit card (ICC), is any pocket-sized card with embedded integrated circuits. Smart cards can provide identification, authentication, data storage and application processing [16].
The benefits of smart cards are directly related to the volume of information and applications that are programmed for use on a card. A single contact/contactless smart card can be programmed with multiple banking credentials, medical entitlement, driver’s license/public transport entitlement, loyalty programs and club memberships to name just a few. Multi-factor and proximity authentication can and has been embedded into smart cards to increase the security of all services on the card. For example, a smart card can be programmed to only allow a contactless transaction if it is also within range of another device like a uniquely paired mobile phone. This can significantly increase the security of the smart card.
stolen. Additionally, the data storage available on a card could contain medical information that is critical in an emergency should the card holder allow access to this. Smart cards have been advertised as suitable for personal identification tasks, because they are engineered to be tamper resistant. The chip usually implements some cryptographic algorithm.
2.6. Passwords
A password is a secret word or string of characters that is used for authentication, to prove identity or gain access to a resource (example: an access code is a type of password). The password should be kept secret from those not allowed access. In modern times, user names and passwords are commonly used by people during a log in process that controls access to protected computer operating systems, mobile phones, cable TV decoders, automated teller machines (ATMs), etc. For the purposes of more compellingly authenticating the identity of one computing device to another, passwords have significant disadvantages (they may be stolen, spoofed, forgotten, etc.) over authentications systems relying on cryptographic protocols, which are more difficult to circumvent.
2.7. Personal identification numbers (PINs)
A personal identification number (PIN) is a secret numeric password shared between a user and a system that can be used to authenticate the user to the system. Typically, the user is required to provide a non-confidential user identifier or token (the user ID) and a confidential PIN to gain access to the system. Upon receiving the user ID and PIN, the system looks up the PIN based upon the user ID and compares the looked-up PIN with the received PIN. The user is granted access only when the number entered matches with the number stored in the system. Hence, despite the name, a PIN does not personally identify the user.
2.8. Photographs
Names are not sufficient identifiers for long-term, absolute authentication. Driver’s licenses and passports are more reliable, but both are subject to tampering. Photographs, as used in photographic recognition devices or facial recognition software, may appear to provide a more reliable method of determining or confirming identification. However, photographs taken of the same individual may show changes over time. For example, Figures 1(a) and 1(b) are both photographs of same person, the first taken a few years ago (perhaps many years ago) and the second more recent.
(a) (b)
Figure 1: (a) Early Photo, (b) Later Photo
These two figures illustrate how a subject’s appearance in a photograph can change over the years. Beyond changes in appearance, such as hair color, addition or removal of glasses, facial hair, etc., there are other changes that can add to missed identifications. A change in lighting, the direction of shadows, background color or activity, or even the size of the face in relation to the background affect the accuracy of photographic recognition devices. The images that are captured in photographs are subject to changes in lighting, shadows, background, “noise” from other lighting sources, etc. For an identifier to be truly unique, however, it cannot be changed either by the owner of the identifier or governmental or cultural differences; it must remain unique for perpetuity. Fingerprints remain constant. Fingerprints are unique.
Biometrics consists of methods for uniquely recognizing humans based upon one or more intrinsic physical or behavioural traits. Currently Biometrics is one of the biggest tendencies in human identification.
Biometrics is claimed to be better than current and established authentication methods, such as Personal identification numbers (PINs), Passwords, Smart cards. Key advantages of using a biometric feature are: availability (always), uniqueness (to each person), not transferable (to other parties), not forgettable, not subject to theft, not guessable.
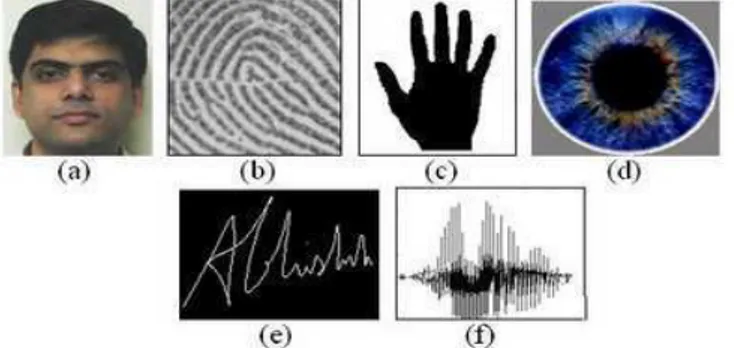
Figure2: Few Biometric characteristics that are commonly used: (a) face, (b) fingerprint, (c) hand geometry, (d) iris, (e) signature, (f) voice.
Figure 3: Various steps involved in a Biometric system
2.9.1. DNA
Mug shots and fingerprints are not the only biometrics that can be used for identification. Due to recent improvements in laboratory analysis and reduction in costs, many agencies are relying on deoxyribonucleic acid (DNA) as a form of identification. DNA is a chemical structure that forms chromosomes. A gene is piece of a chromosome that dictates a particular trait. That chemical structure can be identified through laboratory analysis. Like fingerprints, DNA does not change over time. Unlike fingerprints, however, two people can have the same DNA. Identical twins share the same DNA, but not the same fingerprints!
Large fingerprint identification services such as state identification bureaus process hundreds, perhaps thousands, of requests each day. They respond to these requests in hours, sometimes minutes. However, accommodating even a portion of that number of DNA requests would grind the identification process to a halt, as DNA identification processes require a relatively lengthy time period. In addition, some consider DNA collection to be much more personally invasive than taking a rolled set of finger images. A booking officer putting a subject’s fingers onto a glass platen to capture finger (and perhaps palm) images create a mind-set entirely different from the officer inserting a swab held by a gloved hand into the subject’s mouth. The latter procedure assumes the aura of medical analysis, an aura that can be viewed as too invasive.
Iris recognition is a method of biometric authentication that uses pattern-recognition techniques based on high-resolution images of the irises of an individual's eyes.
Iris recognition uses camera technology, with subtle infrared illumination reducing specular reflection from the convex cornea, to create images of the detail-rich, intricate structures of the iris. Converted into digital templates, these images provide mathematical representations of the iris that yield unambiguous positive identification of an individual.
Iris recognition efficacy is rarely impeded by glasses or contact lenses. Iris technology has the smallest outlier (those who cannot use/enroll) group of all biometric technologies. Because of its speed of comparison, iris recognition is the only biometric technology well-suited for one-to-many identification. A key advantage of iris recognition is its stability, or template longevity, a single enrollment can last a lifetime.
There are few advantages of using iris as biometric identification: It is an internal organ that is well protected against damage and wear by a highly transparent and sensitive membrane (the cornea). This distinguishes it from fingerprints, which can be difficult to recognize after years of certain types of manual labor. The iris is mostly flat, and its geometric configuration is only controlled by two complementary muscles (the sphincter pupillae and dilator pupillae) that control the diameter of the pupil. This makes the iris shape far more predictable than, for instance, that of the face. The iris has a fine texture that—like fingerprints—is determined randomly during embryonic gestation. Even genetically identical individuals have completely independent iris textures, whereas DNA (genetic "fingerprinting") is not unique for the about 0.2% of the human population who have a genetically identical twin. An iris scan is similar to taking a photograph and can be performed from about 10 cm to a few meters away. There is no need for the person to be identified to touch any equipment that has recently been touched by a stranger, thereby eliminating an objection that has been raised in some cultures against fingerprint scanners, where a finger has to touch a surface, or retinal scanning, where the eye can be brought very close to a lens (like looking into a microscope lens).While there are some medical and surgical procedures that can affect the colour and overall shape of the iris, the fine texture remains remarkably stable over many decades. Some iris identifications have succeeded over a period of about 30 years.
But Iris scanning is a relatively new technology and is incompatible with the very substantial investment that the law enforcement and immigration authorities of some countries have already made into fingerprint recognition. Iris recognition is very difficult to perform at a distance larger than a few meters and if the person to be identified is not cooperating by holding the head still and looking into the camera. However, several academic institutions and biometric vendors are developing products that claim to be able to identify subjects at distances of up to 10 meters. As with other photographic biometric technologies, iris recognition is susceptible to poor image quality, with associated failure to enroll rates [13]. As with other identification infrastructure (national residents databases, ID cards, etc.), civil rights activists have voiced concerns that iris-recognition technology might help governments to track individuals beyond their will.
2.9.3. Retina
A retinal scan is a biometric technique that uses the unique patterns on a person's retina to identify them. The human retina is a thin tissue composed of neural cells that is located in the posterior portion of the eye. Because of the complex structure of the capillaries that supply the retina with blood, each person's retina is unique. The network of blood vessels in the retina is so complex that even identical twins do not share a similar pattern.
Although retinal patterns may be altered in cases of diabetes, glaucoma or retinal degenerative disorders, the retina typically remains unchanged from birth until death. Due to its unique and unchanging nature, the retina appears to be the most precise and reliable biometric [17]. Advocates of retinal scanning have concluded that it is so accurate that its error rate is estimated to be only one in a million.
Retinal scanners are typically used for authentication and identification purposes. Advantagesof using Retinal scan include low occurrence of false positives, extremely low (almost 0%) false negative rates, highly reliable because no two people have the same retinal pattern, speedy results: Identity of the subject is verified very quickly [18]. Disadvantagesinclude measurement accuracy can be affected by a disease such as cataracts, measurement accuracy can also be affected by severe astigmatism, canning procedure is perceived by some as invasive, not very user friendly, subject being scanned must be close to the camera optics, high equipment costs [18][19].
2.9.4. Face
A facial recognition system is a computer application for automatically identifying or verifying a person from a digital image or a video frame from a video source. One of the ways to do this is by comparing selected facial features from the image and a facial database. It is typically used in security systems. Face recognition can be considered to be same as photograph recognition, so it lacks in many areas. Even the automated system for face recognition has lacking as photographs are highly affected by camera angle, brightness, etc. And also the face of the person changes over the time, unlike fingerprint which remains same throughout the life span of a person.
Face recognition is not perfect and struggles to perform under certain conditions. Ralph Gross, a researcher at the Carnegie Mellon Robotics Institute, describes one obstacle related to the viewing angle of the face. Face recognition has been getting pretty good at full frontal faces and 20 degrees off, but as soon as you go towards profile, there've been problems [11].Other conditions where face recognition does not work well include poor lighting, sunglasses, long hair, or other objects partially covering the subject’s face, and low resolution images [12]. Another serious disadvantage is that many systems are less effective if facial expressions vary. Even a big smile can render the system less effective. For instance: few countries now allow only neutral facial expressions in passport photos. An emerging trend uses the visual details of the skin, as captured in standard digital or scanned images. This technique, called skin texture analysis, turns the unique lines, patterns, and spots apparent in a person’s skin into a mathematical space [12]. Tests have shown that with the addition of skin texture analysis, performance in recognizing faces can increase 20 to 25 percent [11] [12].
2.9.5. Voice
Speaker recognition is the computing task of validating a user's claimed identity using characteristics extracted from their voices. Speaker verification is usually employed as a "gatekeeper" in order to provide access to a secure system (e.g.: telephone banking). These systems operate with the user's knowledge and typically require their cooperation. Speaker identification systems can also be implemented covertly without the user's knowledge to identify talkers in a discussion, alert automated systems of speaker changes, check if a user is already enrolled in a system, etc. In forensic applications, it is common to first perform a speaker identification process to create a list of "best matches" and then perform a series of verification processes to determine a conclusive match. Feeding the wrong voice cannot always be avoided in voice recognition as well as the voice capturing machine should be near to the user.
2.9.6. Signature
A signature is a handwritten (and sometimes stylized) depiction of someone's name, nickname, or even a simple "X" that a person writes on documents as a proof of identity and intent. The role of a signature is not solely to provide evidence of the identity of the contracting party, but rather to additionally provide evidence of deliberation and informed consent. Signatures can be easily falsified.
2.9.7. Palm print
A palm print refers to an image acquired of the palm region of the hand. It can be either an online image (i.e taken by a scanner, or CCD) or offline image where the image is taken with ink and paper [15].The palm itself consists of principal lines, wrinkles (secondary lines) and ridges. It differs to a fingerprint in that it also contains other information such as texture, indents and marks which can be used when comparing one palm to another. Palm prints can be used for criminal, forensic or commercial applications. The main disadvantage of palm print is that the print changes with time depending on the type of work the person is doing for a long duration of time.
Fingerprints are the graphical flow-like ridges present on human fingers. Finger ridge configurations do not change throughout the life of an individual except due to accidents such as bruises and cuts on the fingertips. This property makes fingerprints a very attractive biometric identifier. Fingerprint-based personal identification has been used for a very long time [10]. Owning to their distinctiveness and stability, fingerprints are the most widely used biometric features.
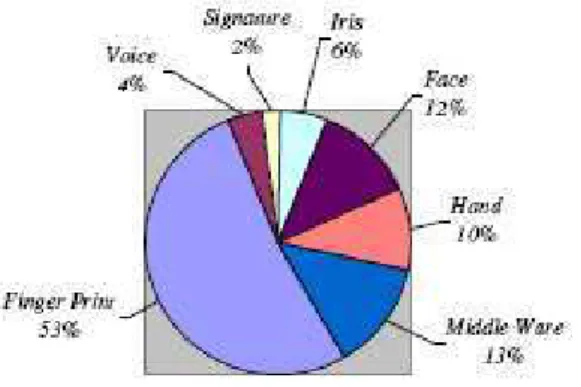
Figure 4: Biometric Market Report (International Biometric Group) estimated the revenue of various biometrics in the year 2002
3. Fingerprints
3.1. Physical characteristics
Figure 5: Finger Image
3.2 Proven uniqueness
Can it be proved that no two finger images are the same? To do that would require that every fingerprint be collected and compared. Each of the more than six billion persons on this planet, most of whom have ten fingers, would have to be fingerprinted. Those prints would build a database of approximately 60 billion images, which would then have to be searched by the ten fingers of each of the six billion people. In AFIS parlance, this is called a self-search, i.e., a portion of the database is searched against the rest of the database until the entire database has been searched against itself.
There are instances in which a person has been fingerprinted more than once and the identification is missed on a subsequent search, perhaps because of a poor-quality set of images on the database, poor-quality inked impressions, or inaccurate data entry. When these records are found, the images are reviewed by a print examiner. If the different records are of the same individual, the records are consolidated into one record. There are also instances in which identification is made on an individual whose finger images match the inquiry card, but the name (or some other characteristic) does not match. What is the true name of the subject? The identification agency can only report on the information it has on file. Large identification agencies may initiate a self-search of the database once the system is fully operational or when major improvements to the system have occurred, such as the installation of more accurate matchers (which house extracted image characteristics) that will match minutiae with a higher level of precision, or improvements to the coders (which extract features from finger images) that will more accurately find the minutiae in the finger image. For example, a few years ago a large identification agency installed new coders and new matchers, and systematically began to undertake a self-search. In searching the two index fingers of these five million records, the agency uncovered hundreds of records that had to be consolidated, some with more than ten entries for the same person. In all of those searches, however, there was not one instance in which two different persons had identical finger images. Five million records may be much fewer than six billion, but it is a good representative sample and a good test. So to the question “Can it be scientifically proved?” the response is “Not in the immediate future.” But there are other indicators. AFIS systems have been around for over 20 years. Their matchers have compared millions of finger images.
3.3 Image quality
to major pattern types such as arc, loop and whorl. Level 2 and level 3 features can be used to establish a fingerprint individuality or uniqueness. High level features can usually be extracted only if the fingerprint image resolution is high. i.e. level 3 feature extraction requires images with more than 500ppi resolution.
The characteristics of an ideal image for an AFIS search are the same as in pre-AFIS days. It should be a clear image, rolled from one nail edge to the other, using even pressure that results in an image in which the ridge shapes, deviations, and pore locations can be distinguished. The advantage with AFIS is that features such as ridge endings, bifurcations, and ridge flows can be extracted electronically by a coder in just a few seconds. These same features can be extracted identically time after time. AFIS systems can be used to search multiple fingers.
4. Experimental Data
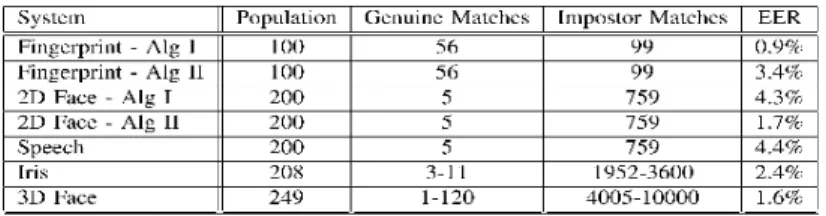
Tests are conducted by a researchers group on a variety of modalities, match algorithms, and data sets. A summary of the data sets is contained in Table 1. Fingerprints data are reported for two fingerprint matching algorithms: Fingerprint - Alg I and Fingerprint - Alg II. The matching algorithms differ only in the features used to calculate the match score. The fingerprint registration is performed using a two-stage optimization algorithm [5]. The first algorithm uses minutiae features to calculate the similarity score, and the second uses the nonminutiae features (ridge frequency, orientation, and curvature). The specific details of the iris matching algorithm and data set are not included for confidentiality reasons. The match scores for the 2D Face and Speech experiments are from the publicly available multimodal fusion benchmark database. The database contains results for a variety of different biometric algorithms for both face and speech samples. The 3D face recognition experiment uses matching algorithm that uses a two-way decomposition to break incoming faces into a number of smaller regions in both space and frequency. Each of these regions is then classified using a specialized classifier and the output of these classifiers is combined using weighted score fusion [9].
Table 1: Summary of Properties of the Experimental Data Sets “Population” specifies the number of people with both genuine and impostor match scores, and “Genuine Matches” and “Impostor Matches” specifies the number (or number
range) of matches for each person.
5. Classification Systems
For more than 100 years, fingerprint images were classified by the rules of the Henry System or the American System. The introduction of AFIS technology, however, virtually eliminated the need for fingerprint examiners to master either of these two principal systems. Identification agencies no longer invest enormous sums in training and certifying tenprint examiners in the most intricate rules for classifying finger images. Classes on the importance of these classification systems are still provided to staff, but their usefulness in everyday operations is on the decline.
One system that does remain in active use is the classification system depends on Fingerprint Classification (FPC), well known to those who do not have immediate access to AFIS, this FPC rules classify each finger of a tenprint record using a combination of patterns, ridge counts, and whorl tracing; does not search on finger images; instead reports on finger image descriptors contained in its classification system. There is no requirement for a digital camera, coder, or matcher.
The American System was developed by Captain James Parke. It was a departure from the traditional Henry System (and, interestingly, was not named after its chief proponent) by providing a different score for each finger that was repeated on each hand. While the Henry System of classification used values derived from the odd/even finger numbers, the American Classification System was based on the hand.
6. Filing Systems
The classification process used determined where the card would be physically filed, with similarly classified cards housed together. The cards were filed based completely on classification. Identification sections would have at least two fingerprint files: a master fingerprint file and a secondary file. The master file held one tenprint card per individual. Usually this was the first or original tenprint card. Assigning these records to a unique location made it easier to find and remove the physical card as well as the electronic Rap Sheet. Fingerprint cards were stored in various types of filing cabinets, including specialized rotary files that would move a tray of cards into a horizontal position for easier access. Physical cards required tremendous accountability for the location of the card. The cards themselves, being a paper product, were subject to fire, heat, humidity, and other environmental factors.
AFIS systems changed all of this. With AFIS, pattern recognition software, as well as examiners, classifies images by one of four pattern types (whorl, arch, right loop, left loop, (Figure 6)) instead of by the Henry or American fingerprint classification rules. There are no secondary classifications; there are no complicated rules. AFIS coders can determine both the pattern type and minutiae placement. In addition, with AFIS systems, fingerprint cards may or may not physically exist. If they do exist, they may be retained at an off-site facility. The images from the electronic cards can be displayed on a screen or printed onto card stock. AFIS examiners no longer have to wait for a physical tenprint card; the card information is as near as a computer terminal connected to the AFIS. The cards cannot be misfiled or subjected to deterioration due to the heat and humidity found in an office building. The information can be virtually retrieved, reviewed, and returned. There is no wasted paper and no file cabinets that must be searched through taking up space. This is one of the major advantages of AFIS.
A B C D
Figure 6: AFIS Pattern Types:(A) Arch; (B) Left Loop; (C) Right Loop; (D) Whorl
7. Soft Computing Approach
AFIS can be further made more accurate using soft computing tools. The most used fingerprint recognition system in current days depends on minutia extraction. Different soft computing tools can be used in different phases of fingerprint extraction and matching [24].
Conventional computing or often called as hard computing, requires a precisely stated analytical model and often a lot of computation time. Many analytical models are valid for ideal cases, and real world problems exist in a non-ideal environment. Soft computing differs from conventional (hard) computing in that, unlike hard computing, it is tolerant of imprecision, uncertainty, partial truth, and approximation. In effect, the role model for soft computing is the human mind. The guiding principle of soft computing is: Exploit the tolerance for imprecision, uncertainty, partial truth, and approximation to achieve tractability, robustness and low solution cost. Soft computing may be viewed as a foundation component for the emerging field of conceptual intelligence. Few soft computing tools are: Fuzzy Systems, Neural Networks, Evolutionary Computation, Machine Learning and Probabilistic Reasoning.
Most of the fingerprint recognition systems rely on minutiae matching algorithms. Although minutiae based techniques are widely used because of their temporal performances, they do not perform so well on low quality images and in the case of partial fingerprint they might not be used at all. Therefore, when comparing partial input fingerprints to pre-stored templates, a different approach is needed. Soft computing can help to achieve better result for these types of case. For extracting features, for minutia, rotational invariant features are also very important.
REFERENCES
[1] David R. Ashbaugh, “Quantitative–Qualitative Friction Ridge Analysis”. [2] http://www.valawyersweekly.com/terrorist.htm.
[3] http://travel.state.gov/passport/index.html.
[4] http://www.wtopnews.com/index.php?nid=25&sid=98856.
[5] N. Yager and A. Amin, “Fingerprint Verification Using Two Stage Optimization,” Pattern Recognition Letters, vol. 27, pp. 317-324, 2006. [6] http://onin.com/fp/level123.html.
[7] http://www.leds.state.or.us/resources/ncic_2000/ncic_2000_code_manual.htm. [8] Michael Harling, “Origins of the New York State Bureau of identification”.
[9] J. Cook, V. Chandran, and C. Fookes, “3D Face Recognition Using Log-Gabor Templates,” Proc. British Machine Vision Conf., 2006. [10] A. Almansa and L. Cohen, “Fingerprint image matching by minimization of a thin-plate energy using a two-step algorithm with auxiliary
variables,” in Proc. IEEE 5thWorkshop Applications Computer Vision, Dec. 2000, pp. 35– 40.
[11] Williams, Mark. "Better Face-Recognition Software". http://www.technologyreview.com/Infotech/18796/?a=f. 2008-06-02.
[12] Bonsor, K.. "How Facial Recognition Systems Work". http://computer.howstuffworks.com/facial-recognition.htm. Retrieved 2008-06-02. [13] Zhaofeng He, Tieniu Tan, Zhenan Sun and Xianchao Qiu, "Towards Accurate and Fast Iris Segmentation for Iris Biometrics", In: IEEE
Transactions on Pattern Analysis and Machine Intelligence (TPAMI), 15 July 2008. IEEE Computer Society Digital Library. IEEE Computer Society, 2 September 2008.
[14] N. Poh and S. Bengio, “Database, Protocol and Tools for Evaluating Score-Level Fusion Algorithms in Biometric Authentications,” Pattern Recognition, vol. 39, no. 2, pp. 223-233, 2005.
[15] Zhang, D. (2004). ‘’Palmprint Authentication’’, Kluwer Academic Publishers.
[16] Rankl, W.; W. Effing (1997). Smart Card Handbook. John Wiley & Sons. ISBN 0-471-96720-3.
[17] Retina and Iris Scans. Encyclopedia of Espionage, Intelligence, and Security. Copyright © 2004 by The Gale Group, Inc. [18] Hill, Robert. “Retina Identification”. Msu.Edu.
[19] Roberts, Chris. "Biometrics" Retrieved on 2009-06-11.
[20] K. Karu and A.K. Jain, “Fingerprint Registration,” Research Report, Michigan State Univ., Dept. of Computer Science, 1995.
[21] A. K. Jain, L. Hong, S. Pankanti, and R. Bolle, “An identity authentication system using fingerprints,” Proc. IEEE, vol. 85, no. 9, pp. 1365– 1388, Sep. 1997.
[22] A. K. Jain, L. Hong, and R. Bolle, “On-line fingerprint verification,” IEEE Trans. Pattern Anal. Mach. Intell., vol. 19, no. 4, pp. 302–314, Apr. 1997.
[23] X. Jiang andW. Yau, “Fingerprint minutiae matching based on the local and global structures,” in Proc. 15th Int. Conf. Pattern Recognition, vol. 2, Barcelona, Spain, Sep. 2000, pp. 1042–1045.