Swindler Ingress Point Detection by Real Time
Recognition of Transfer Characteristics
P. M. Dhanrao
Department of Computer Technology K. B. P. Polytechnic, Kopargaon, Maharashtra, India
Asso. Prof. Ketan Singh
Department of Computer Science and Engineering MTRI, Bhopal, M.P., India
Asso. Prof. Prajeet Sharma
Department of Computer Science and Engineering MTRI, Bhopal, M.P., India
Abstract- In this paper we have introduced more influential techniques are to identify swindler IPs and to get better network flexibility. Here an proficient swindler IP protection system termed as SIP for uncovering of any scam in wireless communication. This system intended has nice properties: it requires neither dedicated hardware nor change to existing standards; the planned mechanism can be incorporated with an IP in a plug in manner; it provides a cost efficient safety development to Wi-Fi networks by incorporating free but full-grown software tools; it can guard the network from adversaries competent of using adapted equipment and violating the IEEE 802.11 standard.
Keywords – Swindler Ingress Point
I. INTRODUCTION
It is the avoidance of unlawful access or harm to computers using wireless networks. Wireless networks are very common, both for organizations and persons. Many laptop computers have wireless cards pre-installed. The capability to go in a network while mobile has great profit. However, wireless networking has many safekeeping issues. Crackers have establish wireless networks relatively simple to break into, and even use wireless technology to crack into wired networks. As a result, it's very significant that enterprises define successful wireless safety policies that watch against unofficial access to vital resources.
One of the most difficult safety concerns for network managers is the attendance of swindler wireless ingress points. A swindler ingress point (SIP) is a wireless ingress point that has either been installed on a safe company network exclusive of explicit approval from a local network administration or has been created to allow a cracker to behavior a man-in-the-middle attack. The swindler ingress points are plans that are deployed in secure WLANs without agreement or knowledge of the network superintendent. The attendance of such swindler ingress point poses severe fear to the WLAN safety as it could give and take safety of the entire wireless LAN. This trouble has been in existence ever since WLANs have become accepted in profitable applications. There have been information of data theft, identity theft by using these swindler ingress points. Growing use of wireless technologies by defense establishments along with above mentioned reasons have forced researchers all over the world to find a key for this problem. WLANs facade the same safety challenges as their wired counterparts, and more.
Within a properly tenable WLAN, swindler ingress points are more destructive than swindler users. Illegal users annoying to access a WLAN likely will not be victorious at reaching precious corporate possessions if effective verification mechanisms are in place. Major issues happen, however, when an employee or hacker plugs in a swindler ingress point. The swindler ingress point helps an attacker in gaining admission to responsive information of an organization.
In order to keep away from this circumstance, it is needed to apply safety policies that mandate conformance with successful safety controls and synchronization with the network manager previous to installing ingress points. This can only be successful, however, if you evidently inform workers of the policies. After the stage several safety audits, it has been originate that workers often set up swindler ingress points without knowing the company safety policies or the penalty of violating the strategy. A hacker can set up a swindler ingress point to supply an open, non-secure line to a business network. In order to do this, the hacker has to unswervingly attach the ingress point to an active network port within the capability. This requires the hacker to pass from side to side physical safety; however, that's easy to do in most companies. So there is an vital need of developing skill which will speak to this problem of swindler ingress points.
With the rising fame of Wi-Fi networks, securing such a network becomes a difficult problem. Service Wi-Fi networks are largely pathetic to attacks because of factors such as release medium, not enough software implementations, possible for hardware deficits, and inappropriate configurations. Among all the safety threats, one of the most risky hazards is the occurrence of swindler IPs. A swindler IP is naturally referred to as an unlawful IP in the literature. This type of tool can be easily deployed by end-users. When a swindler IP is related to a network, it can be used by adversaries for committing spying and launching attacks. Similarly, inappropriately configured IPs and phishing IPs can initiate the same safety threats once broken by adversaries. Therefore, they can be regarded as swindler IPs as well. More importantly, there is a more insidious type of swindler IPs, called the compromised IPs, that has drawn little attention in the literature. A compromised IP is the most unsafe swindler IP that can exist in product Wi-Fi Networks. In particular, it is hard to detect such a swindler device because the IP itself is not out of order (e.g., operating without particular safety controls).
Table 1. Classification of swindler IPs.
Swindler IPClass probable Scenarios
inappropriatelyConfigured inadequate safety knowledge; defective driver; physically defective; manifold network cards Unauthorized associated to internal LAN without
authorization; outside neighborhood IP
Phishing fabricated by opponent
Compromised revelation of safetycertificate
Additional, the IP does not display irregular misconduct such as distribution a duplicate SSID. Thus, a compromised IP can considerably diminish the overall safety of the system. A synopsis of the types of swindler IPs and a amount of possible scenarios is shown in Table 1 for a detailed taxonomy of swindler IPs.
We first give a complete classification of swindler ingress points (IPs), which includes a new class of swindler IPs by no means addressed in the journalism before.
Further, the IP does not show irregular misbehavior such as broadcasting a copy SSID. Thus, a compromised IP can considerably diminish the on the whole safety of the network. A synopsis of the types of swindler IPs and a number of possible scenarios is shown in Table 1 for a detailed classification of swindler IPs.
We first give a comprehensive taxonomy of swindler ingress points (IPs), which includes a new class of swindler IPs never addressed in the literature before.
The rest of the paper is organized as follows. Proposed Swindler Ingress Point Detection algorithms are explained in section II. Experimental results are presented in section III. Concluding remarks are given in section IV.
II. PROPOSED ALGORITHM A. Swindler Ingress Point Detection algorithm –
enlightening their attendance. These mechanisms can be implemented on an IP or on split plans that connect to the IP in a plug-in manner [6]. It is significant to think network presentation when making the above conclusion. On a supply constrained IP, the overall network service could be tarnished when all three mechanism are implemented on it. The facts of each component are described in the following subsections.
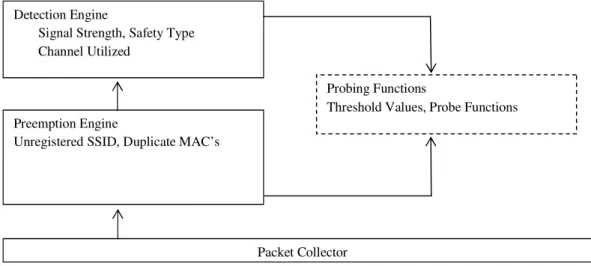
Figure 1. Proposed SIP Detection Model
1.1 System background
The type of Wi-Fi set-up that we believe uses WEP or WPA in grouping with MAC address filtering. This grouping of features is rampant in commodity Wi-Fi networks. Additionally, we try to avoid rekeying behavior, as they require significant slide. An case of such a network is the one used by the Department of Computer Science at The George Washington University. Even though there are about 20 to 30 lively users every day, there are over 600 registered users.
1.2 Packet Collector
A packet collector is required for real-time WLAN monitoring so that swindler wireless devices can be rapidly known, and network managers notified when suitable. One advantage of a packet collector is its natural capability to split wired and wireless travel.
Thus, there is no need for complex modules that effort to isolate the two by examining transfer signatures. 1.2.1 Information compilation from packets
The packet collector needs to have a network device that runs in immoral mode at all times. The entire region of interest can be enclosed with the support of wireless range extenders. One of the packet collector's duties is to imprison all network traffic. In order to quantify the storage overhead, we conducted a test using our department (802.11b/g compatible) Wi-Fi network. The test consisted of a single 802.11b client using ftp to download a large file from a local server. We approved out the test in the middle of the night so that there would be no argument from other wireless clients. The average transfer rate recorded over many trials was about 2.2 Mbps. Therefore, by recycling the composed data every one hour, the storage slide can be limited to about 1 Gigabyte. This is a sound overhead for even low-end computing tools.
1.3 Preemption Engine work flow
Whilst attempted network attacks cannot be avoided, it is possible to put off some attacks earlier than they occur. In exacting, a certain amount of information has to be collected by an opponent before an assault can actually occur. The punctual detection of such action can help prevent an awaiting attack. Subsequently, a swindler IP preemption engine is built-in with SIP. The swindler IP preemption engine of SIP is our first line of protection.
The basic objectives of this constituent are to catch sniffers and prevent activity that can lead to IP compromise. Probing of potential eavesdroppers and network integrity checks are performed to achieve these goals. The former is intended to find out passive spectators while the latter is used to avoid a rightful IP from being compromised. 1.4 Probing criteria over parameters
In exacting, messages are occasionally generated that, when replied to, make known the attendance of a sniffer. One type of note is an ARP request. If a potential attacker is "inactively listening" to the network travel and replies to one of the trap ARP requests, her attendance will be exposed. The gap selected for broadcasting these frames reflects
Detection Engine
Signal Strength, Safety Type Channel Utilized
Preemption Engine
Unregistered SSID, Duplicate MAC’s
Probing Functions
Threshold Values, Probe Functions
a transaction between accessible bandwidth use and time wanted for discovery. These parameters can be modified based on the capabilities of the fundamental systems.
1.5 Attack Preemption
After obtaining data from the packet collector, the swindler IP preemption engine will carry out the checks outlined below. By preempting attacks that could make known the top secret network key, we prevent the formation of Class 4 swindler IPs.
1) Unregistered MAC addresses are for the moment stored together with their location in order. This is because an attacker might disclose its MAC address to the IP before the information of a lawful MAC address is acquired. The place information can be obtained by localization schemes planned in the literature (e.g., [20]). Naturally, such localization schemes need 3 to 4 base stations (or IPs in our container) with identified locations. This prerequisite is simply pleased in service Wi-Fi networks.
2) Carbon copy MAC addresses are for the time being removed from the MAC clean so that network contact is left without. This can happen when an assailant spoofs a MAC address to that of a customer that is at present linked. The position of any station using this MAC address will be made existing by the IPs. If one of the locations matches that of a earlier unregistered MAC address, the spot of the assailant is identified [9].
3) The crowd of management frames (e.g., DE authentication frames) will be observed as many active attacks rely on the broadcast of forged frames. Though it has been recommended in that management frames in 802.11i be genuine, the WEP and WPA protocols do not bear this functionality. Thus, the preemption engine wants to keep a proof of all organization frames that the IP sends out. By doing this, the broadcast of a spoofed management frame to a client can be detected, and the IP can decide not to react to requests from that scrupulous client. For example, in order to open a dictionary attack on the common key used in a WPA-PSK enabled network, an attacker wants to imprison the four verification frames exchanged between a client and the IP [7]. To do this, an assailant may send out a spoofed de-authentication note to a client to power the client to re-authenticate to the IP. In this case, the IP refuses to carry out the confirmation process with the client. Thus, the assailant is prevented from capturing the frames required to start on a brute-force attack on the key.
As a balance to the above three tactics, a warning note can be sent to the system manager when a spoofed MAC address or a forged management frame is detected. Yet, there are some cases where an assailant might go ignored by our preemption system. For example, the assailant might decide to use the passive listening techniques described in above Section. The assailant could also trail lawful MAC addresses for use at a later on time. Once the assailant has acquired the secret key, the MAC address of a lawful but currently not present client can be used. Since these types of activities may go unnoticed by our integrity check module, SIP includes the swindler IP detection capabilities described in the next subsection.
1.6 Detection Engine
There are two primary reasons for the swindler IP detection engine. First, defensive against Class 1 -3 swindler IPs is an naturally reactive course. For example, there is no means to stop an assailant from setting up a phishing IP outside of a confidential organization. Secondly, a complicated opponent may be able to avoid the preemption techniques for Class 4 swindler IPs. The swindler IP detection engine is accountable for discovering swindler IPs in spite of of what class they fit in to. For Classes 1-3, the IP probing method described in Section below is used to attract swindler IPs into enlightening their attendance. Class 4 swindler IP’s are detected by first identifying travel from an unlawful user. Extra mechanisms are incorporated for treating adversaries that are strong sufficient to use hardware that violates the 802.11 customary. An IP advertises its attendance a number of times per second by distribution special frames that take its SSID called beacons. Stations be able to realize an IP by passively listening for beacons, or by transmitting a search request message to actively look for for an IP with a particular SSID. Our detection engine uses lively honey pot functionality to find out swindler IPs by sending out probe requests. It is competent of detecting the primary three classes of swindler IPs.
There is a universal misconception that disabling the "Broadcast SSID" trait hides the SSID. In actuality, disabling this feature only makes the IP broadcast a null (zero-length) SSID in beacon frames and probe responses in its place of the its actual SSID. There are at rest several other frames (e.g., probe requests, organization requests, and re-association needs) that carry the SSID. Hence, it is unworkable to remain an SSID value undisclosed without physically reconfiguring device drivers or hardware to infringe the 802.11 standard. So, a particular IP can be exposed as of its probe responses. The next step is to determine whether or not it is a swindler 3 Examples of active honey pot systems contain Strider Honey Monkeys and the Honey client Project IP.
(e.g., 11 channels in 802.11b). This asset increases the possibility of a swindler IP being detected because any IP that hears the demand will send a search response back to SIP. In this reply, information such as the MAC address has to be included, even though the SSID may not be there.
If the reported MAC address matches an unregistered MAC address bring into being during an truth check, we can bring to a close that it belongs to a swindler IP. in conclusion, SIP can have the switch port that is connected with the swindler IP's MAC address closed to get rid of it from the network. In the event that a swindler IP spoofs a legitimate IP's MAC address and SSID, location information ought to be used to make a decision. If an IP announces a legitimate MAC address, but has localization results that are contradictory with those in the location table, it can be calculated to be a swindler IP. SIP also handles great cases where swindler IPs has had their driver and/or firmwares customized in such a means that neither beacon frames nor probe reply frames are transmitted. As a effect, there is no MAC address in sequence available to draw a winding up.
Yet, a disassociation message can be sent to a client of the expect IP based on the flow information composed by the packet collector. While the client sends out a re-association demand, the MAC address and SSID of the IP will be disclosed. Note that the above method can prevent an adversary with a level of strength that has by no means been understood before. In exacting, other work such as and (assume that an assailant does not have the ability to violate uniqueness of the 802.11 standard).
Although this statement is sensible in many cases, the defense of any organization based on it can be undermined. SIP does not place this restriction on the capabilities of the opponent. Hence, it is able to give both robust and comprehensive guard from swindler IPs.
II. EXPERIMENT AND RESULT
Then analysis for swindler ingress point can be determined in graphical form as given below,
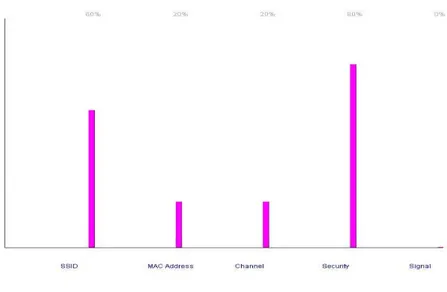
Figure 2. One SSID is registered for IP Out of 4 (25%)
As proposed algorithm is continuously scanning for all the ingress points available, the graphical representation after iteration of cycle will be change and the percentage of traffic form the every ingress point with packets is analyzed. So depending upon traffic and parameters registered, system analyzing whether the ingress point is swindler or its authorized point. After 25 scans of cycles of iteration that is loop is repeated, means system scans for ingress point. The graph will change for each ingress point when it compute the percentage values for SSID, Mac Address, channel and safety with signal. For complete demonstration signal parameter was not registered. But it can be included to increase the efficiency of the system.
P
er
ce
n
ta
g
e
o
f
T
o
ta
l
A
u
th
o
ri
ze
d
P
ar
am
et
er
s
in
n
et
w
o
rk
The test set for this evaluation experiment watermark image randomly selected from the internet. Matlab 7.0 software platform is use to perform the experiment. The PC for experiment is equipped with an Intel P4 2.4GHz Personal laptop and 2GB memory.
Figure 3. Result after 25 Scans
Hence form above discussion it is clear that we can find the unauthorized IP by using only 4 parameters in effective and faster fashion. And you also can take the help of other parameters required for make the faster decisions and more effective system. But it again ingress the system overheads and decrees the network performance
Table -2Experiment Result
MAC Address SSID Channel Security Signal Type
DETECTION ENGINE PREEMPTION ENGINE THRESHOLD
Registered Unregistered Known Known Correct Authorized
Unregistered Registered Known Known Correct Authorized
Registered Registered Unknown Unknown Incorrect Authorized
Unregistered Registered Unknown Unknown Incorrect Unauthorized
Unregistered Unregistered Unknown Unknown Incorrect Unauthorized
Unregistered Unregistered Known Known Correct Unauthorized
Registered Unregistered Unknown Known Correct Authorized
Unregistered Unregistered Known Known Incorrect Unauthorized
Registered Unregistered Known Known Incorrect Authorized
Unregistered Registered Known Known Correct Authorized
Registered Unregistered Known Unknown Incorrect Unauthorized
IV.CONCLUSION
Wi-Fi networks from swindler IPs called SIP. A striking feature of SIP is that it requires neither dedicated hardware nor adjustment to existing security standards. Further, the projected means can be associated to or implemented on IPs as small plug-in. It also makes use of freely obtainable mature software in order to supply a cost-effective security solution. Lastly, SIP can defend networks from swindler IPs even when presumptuous that adversaries have the capability to use custom-made equipment that violates the IEEE 802.11 standard. SIP is the primary system that can productively protect the system under that supposition. As a part of our opportunity work, we plan to deploy SIP on a test Wi- Fi network.
REFERENCES
[1] Liran Ma Department of Computer Science The George Washington University Washington, DC 20052, USA lrma@gwu.eduRAP: Protecting Commodity Wi-Fi Networks from Swindler Access Points
[2] M. A. Maloof. Machine Learning and Data Mining for Computer Security: Methods and Applications (Advanced Information and Knowledge Processing). Springer-Verlag New York, Inc., Secaucus, NJ, USA, 2005.
[3] P. Mateti. Hacking techniques in wireless networks.
[4] M. Raya, J.-P. Hubaux, and I. Aad. Domino: a system to detect greedy behavior in ieee 802.11 hotspots. In MobiSys '04, pages 84-97. ACM Press, 2004.
[5] D. Schwab and R. Bunt. Characterising the use of a campus wireless network. In INFOCOM, 2004.
[6] Y.-M. Wang, D. Beck, X. Jiang, R. Roussev, C. Verbowski, S. Chen, and S. T. King. Automated web patrol with strider honeymonkeys: Finding web sites that exploit browser vulnerabilities. In NDSS, 2006.
[7] J. Yeo, M. Youssef, and A. Agrawala. A framework for wireless lan monitoring and its applications. In WiSe '04, pages 70-79. ACM Press, 2004.
[8] Nmap: Network mapper.
[9] p0f: a versatile passive os fingerprinting tool.
[10] A. Adya, P. Bahl, R. Chandra, and L. Qiu. Architecture and techniques for diagnosing faults in ieee 802.11 infrastructure networks. In MobiCom '04, pages 30-44. ACM Press, 2004.
[11] P. Bahl, R. Chandra, J. Padhye, L. Ravindranath, M. Singh, A. Wolman, and B. Zill. Enhancing the security of corporate wi-fi networks using dair. In MobiSys '06, pages 1-14. ACM Press, 2006.