Vol. 2(5), 2010, 1473-1484
A novel cryptographic technique under
visual secret sharing scheme for binary
images
B. Lakshmi Sirisha G. Sree Lakshmi
Lecturer, M.Tech Student
V.R. Siddhartha Engineering College V. R Siddhartha Engineering College Email: suravarapuls @yahoo.co.in Email: srilakshmialapati @yahoo.com
ABSTRACT- The traditional cryptographic techniques require decryption algorithm to decode the original information. This process requires computations and further increases cost of equipments making the technique inefficient. This paper briefly presents the visual cryptographic technique applied to image so that decryption can be performed by human visual system, without any decryption algorithm. A visual cryptography scheme encodes a black & white secret image into n shadow images called shares which are distributed to the n participants. The VC scheme is based on the no. of the shares and participants. The paper projects a new matrices with different shares and participants namely (3,6) & (4,4). The proposed scheme reduces the complexity by reducing the no. of shares with increased participants. This feature of the scheme improves the efficiency and makes the decoding system easy by printing out shadow images on transparencies and stacks them to visually reveal the secret image. The proposed scheme is developed using Matlab. The results are presented to validate the effectiveness of the proposed scheme. Keywords: Visual cryptography, visual secrete sharing, shares, participants
INTRODUCTION
To prevent digital contents from being intercepted by unauthorized parties is a critical demand in information security. With the increasing popularity of the internet, which makes possible the instant access or distribution of digital contents, such a demand becomes even more significant. Traditional cryptographic skills recommend plenty of solutions by encrypting the digital data into a cipher text that cannot be recognized by illegal intruders. Yet the decryption of the protected cipher text needs computations. Generally peaking, the cost or efficiency of the hardware/software performing the decoding computations is mostly proportional to the security of the encryption algorithm. Thus, when we demand a stronger security, the decoding devices/computations become more costly or inefficient.
than the grey level of a ”reconstructed” white one. In other words, the reconstructed image will be darker than the background of the image itself. In such a model [3], [4], [5] the recovered secret image can be darker or lighter than the background.
The organization of the paper as follows: Section I briefly gives the introduction and previous work related to the proposed work. Section II explains the visual secret sharing scheme.
II. VISUAL SECRET SHARING SCHEME
Introduction: In 1994, Naor and Shamir proposed a new technique called visual cryptography. The primary property of visual cryptography is using a method called stacking shares to recover secret messages. Stacking refers to layering the shares on top of one another. The secret owner or a dealer creates two or more shares for the secret message. Each cannot be used to reveal the secret alone. Receiving all of the shares, printing each share onto a transparency, stacking the transparencies and using human visual system, the secret message can be visible without any computation needed. In this way, visual cryptography has proven to provide perfect security. Furthermore, the technique can be applied to group secret system, which is using (k, n)-threshold visual secret sharing scheme in order to perform secret sharing, where k≤n. With (k, n)-threshold visual secret sharing scheme, the dealer or the secret owner can base a group of n participants to produce n shares for the secret message. Each participant in the group can have his own share. When recovering the secret message, only k or more transparency stacks are required without any computation. The secret message cannot be restored if less than k transparencies are used. Each pixel in the secret image is expanded to four sub pixels in each share that consist of white and black according to the patterns. The summary points of Naor and Shamir’s scheme
(1) The secret data can be divided into n parts. (2) Any k or more than k parts can recover the secret
3) Any k -1 or fewer than k parts cannot compute the secret data.
Fig.1: Naor and Shamir‘s visual cryptography model
II B. Visual cryptography scheme for binary Images-Implementation of ‘2 out of 2’ scheme:
Vol. 2(5), 2010, 1473-1484
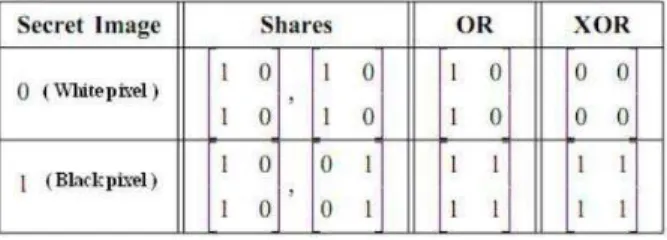
belongs to the corresponding share image. In the decryption process the two corresponding shares are stacked together (using OR operation) to recover the secret pixel. Two share of a white secret pixel are of the same while those of a black secret pixel are complementary.
As Shown in Figure 1. Consequently a white secret pixel is recovered by a share with the stacked result of half white sub-pixels and a black secret pixel is recovered by all black. Using this basic VCS Scheme we can-not completely recover the white Secrete pixel which causes loss in contrast. In XOR based VCS scheme where the share images are superimposed using XOR operation which results in perfect reconstruction of both Black and white pixels as shown in Figure 2 and sub sampling a 2×2 share into a single pixel we get decrypted image of the same size as original secret image.
Fig.2: Comparison between OR and XOR based VCS
Example for 2 out of 2 scheme
Fig 3(a): original binary image
Fig 3 (b) share1 Fig 3 (c) share2
Fig 3 (d) Decrypted image using OR operation
Fig 3 (e) Decrypted image using XOR operation
2 out of 2 sharing matrixes:
S0=
1
0
0 1
S00 =0 1
1
0
S1=1 0
1 0
S11 =0 1
0 1
S0,&S00 are complimented matrixes to reveal the black pixel, where as S1&S11 are same matrixes to reveal the white pixels. Using above matrixes we can produce 2 shares Individual shares cannot give any information. Two shares are stacked we can reveal the original output.
IIC. Possibilities for 2 out of 4 sharing scheme:
S0=
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
S1=
0
0
1
1
1
1
0
0
0
1
1
0
1
0
0
1
Using above matrixes we can produce 4 shares. Out of these 4 any two shares are stacked we reveal the original output less than two shares can not reveal any information.
II D. Possibilities for 3 out of 3 sharing scheme
S0=
1
1
0
0
1
0
1
0
0 1
1
0
S1=
1 1
0
0
1 0 1
0
1 0
0
1
Using above matrixes we can produce 3 shares. Only all shares are stacked we can reveal the original output.
III. PROPOSED VISUAL SHARING SCHEME
A. Possibilities for 3 out of 6 sharing scheme:
S0=
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
S1=1
1
0
0
1
1
0
0
1
1
0
0
1
1
0
0
1
1
0
0
0
0
1
1
Vol. 2(5), 2010, 1473-1484
S0=
1 1
0
0
1 0 1
0
1 1
0
0
1 0 1
0
1 1
0
0
1 1
0
0
S1=
1
1
0
0
1
0
1
0
1
1
0
0
1
0
1
0
1
1
0
0
0
0
1
1
S0=
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
S1=
0
0
1
1
0
0
1
1
0
0
1
1
0
0
1
1
0
0
1
1
1
1
0
0
S0=
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
S1=
1
1
0
0
1
1
0
0
1
1
0
0
1
1
0
0
1
1
0
0
0
0
1
1
S0=
1 1 0 0
1 1 0 0
1 1 0 0
1 1 0 0
1 1 0 0
1 1 0 0
S1=
1
1
0
0
1
1
0
0
1
1
0
0
1
1
0
0
1
1
0
0
0
0
1
1
Using above matrixes we can produce 6 shares. Out of these 6 any three shares are stacked we reveal the original output less than three shares we can not reveal any information
.
B. Possibilities for 4 out of 4 sharing scheme:
s
0=0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
S1=
0
0
1
1
1
1
0
0
1
1
0
0
1
1
0
0
S0=
0 0 1 1
0 0 1 1
0 0 1 1
0 0 1 1
S1=
1
1
0
0
1
1
0
0
1
1
0
0
0
0
1
1
S0=
1 1 0 0
1 1 0 0
1 1 0 0
1 1 0 0
S1=
0
0
1
1
0
0
1
1
0
0
1
1
1
1
0
0
Using above matrixes we can produce 4 shares. Only all shares are stacked we can reveal the original output. .
IV. (K, N) - THRESHOLD VISUAL CRYPTOGRAPHY
A (k, n)-threshold visual cryptography scheme is a method to encode a secret image into n shadow images called shares. Such that any K or more K shares enable the “Visual” recovery of the secret image, but by inspecting less than K shares one cannot gain anyinformation on the secret image. The “visual” recovery consists of xeroxing the shares on to transparencies, and then stacking them. Any K shares will reveal the secret image without any cryptographic computation.
V. RESULTS
Case Studies:
a) An image with 512x512 pixels is taken for validating the scheme. Results for (2,2) scheme are shown in figs 4 b-d.
Fig 4(a): Original image Fig4 (b) Share1
original image
Vol. 2(5), 2010, 1473-1484
Fig4(c) Share2 Fig4 (d) stacked shares image
b)An image with 512x512 pixels is taken for validating the scheme. Results for (2,4) scheme are shown in figs 5 b-h.
Results for (2, 4) scheme:
Fig5 (a) OriginalImage Fig5 (b) Share1
Fig5(c) share2 Fig5 (d) Share3
share2
original image
share1
share2 share3
Fig5 (e) Share4 Fig5 (f) Stacked 1&2 shares
Fig5 (g) Stacked 3&4 shares Fig5 (h) Stacked1&2&3&4 shares
c) An image with 512x512 pixels is taken for validating the scheme. Results for (3,3) scheme are shown in figs 6 b-e.
Results for (3, 3) scheme
Fig6 (a) Original image Fig6 (b) Share1
share4
over lapped 12
over lapped image over lapped image
original image
Vol. 2(5), 2010, 1473-1484
Fig6 (c) Share2 Fig6 (d) Share3
Fig6 (e) Stacked 3 shares
d) An image with 512x512 pixels is taken for validating the scheme. Results for (3,6) scheme are shown in figs 7 b-j.
Results for (3, 6) scheme:
Fig7 (a) Original image Fig7 (b) Share1
share1
share3
over lapped image
original image
Fig7 (c) Share2 Fig7 (d) Share3
Fig7 (e) Share4 Fig7 (f) Share5
Fig7 (g) Share6 Fig7 (h) Stacked 1&2&3 Shares
Fig7 (i) Stacked 3&4&6 shares Fig7 (j) Stacked 5&2&1 shares
e) An image with 512x512 pixels is taken for validating the scheme. Results for (4,4) scheme are shown in figs 4 b-f.
share3 share3
share4
share5
share6
over lapped image
over lapped image
Vol. 2(5), 2010, 1473-1484
Results for (4,4)scheme
Fig8 (a) Original image Fig8 (b) Share1
Fig8 (c) Share2 Fig8 (d) Share3
Fig8 (e) Share4 Fig8 (f) Stacked all shares
VI. CONCLUSION
This paper presented a new visual sharing scheme with (3, 6) and (4, 4) for visual cryptography. The proposed scheme reduced the no. of shares for more participants compared to equal shares and participants proposed earlier papers. As the no. of shares is reduced, system complexity is reduced. Decoding becomes easy with less no. of shares.
original image
share1
share2
share3
share4
VII. ACKNOWLEDGEMENT
We wish to express our profound thanks toDr.K.SRI RAMAKRISHNA, PhDHead of the department E.C.E,and Dr.K.MOHAN RAOprinciple of V.R.Siddhartha Engineering College for providing necessary facilities to make this project success. We wish to express special thanks to S.N.V.GANESH Assistant professor of EEE Department.
VIII. REFERENCES
[1] M. Naor, A. Shamir, Visual cryptography, in: Eurocrypt’94, Lecture Notes in Computer Science, vol. 9 50, 1994, pp. 1–12. [2] A. Shamir, How to share a secret, Communications of ACM 22 (11) (1979) 612–613.
[3] W.-G. Tzeng and C.-M. Hu, a New Approach for Visual Cryptography, Designs, Codes and Cryptography, Vol. 27, No. 3, pp. 207– 227, 2002
[4] Visual Cryptography Schemes with Optimal Pixel ExpansionCarlo Blundo, Stelvio Cimato, and Alfredo De Santis
[5] A Secret Sharing Scheme for Image Encryption Rastislav Lukac and Konstantinos N. Plataniotis 46th International SvmDosium Electronics in Marine. ELMAR-2004. 16-18 June 2004. Zadar. Croatia.
[6] Zhi Zhou, Gonzalo R. Arce , and Giovanni Di Crescenzo, “Halftone Visual Cryptography”, IEEE Transactions on image processing, vol. 15, no. 8, August 2006.
[7] Randomness in secret sharing and visual Cryptography schemes Annalisa De Bon, Alfredo De Santis Theoretical Computer Science
314 (2004) 351 – 374.