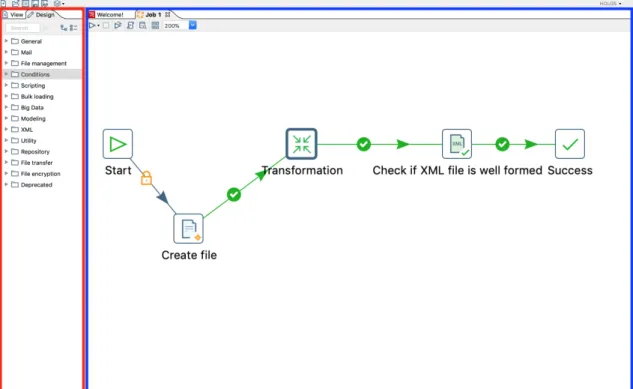
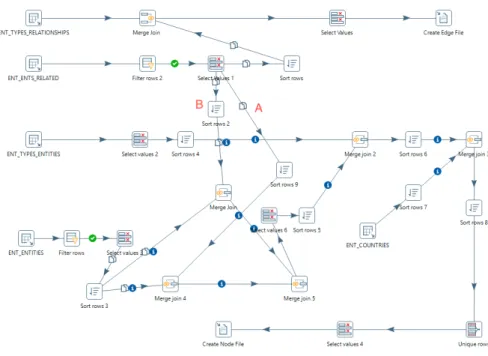
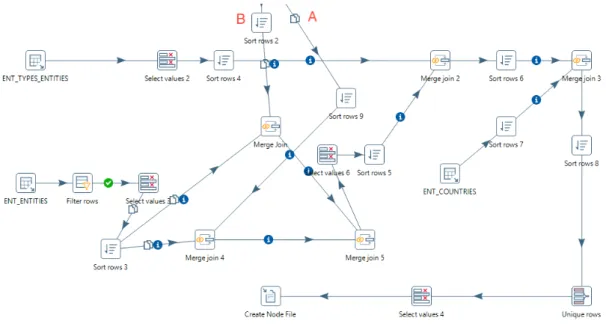
Insurance Fraud Detection - Using Complex Networks to Detect Suspicious Entity Relationships
Texto
Imagem
![Figure 2.1: Survey performed upon Australian organizations identifying basic fraud control and prevention techniques by PricewaterhouseCoopers Economic Crime Survey 2007 [12]](https://thumb-eu.123doks.com/thumbv2/123dok_br/15194349.1017263/36.892.173.773.426.805/performed-australian-organizations-identifying-prevention-techniques-pricewaterhousecoopers-economic.webp)


Documentos relacionados
Eles podem não escrever ali o que é, mas ouvir alguém falar, o pai falou isso, a mãe falou aquilo, daí você também não pode dizer a mãe não sabe, o pai não sabe, você já
A regulação do crescimento é complexa e multifatorial, sendo os fatores genéticos fundamentais para determinação do potencial do crescimento, porém com uma interface múltipla
Disse que não conversa muito com o pai, só com a mãe Perguntei o motivo de ele conversar pouco com o pai, ele disse: “meu pai é muito sério, quase não fica em casa
F ullerman está à espera… «Não só foste eleito para o conselho escolar, como também alcançaste a MAIOR PONTUAÇÃO DE SEMPRE no teste da semana passada.. Agora, o Marcus
O Partido Republicano Riograndense (PRR) esteve no poder do Estado do Rio Grande do Sul por quase 40 anos, tendo como principais líderes Júlio Prates de Castilhos e
A mãe devemos eterna alegria e gratidão Não importa seu sexo, se é “pai-mãe”.. Sentimentos de ser mãe, não importa em
・ Lar de pai ou mãe solteiro(a) ou mora no lar pessoa com deficiência(a própria criança, pai, mãe, irmãos), lar que se enquadra para pagar imposto municipal (pai e mãe
FAMÍLIA SECRETA DE ORAÇÃO 2 | A relação com o cardápio do almoço para o encerramento da Família Secreta de Oração já está com Anne (Cerimonial da SAF). Todas
![Table 3.3: Some of the most relevant metrics regarding complex networks [52].](https://thumb-eu.123doks.com/thumbv2/123dok_br/15194349.1017263/71.892.108.757.576.1019/table-relevant-metrics-regarding-complex-networks.webp)