Universidade de Aveiro Departamento de Eletrónica,Telecomunicações e Informática
2020
João Tiago
Cruz Branquinho
Um sistema eficiente para aumentar a segurança em
passadeiras
An efficient alert system for improving crosswalks’
Universidade de Aveiro Departamento de Eletrónica,Telecomunicações e Informática
2020
João Tiago
Cruz Branquinho
Um sistema eficiente para aumentar a segurança em
passadeiras
An efficient alert system for improving crosswalks’
security
Dissertação apresentada à Universidade de Aveiro para cumprimento dos requisi-tos necessários à obtenção do grau de Mestre em Engenharia de Computadores e Telemática, realizada sob a orientação científica do Doutor André Zúquete, Pro-fessor auxiliar do Departamento de Eletrónica, Telecomunicações e Informática da Universidade de Aveiro, e do Doutor Carlos Senna, Investigador no Instituto de
o júri / the jury
presidente / president Prof. Doutor Joaquim João Estrela Ribeiro Silvestre Madeira Professor Auxiliar da Universidade de Aveiro
vogais / examiners committee Prof. Doutor Pedro Miguel Alves Brandão
Professor Auxiliar da Faculdade de Ciências da Universidade do Porto
agradecimentos /
acknowledgements This work is the culmination of seventeen years of blood, sweat, and tears. Duringthis educational path, multiple people helped me reach my goals. This is for all the ones that left their mark.
First of all, I would like to thank both Professor André Zuquete and Carlos Senna. For sharing their long knowledge of the academic world. For their constant avail-ability. For keeping my head on track from the many distractions and doing it with their particular good mood.
To my closest friends. Thank you for the discussions, the laughs, the everyday lessons, the growing up together, and, especially, for putting up with my crankiest days.
To my family, father, and sister. For the valuable lessons, the long laughing meals, the nostalgic vacations, and for being a part of me.
Palavras Chave Criptografia, Comunicação Segura, Redes Veicular, VANET, Assinaturas Digitais, Autenticação Eficiente
Resumo Uma das características chave das cidades inteligentes é a possibilidade de redu-zir os conflitos físicos existentes entre os diferentes agentes que coexistem neste sistema dinâmico. Um dos exemplos é a interação entre peões e veículos. Esta dissertação descreve um sistema que visa aumentar a consciência do condutor do veiculo relativamente à presença de peões nas passadeiras das redondezas. Para responder a esta necessidade o sistema liga Road Side Units (RSUs), que tem in-formação sobre o estado de ocupação da passadeira, e os veículos, desta forma espalhando para os veículos o estado de ocupação das passadeiras. Para prevenir que falsas informações sejam disseminadas, as RSUs assinam as mensagens que enviam, permitindo a todos os veículos que validem estas assinaturas. Este cenário impõe fortes requisitos de segurança, por exemplo o não repúdio das mensagens de alerta, bem como requisitos de tempo real, como por exemplo tempos de vali-dação das mensagens reduzidos que entre veículos que estejam a aproximar-se da passadeira de interesse. Tendo por base estes requisitos, o sistema procura reduzir o recurso a cifras assimétricas, que são fundamentais para garantir o não repúdio mas têm elevados tempos de validação, e vale-se maioritariamente de cifras simé-tricas para garantir a autenticação do emissor da mensagem. Para garantir estes requisitos, foi desenvolvido um protocolo, a que chamámos de Nimble
Keywords Criptography, Secure Communication, Vehicular Network, VANET, Digital Signa-tures, Efficient Authentication
Abstract A key characteristic of Smart Cities is the ability to reduce conflicts between differ-ent agdiffer-ents coexisting in a dynamic system, such as the interaction between vehicles and pedestrians. This dissertation describes a system to augment the awareness of vehicle drivers regarding the presence of pedestrians in nearby crosswalks. To address this need, the system interconnects Road Side Units (RSUs), which are informed about the state of the crosswalks, and vehicles, in order to spread to ve-hicles the information about the presence of pedestrians in crosswalks. To prevent false information spreading, RSUs sign the alert messages they broadcast and all vehicles can validate the signatures. This poses strong security requirements, such as non-repudiation of alert messages, as well as strong real-time requirements, such as minimum message validation delays among vehicles approaching a crosswalk of interest. Because of this, the system minimizes the usage of asymmetric ciphers, which are fundamental to assure non-repudiation but increase performance penal-ties, and uses mostly symmetric ciphers for source authentication. To do so, we designed a new protocol, called Nimble Asymmetric Cryptography (NAC), which
Contents
Contents i
List of Figures v
List of Tables vii
Acronyms ix
1 Introduction 1
1.1 Context and Motivations . . . 1
1.2 Objectives and contributions . . . 2
1.3 Structure . . . 3
2 Fundamental concepts 5 2.1 Vehicular ad-hoc networks (VANETs) . . . 5
2.1.1 Architecture . . . 6
2.1.2 Communication Types . . . 6
2.1.3 Radio Communication Standards . . . 7
2.1.4 VANET characteristics . . . 8
2.2 Cryptography . . . 9
2.2.1 Asymmetric cryptography . . . 9
2.3 Digital Signatures . . . 13
2.3.2 Edwards-curve Digital Signature Algorithm - EdDSA . . . 15
2.3.3 Digital Certificate . . . 16
2.3.4 Public key infrastructure . . . 17
2.3.5 Symmetric cryptography . . . 18
3 Related Work 23 3.1 VANET message authentication protocols . . . 23
3.2 Security requirements . . . 23
3.2.1 Message Authentication Code based authentication schemes . . . 24
3.2.2 Hash Function based authentication schemes . . . 25
3.3 Guy Fawkes protocol . . . 26
3.4 Tesla . . . 28
3.5 TESLA++ . . . 29
4 Proposal 33 4.1 The Nimble Asymmetric Cryptography protocol . . . 33
4.1.1 Anchor Message . . . 35 4.1.2 Hash Message . . . 36 4.2 Security analysis . . . 37 4.2.1 Attacker model . . . 38 4.2.2 Replay Attack . . . 38 4.2.3 Pre-image Attack . . . 38
4.2.4 Message Falsification Attack . . . 39
4.3 Proposed use case . . . 39
4.3.1 Message Content . . . 40
4.3.2 Protocol improvements . . . 41
4.3.3 Message Dissemination . . . 43
5 Implementation & Integration 45 5.1 SUMO . . . 46 5.1.1 OSM - OpenStreetMap . . . 46 5.1.2 NET Files . . . 47 5.1.3 NETEdit . . . 47 5.1.4 TRIPS Files . . . 48 ii
5.1.5 Routes File . . . 48
5.1.6 FCD File . . . 49
5.1.7 CFG File - Simulation visualization . . . 49
5.2 Connectivity Aggregation Tool . . . 50
5.3 Automation . . . 52
5.4 mOVERS Simulation Tool . . . 52
5.4.1 API Management Module . . . 53
5.4.2 Communication Modules . . . 53 5.4.3 Logging Module . . . 54 5.4.4 Storage Module . . . 55 5.4.5 Neighboring Module . . . 56 5.4.6 Routing Module . . . 56 5.4.7 Movers changes . . . 57 5.5 Crypto Tool . . . 60 5.5.1 Hash Function . . . 60 5.5.2 Asymmetric Cryptography . . . 61 5.5.3 Message Structure . . . 62 6 Results 65 6.1 Test Environment . . . 65 6.2 Performance Evaluation . . . 66 6.2.1 Message Size . . . 66 6.2.2 Validation times . . . 67
6.3 Mobility Test Scenarios . . . 69
6.3.1 Radio Environment Occupancy . . . 70
6.4 Scenario Evaluation . . . 72
6.4.1 Mobility Scenario . . . 72
6.4.2 Mean vehicle warning distance . . . 74
6.4.3 Problematic Crosswalks . . . 76
6.5 Message Loss Scenario . . . 77
7 Conclusion & Future Work 79
List of Figures
2.1 VANET communication types[6] . . . 7
2.2 European standard of the VANET radio frequency spectrum [10] . . . 8
2.3 Certification Chains . . . 17
2.4 Graphical representation of three critical characteristics of hash functions [25] . . 19
2.5 MD5 Compression Function . . . 20
2.6 SHA-1 Compression Function . . . 21
2.7 SHA-2 Compression Function . . . 21
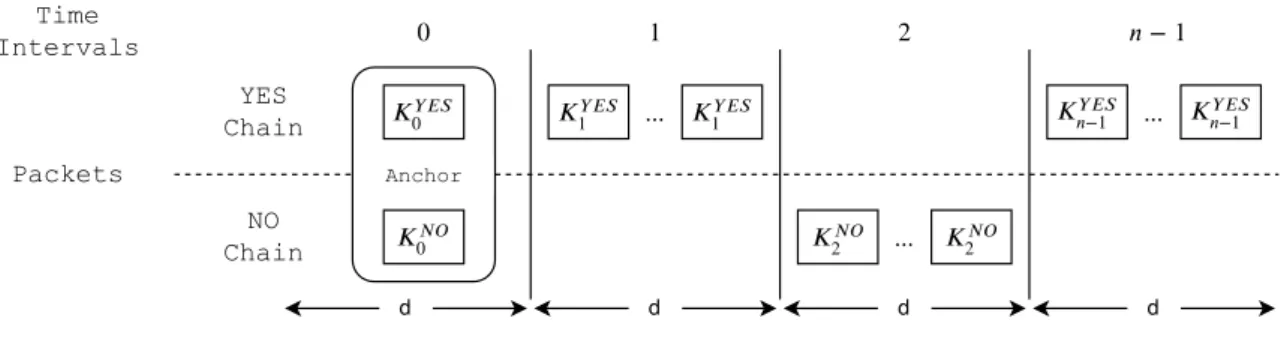
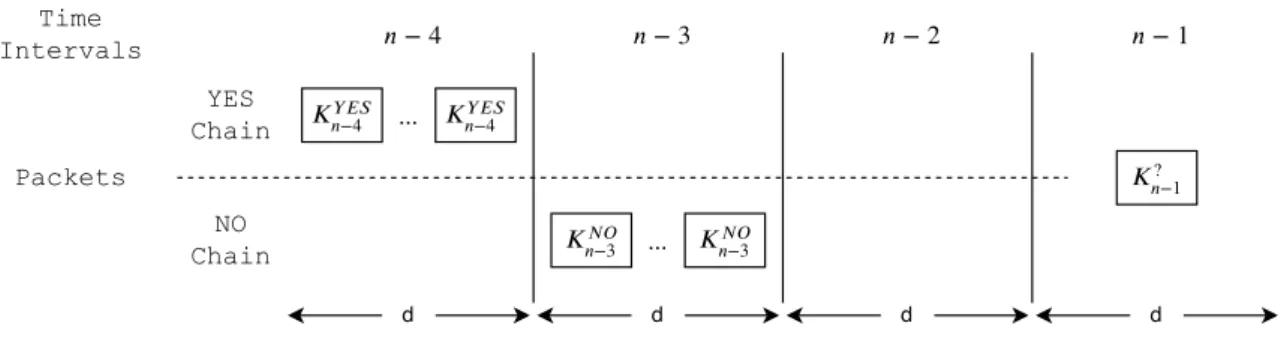
3.1 Sequence of packages in the Guy Fawkes protocol. Pm i and Pi+1m are messages and Piv and Pi+1v are message’s hashes (validations); . . . 27
3.2 Key chain creation and definition. Each key is only valid if used in particular time intervals i . . . . 28
3.3 TESLA protocol execution for each message sent. . . 29
3.4 TESLA++ execution . . . 30
4.1 The NAC protocol execution pattern . . . 34
4.2 Recipient validation process. Upon receiving a message . . . 35
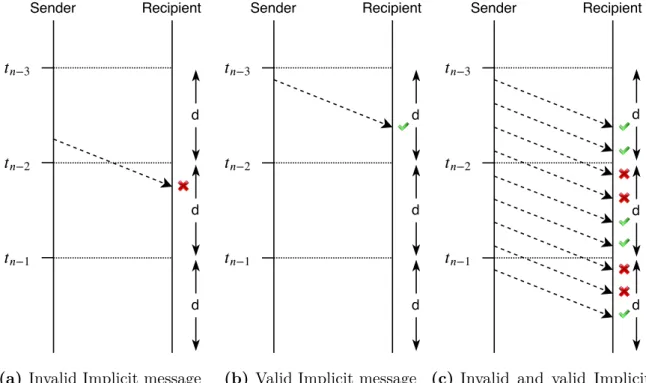
4.3 Time restrictions to Implicit messages validity . . . 37
4.4 Anchor update process. The anchor message includes the keys regarding the previous validity interval . . . 41
4.5 Braking distances, using different friction coefficients, different reaction timings and different velocities . . . 44
5.1 Software testbed platform [11]. . . 45
5.2 Several radio signal power functions. RSSI as a function of distance . . . 51
5.3 mOVERS Macro architecture [54]. . . 53
5.4 Logging module procedure flowchart . . . 54
5.5 Node class types . . . 56
5.6 Neighboring classes . . . 56
5.7 Node class types . . . 57
6.1 Evolution of message size x number of crosswalks. . . 66
6.2 Evolution of validation time x number of crosswalks. . . 68
6.3 Comparison of Anchor message validation against Implicit message validation. . 68
6.4 Visual representations of the part of Aveiro used in our tests. . . 69
6.5 Representation of the used crosswalks (red marks). . . 70
6.6 Number of messages per second using different dissemination intervals and varying the number of RSUs . . . 71
6.7 Scenario depicting crosswalks in red circles and RSU in blue squares. . . 73
6.8 Graphical depiction containing medians, minimums, maximums, and second and third quartiles of the warning distances of the vehicles . . . 74
6.9 Inclusion of RSU 3 . . . 77
6.10 Message loss using a validity interval of 200ms, a message dissemination time of 50ms, and the scenario depicted in Figure 6.9a . . . 78
List of Tables
5.1 Crypto++ hash functions performance. . . 60
5.2 OPENSSL hash functions performance. . . 60
5.3 Crypto++ signing performance on an AMD Opteron Processor 4238 3.3 GHz processor . . . 61
5.4 Crypto++ signature verification performance on an AMD Opteron Processor 4238 3.3 GHz processor . . . 62
6.1 Testbed hardware configuratuion. . . 65
6.2 Time parameters used to perform test results . . . 73
6.3 Valid message percentage . . . 75
Acronyms
CAT Connectivity Aggregation Tool
CA Certificate Authority
CRL Certificate Revocation List
DoS Denial of Service
DSA Digital Signature Algorithm
DSRC Dedicated Short Range Communication
ECC Elliptic Curve Cryptography
ECDSA Elliptic Curve Digital Signature Algorithm
EdDSA Edwards-curve Digital Signature Algorithm
EPL Eclipse Public License - v 2.0
FCD Floating Car Data
GS Group Signature
ITS Intelligent Transportation System
ITSGAC Institute of Transportation Systems at the German Aerospace Center
JSON JavaScript Object Notation
MAC Message Authentication Code
MANET Mobile Ad-hoc Network
mOVERS mobile Opportunistic Vehicular Emulator for Real Scenarios
NAC Nimble Asymmetric
Cryptography
OBU On-Board Unit
OCSP Online Certificate Status Protocol
OSM Open Street Map
PKI Public Key Infrastructure
POI Point of Interest
RAISE Roadside Unit Aided Message Authentication Scheme
RSSI Received Signal Strength Indicator
RSU Road Side Unit
SUMO Simulation of Urban MObility
TEAM Trust-Extended Authentication Mechanism
TESLA Timed Efficient Stream Loss-tolerant Authentication)
VANET Vehicular Ad-hoc Network
WAVE Wireless Access in Vehicular Environments
1
Introduction
Vehicular networks offer a variety of useful services that provide a better user experience and a functional interaction between the vehicles and the city. Vehicle manufacturing companies are already implementing functionalities like assisted driving, city congestion minimization, in-vehicle internet connection and more. One of the big topics being discussed is city interaction. There are a lot of interesting scenarios to explore, i.e. like the state of traffic lights, crosswalks, emergency messages and information sensors (humidity, temperature etc.). Moreover, city-vehicle interactions become crucial when
considering life or death situations like crosswalks.
In this section, we will discuss the motivation and context that led to the development of this dissertation.
1.1 Context and Motivations
Nowadays, road safety is a big concern among country governments. In Portugal, for example, in the year of 2017 there where a total of 34,416 traffic accidents. These accidents resulted in a total of 43,893 injured people and 602 deaths. Of those 34,416 accidents, 5651 involved pedestrians 42.7% of which happened in signalled crosswalks [1]. These statistics show that a significant chunk of road accidents happen on pedestrian signalled crosswalks. As described earlier, crosswalks are already a case study in vehicular networks. Researchers have found ways of detecting the presence of people in them or about to cross them. The problem with these studies is that the vast majority has no concern for message security. If no messages include security measures, such as cryptographic authentication processes, any third party can impersonate another and disclose unfaithful and unreliable information. Therefore the whole system may be compromised if a third party decides to cause chaos. Moreover, in Vehicular Ad-hoc
Network (VANET) environments, the network topology changes very rapidly, and network connections are intermittent due to reduced contact times. In order to deal with these problems, it is crucial that existing solutions are efficient and resilient to message loss.
This dissertation focuses mostly on two aspects: 1. how to inform vehicles about the presence of pedestrians in a crosswalk in a secure fashion 2. how to assure that vehicles can validate that information using a very efficient method. This way the purpose of this dissertation is the secure dissemination of emergency messages, more specifically the presence of pedestrians on a crosswalk, taking into account the challenges of mobile networks like frequent service failure and changes in the network topology. Moreover we focus on efficiency so that the overhead caused by packet validation and dissemination is minimized. This allows the network to proper interact with its agents in a secure way.
1.2 Objectives and contributions
Smart cities are a new reality, and an important branch of smart cities are Vehicular Ad-Hoc Networks (VANETs), where interconnected vehicles interact among themselves, with citizens and with the city itself.
The goal of our work is to help car drivers to get alerts relatively to the presence of pedestrians in a crosswalk they are heading to. For reaching this goal, we assumed that crosswalks have a trustworthy pedestrian detection system, which they use to gather information to convey to a nearby Road Side Unit (RSU). This information is then spread along a variety of vehicles of interest in the neighborhood of the source crosswalk using the VANET formed by the vehicles themselves. To prevent false information spreading, alert messages broadcast by RSUs must be authenticated, and all vehicles (or their On-Board Units (OBUs)) must validate them. This poses strong security requirements, such as non-repudiation of alert messages, as well as strong real-time requirements, such as minimum message propagation delays among vehicles approaching a crosswalk of interest. Thus, in this crosswalk-vehicle interaction scenario, maximizing efficiency while maintaining safety requirements is mandatory. Considering that RSUs and OBUs must perform several parallel tasks, such as (i) maintaining an Internet connection, (ii) control of car sensors and (iii) driver assistance mechanisms, the authentication procedure can not be a burden.
The Wireless Access in Vehicular Environments (WAVE) is a communication pro-tocol widely used in VANETs. For routing services, WAVE makes use of asymmetric cryptography in order to guarantee both authenticity and non-repudiation [2]. However, asymmetric cryptography, which is computationally more intensive than symmetric
cryptography, impacts the validation process of messages [3]. This is particularly true when used in vehicles’ OBUs, given they have limited processing power [3]. Conse-quently, it is associated to delays and to the degradation of applications related with emergency braking signaling [4]. Considering the crosswalk scenario, we propose a solution mainly based on symmetric ciphers for origin authentication. Our proposal still uses asymmetric ciphers, which are fundamental to guarantee non-repudiation, but minimizes its usage to decrease performance penalties.
As a result of this work a scientific paper entitled “Smart crosswalks: a safe alert system that minimizes the confrontation between vehicles and pedestrians” was presented in International Conferences On ICT, Connected Smart Cities 2019.
1.3 Structure
The present dissertation is structured in seven main chapters. Following we present a brief description of each one.
1. Chapter 2 - Fundamental Concepts - This chapter provides the reader an overview analysis and description of the fundamental concepts related with Cryptography and Vehicular Ad-hoc Networks.
2. Chapter 3 - Related Work - This chapter provides a comprehensive review on authentication schemes over VANETs. In such networks, the mobility of the nodes is a significant challenge along with the network resources constraints such as CPU and memory usage and network congestion. Moreover, we emphasize the protocols that better adapt to crosswalk authentication usage.
3. Chapter 4 - Proposal - This chapter presents the proposed authentication system. The protocol is presented agnostically of any specific application, given that it has a broader application range than just the crosswalk scenario in hand.
4. Chapter 5 - Implementation and integration - This chapter describes the de-sign, implementation, and integration procedures of the proposed authentication protocol.
5. Chapter 6 - Results - This chapter describes the evaluated scenarios, the equipment and platforms used in the evaluation and the main results.
6. Chapter 7 - Conclusion and Future Work - This chapter contains the conclusions related to the developed work and also points for possible improvements and future guidelines to continue researching the topic of content distribution in vehicular networks.
2
Fundamental concepts
Smart cities are becoming a vital topic for today societies. The interaction between the city with both vehicles and pedestrians allows for better and safer ecosystems involving both citizens and the city infrastructure. Therefore, there are many parties interested in the development of this topic, namely governments, municipalities, car industry and even the citizens. Moreover, this innovative process in nowadays’ cities needs to be accompanied by security measures that provide a safe environment for all the parties involved. In this chapter, we detail and contextualize the reader with some of the technological topics that are required to better understand the state of the art of both smart cities and secure systems. Among some of the detailed topics are:
1. General VANET concepts, such as the architecture, communication types, radio standards and overall characteristics;
2. Introductory concepts to symmetric and asymmetric cryptographic solutions.
2.1 Vehicular ad-hoc networks (VANETs)
VANETs are spontaneously created networks composed by vehicles and the city infras-tructure (sensors and network support devices). Vehicular networks first appeared at the beginning of the millennium and have been a subject of study since then. Nevertheless, the whole vehicle communication revolution process is yet to occur. Standards are under constant evolution, and technologies are under improvement.
VANETs are a special case of a Mobile Ad-hoc Networks (MANETs); and, as such, are very unpredictable networks. Contributing to unpredictability are characteristics such as the city’s topology, vehicle’s velocity and network infrastructure.
In this section, we will elaborate on this broad topic of vehicular communication. Moreover, we will focus on the characteristics, device types, communications types, and radio communication standards of Vehicular Ad-hoc Networks.
2.1.1 Architecture
In the VANET communication environment, there are different types of devices that incorporate the ecosystem. The primary system’s components of VANETs are OBUs and RSUs. Typically, RSUs are responsible for hosting services that OBUs will subscribe. The RSU usually hosts a service-providing application. Following, we present the key characteristics of RSUs:
• The RSUs are part of the city infrastructure.
• RSUs are devices, similar to OBUs, yet usually with more computational power, spread along roadsides or in strategic locations, such as junctions or crosswalks. It is important to notice that, such as OBUs, RSUs are equipped with different types of networking interfaces (WAVE, Wireless Fidelity (Wi-Fi) and cellular). • Among other, some of its responsibilities are (i) extending the OBUs connection
range by routing their packets to other OBUs in different whereabouts, (ii) con-necting OBUs with the city’s infrastructure (sensors, information servers, etc), (iii) providing Internet connectivity to OBUs, (iv) allowing distant OBUs to
communicate with each other, serving as a router and (v) running safety and emergency applications that warn vehicles of all types of information, such as traffic, accident warnings or working zones, crosswalk occupancy, etc. [5].
The OBU, on the other hand, is a peer device that uses the services that RSUs provide. Following we present the key characteristics of OBUs:
• OBUs are integrated in each vehicle and responsible for relaying its information to the VANET;
• They are equipped with several types of communication interfaces, such as WAVE, Wi-Fi, and cellular. This allows them to communicate through a large variety of means and to be compatible with multiple communication devices;
• An OBU is responsible for wireless radio access, ad-hoc and geographical routing, network congestion control, reliable message transfer with other OBUs and RSUs, data security and IP mobility. Similarly to regular computers, an OBU contains CPU, internal memory (both volatile and non-volatile), and a user interface.
2.1.2 Communication Types
VANET networks allow for different types of communications, depending on the source and destination of the messages:
Figure 2.1: VANET communication types[6]
• V2V communication - This type of communication occurs when vehicles ex-change messages only among themselves and not with the infrastructure. Vehicles can use multi-hop communication to ensure that the message arrives at the desig-nated vehicle. This type of communication can be used in applications related with security or geographical data dissemination. There are interesting practi-cal applications for this: (i) warnings upon entering intersections or departing highways; (ii) hazardous location warning (obstacle discovery, reporting accidents, etc.); (iii) sudden stop warnings (forward collision warning, pre-crash sensing or warning, etc.); and (iv) privileging ambulances, firefighting vehicles, and police cars [7].
• V2I communication - This type of communication occurs among OBUs and RSUs when vehicles communicate with the infrastructure. This communication allows vehicles to reach other networks and can also be used in applications regarding security or data dissemination. Following we present typical applications that are interesting use cases which can improve traffic efficiency: (i) traffic jam notification, (ii) dynamic traffic light control and (iii) connected navigation [8]. • Hybrid communication - This type of communication, also known as V2X,
uses both V2V and V2I. The architecture allows network agents to reach longer ranges and opens a lot of possibilities to facilitate communication with distant nodes. The previous V2V and V2I use cases also fit V2X use cases.
• I2I communication - This communication type is used for fast communications between different nodes in the network. It can be used when (i) the city wants to deliver a message to a vehicle or to another city agent, (ii) the infrastructure is routing packages.
2.1.3 Radio Communication Standards
In this section, we will talk about WAVE, also known as Dedicated Short Range Communication (DSRC), how it has evolved over time and in which scenarios its
exploitation is useful. WAVE is a set of emerging standards for mobile wireless radio communications. As explained by Daniel Jiang et al. in [9], on October 1999 the United States FCC allocated 75 MHz of spectrum in the 5.9 GHz band to be used by Intelligent Transportation Systems (ITSs) Institute.
Figure 2.2: European standard of the VANET radio frequency spectrum [10] When compared with other technologies, some key characteristics make WAVE suitable to be used in vehicular environments. Contrasting with cellular, WAVE is a better choice given that
• The cost associated with the usage of cellular networks is still very high;
• The cost for developing WAVE technology is supposed to be supported by vehicle manufacturers independently of the existence of any cellular network providers, • Although the reach of cellular antennas is larger, its ground coverage is not evenly
distributed (rural areas are especially affected by this fact);
• VANETs using WAVE can efficiently solve this problem by extending the reach of the network;
• WAVE has significantly better latency results when compared to cellular networks. While the latency for WAVE is around 200µs, in cellular networks it can reach 3s [11].
Wi-Fi technology is not fit to be used in VANETs. Although its latency times are closer to WAVE’s, it is not appropriate to be used as a vehicular network technology because of (i) its connection process being very slow and (ii) its smaller range. Even when considering the disadvantages of using both Wi-Fi and cellular, these technologies should not be completely disregarded. In fact, a vehicle can connect to a Wi-Fi access point when moving at lower velocities or stopped, or even use the cellular infrastructure when no other options are available (although at slow rates). According to Daniel Jiang
et al. , WAVE can handle the challenges involving network node’s mobility and irregular
network connections presented by VANETs.
2.1.4 VANET characteristics
MANETs in general, and more specifically VANETs, have a special set of characteristics that should not be disregarded. Following, we will elaborate on some of the main
challenges of these networks.
• Volatility - The network nodes are vehicles in constant movement. In urban scenarios, these movements can be very inconstant, varying in velocity, trajectory, time of day, traffic and even weather conditions. Therefore, vehicles can be connected to the network for very brief periods.
• Mobility - As vehicles are in constant movement, connections can last only a few seconds, mostly due to velocity and unpredictable movements. Therefore network connections may break, and the network must adapt to these changes. The changes in topology may occur suddenly, and the network must be extremely dynamic and adapt to those changes.
• Network density - As in any other network, VANETs are influenced by the node density at a given time. Network agents must adapt to the local density in order to maintain a balanced network.
• Scalability - VANETs can become extremely large. Our world has over a billion vehicles and, in the future, they will be all connected. The network must be ready to address millions of nodes that will intermittently connect.
• Time Constraints - In VANETs some messages are time-sensitive - security messages and emergency messages. This means that messages should be dispatched efficiently, in order to avoid message delays. Such delays may cause message loss and, consequently, possible traffic accidents and/or security hazards.
2.2 Cryptography
Secure communications have been a concern for centuries. A lot of techniques and methods were invented, improved and applied to establish safe communications between two or more parties. The first appearance of applied cryptography was in 1500 BC where Mesopotamian scribes enciphered in a tablet the formula for making pottery glazes [12]. After this, a lot more examples of applied cryptography appeared. Ancient ones such as the Caesar Cypher, and more recent ones, for instance the Enigma machine. In the XX century, with the computing advances and the appearance of the Internet, this became a broadly discussed topic that focused on efficiently and securely exchanging messages between the involved agents. In this chapter, we will discuss some secure messaging techniques, what they aim to achieve, and why they are essential in the context of our work.
2.2.1 Asymmetric cryptography
Asymmetric cryptography, also known as public key cryptography, makes use of key pairs in order to provide for information encryption and digital signature functions. A key pair is composed by a public key and a private key. The private key allows the user
to sign or decrypt a piece of information. This key is never disclosed. The public key allows to validate a signature or to encrypt a piece of information. This key, as the name implies, can freely be disclosed.
A lot of protocols (HTTPS, SSH, OpenPGP, S/MIME, etc.) rely on public key cryptography for these two operations. The level of security provided is directly correlated with the chosen key size. However while increasing the key size augments the level of security provided, it also decreases the performance. As computing power increases, and more efficient algorithms are developed, the need for bigger sized keys arises [13]. In this section we will present and discuss some of the available public key cryptography solutions.
2.2.1.1 RSA
The RSA public key system [14] was one of the first asymmetric systems ever invented. Its novelty comes from the fact that two different keys, a private and a public, are used to cipher/decipher or cipher/decipher information.
In order to generate a key pair the following must be applied: 1. Generate a pair of large, random primes p and q;
2. Compute the modulus n as n = pq; 3. Calculate φ (n) = (p − 1, q − 1);
4. Select an integer e, such that 1 < e < φ (n) and e is coprime to φ (n) 5. Compute a private exponent d such that ed ≡ 1 ( mod φ (n))
6. The public key is composed by the pair (n, e) and the private key is composed by (p, q, d)(p and q are used in intermediate steps).
After creating the keys, to cypher a message m we use modular exponentiation as follows:
c = me mod n (2.1)
For deciphering a c we use modular logarithms, which is similar to the cyphering
process but instead of me we use cd:
m = cd mod n (2.2)
RSA is based on the difficulty of calculating p and q by factoring n.This problem is known as the "factoring problem" and is only as complex as the size of the integer numbers p and q.
In 1994, Shor elaborated on the capacity of quantum computers to factor a product of 2 prime numbers in polynomial time, therefore breaking RSA [15]. Shor showed that a quantum computer – if one could ever be created for the purpose – would be able to factor in polynomial time, therefore breaking RSA. In 2003, Shamir and Tromer came
up with a theoretical hardware device (TWIRL) that questioned the security of 1024 bit sized keys [16]. As a consequence of these works, the minimum size recommended for RSA keys is now 2048 bit long. In 2010, Thorsten Kleinjung et al. showed in [17] that it is possible to factor a 768 bits long (232 decimal digits) key in around fifteen hundred CPU years (two years of real time, on many hundreds of computers).
2.2.1.2 Elliptic-Curves
Elliptic Curve Cryptography (ECC) uses the complexity of calculating the discrete logarithm of points in elliptic curves defined over modular fields to archieve security. This technique, discovered by V. Miller and N. Koblitz [18][19], its considered very promising, especially when compared with RSA. Its key characteristics include low processing requirements, high efficiency levels, small memory consumptions and small key sizes when compared with RSA for the same security levels [20].
After the Edward Snowden scandal in 2013, some doubts emerged about ECC real security. After Snowden’s revelations, suspicions arose that the NSA had intentionally planted backdoors on a pseudo-random number generator based on elliptic curves. These suspicions were never confirmed.
Elliptic curves formula is described by the following equation:
y2+ axy + by = x3+ cx2+ dx + e (2.3)
The points belonging to these curves have only integer coordinates (discrete universe) and belong to the interval [0, q − 1] (modular universe with the module equal to q)
where q is either pk (with p being a prime number and k an integer) or 2m (with m
being a prime number).
These curves allow for two types of operations. The first one is the sum of two points:
C = A + B (2.4)
Calculating the sum of two points, represented in Equation 2.4, is the same as calculating the symmetric point (relatively to the x-axis) to the point resulting from the intersection of the curve with the line crossing the points A and B. The second operation is the duplication of a point:
C = 2A (2.5)
The duplication of a point is just the same as the sum of two points, depicted in 2.5, except that the straight line is tangent to A. Choosing a key pair depends on two things: having an elliptic curve - that follows the form of depicted in Equation 2.3 - and a generator point G that belongs to the curve. To create a valid key pair, we generate
a scaler d and compose a point P such that
P = d.G (2.6)
d is a private key, and P is its corresponding public key. Calculating P becomes
a matter of summing points that multiplicate themselves by powers of 2 (sum of consecutive duplications). For example if d = 20
dG = 24G + 22G = 2 (2 (2 (2G))) + 2 (2G) (2.7) A curve has multiple finite groups of points. The size of each group is defined by the smallest integer n that, when multiplied by a point of the group, generates its point on infinity.
n.P = O (2.8)
When using a specific elliptic curve is important to choose a generator point G that belongs to the group with the biggest n. With this in mind, the cofactor h evaluates the relation between the order of an elliptic curve, its total number of points #E, and n:
h = #E
n (2.9)
The number n defines the key dimension of an elliptic curve. The bigger the n, the smaller the h. The cryptographic community believes that to provide for a n bit security level the public key needs to have 2n bits.
One of the problems of using elliptic curves consists of defining the parameters for the curve, as well as choosing the right generator point G. Typically, curves are predefined, as well as its generator point. Taking this into consideration, there is a set of thoroughly studied and recommended curves:
• NIST proposed ten pseudo random curves. Five of the curves are P-192, P-224,
P-256, P-384 and P-521 and its h = 1. They follow the expression y2 = x3− 3x + b.
The other five, also known as the B series, are called B-163, B-233, B-283, B-409
and B-571. Its h = 2 and they follow the expression y2+ xy = x3+ x2+ b. In
both of the cases, b is the result of a SHA-1 digest over a given value. The curve’s name defines the size of its modulo (in bits).
• NIST also proposed five more curves, called the Koblitz curves: K-163, K-233,
K-283, K-409 and K-571. They follow the expression y2+ xy = x3+ ax2+ 1. The
value of a can be either 1 (h = 2) or 0 (h = 4). Similar to the example above the curve’s name defines its modulo size.
• Curve25519 was proposed by Daniel Bernstein and recommended by the IETF.
This curve has the expression y2 = x3 + 486662x2+ x and a modulus equal to
2255− 19. The order of the curve is bigger than 2252, and its cofactor is 8. The
popularity of this curve increased after Snowden’s revelations, given that it was proposed by an independent party. This curve has received a lot of attention from the cryptography community because of its records regarding efficiency and memory[21] [22].
2.3 Digital Signatures
Digital signatures are mathematical schemes that rely on public-key cryptography to perform authenticity verifications over messages or documents. There are three main applications of such a scheme:
• Authentication - Messages and documents often contain information regarding that content producer. Nonetheless, that information can be changed by a malicious third party. Digital signatures bound a message to its sender such that the recipient can be certain of the identity of the message producer.
• Integrity - Many scenarios require that the sender and the receiver assure that the message was not altered in the transmission process. Digital signatures guarantee this requirement. If a message is, for some reason, changed in the communication process, the signature will no longer be valid.
• Non-Repudiation - The non-repudiation property states that an entity that has signed a message or document cannot deny, later on, having signed it. Both non-repudiation and authentication properties rely on the secrecy of the private keys. With this in mind, compromised keys must be immediately revoked. Over time, researchers developed several relevant and widely acknowledged digital signature algorithms such as the Schnorr signature, the ElGamal signature scheme, Digital Signature Algorithm (DSA). Although these schemes pose as exciting approaches to the problem in hand, we will only detail two very novel approaches: Elliptic Curve Digital Signature Algorithm (ECDSA) and Edwards-curve Digital Signature Algorithm (EdDSA).
2.3.1 Elliptic Curve Digital Signature Algorithm - ECDSA
ECDSA is a method of performing digital signatures which uses ECC.
The first assumption of the ECDSA protocol is the definition of the curve parameters: (i) a curve, (ii) a generating point G and (iii) the integer order of the G point - n. In
Section 2.2.1.2 we described a set of curves. For testing purposes any of those can be used but real scenarios define Public Key Infrastructures (PKIs) (PKIs are described with detail in Section 2.3.4).
2.3.1.1 Signature Procedure
Let the sender possess a key pair consisting of a private key dA and a public key
curve point QA such that QA = dA . G When the sender wants to disclosed a signed
message m he performs the following steps:
1. Calculate e = H(m). H is a cryptographic hash function (described in detail in Section 2.3.5.1).
2. Let z be the Ln leftmost bits of e. Ln is the bit length of the group order n. z
can be greater then n but not longer.
3. Generate a cryptographically secure random integer k within the interval [1, n − 1] .
4. Calculate (x1, y1) = k . G. This operation is defined in Section 2.2.1.2.
5. Calculate r = x1 mod n. If r = 0 repeat the process starting in step 4.
6. Calculate s = k−1(z + rdA) mod n. If s = 0 repeat the process starting in step
4.
After performing the earlier steps, the sender can disclose the message m along with the signature pair (r, s).
2.3.1.2 Validation Procedure
In order for the recipient to authenticate the signature the first step is validate that
the public key point QA belongs to the curve. The recipient can perform this validation
by:
1. Checking that QA is not equal to the infinity point O, thus its coordinates are
valid.
2. Checking that QA is part of the curve.
3. Checking that n . QA= O.
This operation can be executed only once for each key pair. Moreover the recepient must:
1. Verify that r and s are within the interval range [1, n − 1]. The signature is invalid otherwise.
2. Calculate e = HASH (m). The hash functions must me the same that was used in the signing procedure.
3. As in the signing process, let z be the Ln leftmost bit
4. Calculate u1 = zs−1 mod n and u2 = rs−1 mod n.
5. Calculate the curve point (x1, y1) = u1 . G + u2 . QA and verify that (x1, y1) = O.
Finnally the signature is valid if r is equivelant to x1 mod n.
2.3.2 Edwards-curve Digital Signature Algorithm - EdDSA
EdDSA is a digital signature scheme that uses a variant of the Schnorr signatures based on Twisted Edwards curves. This scheme is designed to be quicker than other existing solutions without compromising security levels. EdDSA is a public domain scheme that was designed by a team including Daniel J. Bernstein the creator of Curve25519 -Niels Duif, Tanja Lange, Peter Schwabe, and Bo-Yin Yang.
Following we provide a simplistic description of the EdDSA scheme. Firstly this scheme requires the definition of several parameters:
• a finite field Fq over odd prime power q;
• an elliptic curve E over Fq. This curve must have #E (Fq) = 2cl, l is a large
prime and c = 2 or c = 3;
• a base point B ∈ E (Fq) and order l;
• a cryptographic hash function H with 2-bit outputs (assume 2b−1 > q therefore
allowing for curve points to be represented in strings of b bits); and
• A "prehash" function P H used to perform the signature over a reduced represen-tation of the message.
It is important that all of the nodes involved in the same EdDSA ecosystem use the same parameters. As for ECDSA in real scenarios these parameters are defined by PKIs (described with detail in Section 2.3.4). The signature security depends directly on the parameter choice.
The EdDSA signature of a message M under a private key k is the 2*b-bit string encoded R concatenated with the encoded S:
2cSB = 2cR + 2cH (R, A, M ) A (2.10)
The validate a signature pair of encoded R and S. Compute h =
EN C(R)||EN C(A)||M and check the group equation (2c× S) .B = 2c.R + (2c× h) .A exists in E. The validation fails if the group equation does not hold.
2.3.2.1 Ed25519
Ed25519 is a EdDSA signature scheme that uses Curve25519 along with SHA-512 as a hash function. To use Ed25519, parameters are set as follows:
• q = 2255− 19;
• E/Fq is −x2 + y2 = 1 − 121665121666x2y2 (this function is also known as the twisted
Edwards curve);
• l = 2252+ 27742317777372353535851937790883648493;
• B is the point in E (Fq) with y coordinate 4/5 and x is the correspondent positive coordinate (least significant bit is cleared); and
• H is SHA-512 with b = 256 • P H = x (identity function)
The above information is described in detail in [23].
2.3.3 Digital Certificate
In section 2.2.1 we described public-key cryptography, a widely known technology used to authenticate people, entities, and even internet servers.
The problem associated with the usage of asymmetric keys alone is a trust issue. In an open environment, such as the internet, there is no way of performing entity identification with just a public key. Therefore there is no way an internet user trusts that information was sent from the requested website. The internet is one of the many scenarios in which key pairs are required to be bounded to the entity owning them. This issue is solved with public-key certificates, also known as digital certificates.
Digital certificates are electronic documents with a preset structure that carry (among other things) (i) a public key, (ii) information about its owner (iii) and a digital signature of the certificate.. The entity issuing the certificate provides the digital signature. Such entities are known as Certificate Authoritys (CAs).
Digital certificates have a limited validity period. There are two ways a certificate can expire:
• Each certificate possesses an expiration date. Any signature operation performed by the public key after the expiration date should be disregarded.
• A revocation certificate. Revocation certificates are special types of certificates claiming that, after a certain date, a given certificate is no longer valid. Usually, revocation certificates are issued by the same entity that issued the certificate. A certificate is valid if it is used within its validity period, if when used it has not been revoked and if it signature its valid. This last requirement forces the entity validating a signature to possess the public key of the issuer of the certificate. This way it is normal that, in order to validate a certificate, the validating entity must obtain the public key certificate of the issuing entity. Furthermore, this process must be performed once again to validate the issuing entity - therefore creating a chain.
The chains only end when the validating entity reaches a root certificate, as depicted in Figure 2.3. A root certificate is a certificate signed by the same key it ensures. These are also known as self-certifying certificates. This way to validate a certificate, the hole certification chain must be validated.
Root CA CA CA End Entity End Entity End Entity End Entity
Figure 2.3: Certification Chains
2.3.4 Public key infrastructure
In Section 2.3.3 we have clarified concepts such as digital certificates, certification au-thorities and certificate chains. Different digital ecosystems rely on different certification models, different digital certificate structures and even different key pair distribution. A PKI is a set of policies, procedures, hardware and software that define an aggregation of CAs in a determined context. A PKI is responsible for:
• Defining policies for the creation of asymmetric key pairs attributed to people or services.
• Defining policies of issuance of digital certificates.
• Defining policies for the issuance of revocation certificates. • Defining CAs.
• Providing public distribution of the issued certificates. • Providing public distribution of the revoked certificates.
There are two methods, included in the PKI structure, that allow the issuing entities to publicly disclose a list of the revoked certificates: Certificate Revocation Lists (CRLs) and Online Certificate Status Protocols (OCSPs).
2.3.4.1 Certificate Revocation Lists - CRLs
A CRL is a list of revoked certificates that is publicly disclosed by a PKI. This list contains all the certificates that were both revoked and have not expired yet. For each revocation certificate this list contains (i) details about the certificate, (ii) the revocation reason, (iii) the revocation date. To assure the validity of the CRL, it contains a release date and it is signed by the releasing entity. Moreover, each CRL is issued periodically by an issuing entity and contains the next release date, to allow for controled periodical list updates.
Each revocation certificate contains a revoke reason. Depending on the used certifi-cate standard the reasons can be various:
• Unspecified reason;
• Compromised private key;
• Compromised issuer CA private key;
• Superseded certificate. A replacement certificate has been issued to the entity; • Affiliation changed. The entity has terminated its relationship with the
organiza-tion;
• Entity loss of privilege.
CRLs can become really large files. Moreover, given their size, the lookup can become a problem. With this in mind OCSPs can become a useful protocol to certificate validators.
2.3.4.2 Online Certificate Status Protocol - OCSPs
OCSP is a simple question/answer protocol. In this protocol an OCSP Responder is questioned about the existence of a revocation certificate for a given existent certificate. This question carries a serial number that identifies the certificate. The Responder’s response should be a simple yes or no, furthermore this response must be signed by the CA to assure authentication.
To let the questioning entity know which responder to ask, usually, each certificate contains details about the URL of the Responder.
Typically it is faster to use OCSP compared to CRL lookups, yet it is not guaranteed that the user has internet access. With this in mind the two methods should be combined.
2.3.5 Symmetric cryptography
Asymmetric cryptography enables non-repudiation, digital signatures and confidentiality. On the other side, symmetric cryptography allows for integrity checks, limited source authentication, and encryption. Although some of these properties could also be achieved with asymmetric cryptography, symmetric cryptography is much more efficient. For example, an optimized ECC algorithm performs 100 to 1000 times more slowly than a symmetric cypher such as the Advanced Encryption Standard (AES) algorithm [24]. In this section, we will elaborate on a set of important cryptographic functions that can be used to achieve different cryptographic properties.
2.3.5.1 Cryptographic Hash Functions (and digest functions)
A general hash function is a function that has the capability of mapping an arbitrary amount of data into a fixed-size value. Generally, hash functions are used to index data
(a) Collision resistance (b) Pre-image resis-tance
(c) 2nd pre-image resis-tance
Figure 2.4: Graphical representation of three critical characteristics of hash functions [25]
in hash maps, therefore expediting search complexity. Cryptographic hash functions,
are more specific. The ideal1 cryptographic hash function (H) would have the following
properties, also depicted in 2.4:
• Deterministic - given a message input, the output should be the same no matter the number of times the function runs for that input.
• Quick - for all the inputs, the output should be computed quickly.
• Pre-image resistant - given an output, it should be difficult to calculate the input that generated it.
• Collision-resistant - it should be infeasible to find two inputs i1 and i2 such
that i1 6= i2 and H(i1) = H(i2)
• 2nd pre-image resistant - given an input i1 and its output o1, it should be
infeasible to find an i2 which is both i1 6= i2 and H(i2) = o1.
• Uncorrelatability (confusion) - the input and its output should be largely uncorrelated.
Although finding a close-to-ideal cryptographic hash function is hard, the closer the hash function is to have the above characteristics, the better it is. In this section, we will elaborate on a few examples of cryptographic hash functions, as well as exploits and attacks that were discovered and performed on them.
2.3.5.2 MD5
The MD5 (Message-Digest algorithm 5) is a widely used cryptographic hash function developed by RSA Data Security, Inc. MD5 was designed in 1991 by Ronald Rivest as a successor for MD4 which, at the time, had been proved to have security issues. MD5 produces an output of 128 bits. The input, after padding, is divided into blocks of 512 bits.
1It would be ideal that each hashed value got a different output. However, that is not possible because, in most cases, the number of possible inputs of an hash function (domain) is much higher than the number of outputs (codomain). Moreover, although it is not possible to avoid collisions, it is the hash function’s job to make that discovery hard.
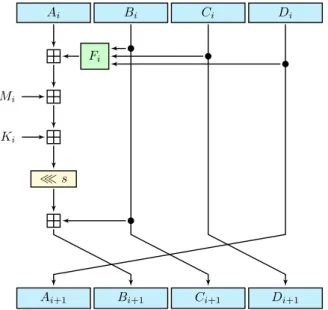
MD5’s main algorithm iterates over all the 512-bit chunks. Its main algorithm maintains and operates over a 128-bit state divided into four 32-bit words (A, B, C, D). The message processing consists of four stages of 16 operations (a non-linear function F, modular addition, and left rotation).
Ai Bi Ci Di
≪ s Fi
Ai+1 Bi+1 Ci+1 Di+1
Mi
Ki
Figure 2.5: MD5 Compression Function
Over the years, researchers discovered several issues involving MD5’s collision resistance: In 2005, Xiaoyun Wang et al. wrote one of the first papers on how to break cryptographic hash functions such as MD4, HAVAL-128, RIPEMD, SHA-0 and MD5. Its main focus was on MD5, given its visibility around the cryptography community and how a hacker could break some of the MD5 applications in a matter of
hours [26][27][28]. Xiaoyun Wang claims that the complexity of finding a pair (M0, M00)
such that H (M0) = H (M00) does not exceeds the time of running 239 MD5 operations.
In 2008, Alexander Sotirov et al. [29] presented a vulnerability in the internet’s PKI used to issue digital certificates for secure websites. As proof of concept, they were able to create a fraudulent Certificate Authority capable of impersonating any website. This bogus CA was considered valid by most Web browsers.
It is important to emphasize that MD5 maintains pre-image resistant. The works discussed above are either collision attacks or 2nd pre-image attacks. It remains
unfeasible to discover i1 given H(i1).
2.3.5.3 SHA-1
The Secure Hash Algorithm 1 (SHA-1) was created by the US National Security Agency (NSA) in 1995, after the SHA-0 algorithm in 1993, and it is part of the Digital Signature Algorithm or the Digital Signature Standard (DSS). SHA-1 produces a 160-bit
output, and internally it runs 20 rounds of 4 different operations. Since its invention, several authors presented papers elaborating on SHA-1’s collision resistance. Most of the work developed has been either theoretical approaches or a partial crack of the eighty rounds of SHA-1 [30][31]. In 2017 Google researchers announced a practical collision attack over SHA-1. The proof of concept relied on two different PDF archives that produced the same hash digest.
Ai Bi Ci Di Ei ≪ 5 ≪ 30 Fi Ei+1 Di+1 Ci+1 Bi+1 Ai+1 Wi Ki
Figure 2.6: SHA-1 Compression Function
2.3.5.4 SHA-2
SHA-2 is a family of cryptographic hash functions designed by the NSA. SHA-2 presents significative changes when compared with its predecessor, SHA-1, one of which is the fact of being a family of functions, 6 in total: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256. SHA-256 and SHA-512 are new hash functions computed with 32-bit and 64-bit words, respectively. SHA-224 and SHA-384 are truncated versions of SHA-256 and SHA-512, respectively, computed with different initial values. SHA-512/224 and SHA-512/256 are also truncated versions of SHA-512, but with different initial values.
Ai Bi Ci Di Ei Fi Gi Hi If Σ1 M aj Σ0 Hi+1 Gi+1 Fi+1 Ei+1 Di+1 Ci+1 Bi+1 Ai+1 Wt Kt
Figure 2.7: SHA-2 Compression Function
SHA-256 and 57 rounds of SHA-512, and collision resistance for 46 rounds of SHA-SHA-256 [32][33]. No collisions were yet discovered for SHA-2, unlike for MD5 and SHA-1.
3
Related Work
3.1 VANET message authentication protocols
As we explained earlier in section 2.1.4 vehicular networks have a very particular set of characteristics like volatility, scalability, time constraints, mobility and network density. These characteristics compel researchers to find security schemes that implement the network security requirements while increasing efficiency. In this section, we will present a set of VANET authentication systems that implement different technologies in order to reach specific goals like non-repudiation, trace-ability, low computational overhead, low communication overhead and others.
3.2 Security requirements
In previous works developed by the cryptographic community there are several ap-proaches that aim to solve different security requirements. Each solution is an approach to a different scenario. Thus it is normal that different approaches adopt different methodologies and, therefore, present different results. Some of the approaches read in the literature aim to solve the following security requirements:
• Privacy Preservation - The protocol does not disclose details about the involved nodes;
• Entity Authentication - The protocol verifies the legitimacy of the sender; • Message Authentication - The protocol validates the message consistency and
integrity.
• Non-repudiation - The protocol does no allow the sender to deny that he transmitted a message.
• Low Computation Overhead - The protocol ensures that the communication cost is reduced (number of packets, number of bytes per packet).
• Low Communication Overhead - The protocol ensures that the computational costs are reduced (processing power, hardware costs, etc.).
• Traceability - The protocol allows for inside attackers to be identified and tracked.
• Unlinkability - The protocol inhibits possible attackers of identifying if different messages come from the same sender.
We aim for a solution that focuses mainly on entity and message authentication, that provides for non-repudiation and low overheads. With this in mind, we discarded traceability and unlinkability and privacy concerns.
For instance in [34], [35], [36], [37] and [38] researchers propose Group Signature (GS) schemes, indicated for VANET scenarios. The main characteristic of a GS based scheme is that any member of a group signs a safety message with its private key. The receiver of the message uses the group public key to validate the authenticity of the message. In this process, the identity of the sender is only revealed to the group manager. Moreover, GS also grants non-traceability - it is not possible to correlate two signed messages to realise whether or not the message sender is the same. Given that each group has only one public key, the GS scheme also allows for scalability. Although important properties like scalability, unlinkability and unforgeability are achieved, the usage of group signatures leads to computational overhead throughout signature validation. This overhead influences the system’s performance and, consequently, it can lead to message losses. Given that these schemes focus mostly on privacy preservation mechanisms, and that is not the main focus of our work, we will not discuss these systems in detail.
3.2.1 Message Authentication Code based authentication schemes
In cryptography, Message Authentication Code (MAC) is a short piece of information, also known as a tag, used to authenticate a message. MAC algorithms take two arguments: a message and a secret key. MAC algorithms are particularly useful as they allow key owners to confirm both data integrity and data authenticity.
Usually, these protocols are very simplistic:
1. The sender calculates the MAC using the message he wants to send and the secret key.
2. The sender broadcasts the message.
3. The recipient validates the key by comparing the received MAC with a MAC calculated by himself (using the received message and the secret key).
If the message somehow changes in the communication process (either by a malicious node or because of an external error) the recipient can identify the error occurred and, consequently, discard the message. These algorithms often assume that the
key is previously agreed/shared between the intervenients before the authenticated communication process starts. Moreover, they do not provide for non-repudiation given that if, for some reason, the key is compromised, anyone who holds the key can both verify and generate hash messages.
In [39] Lin et al. introduced an authentication scheme based on MACs that presents privacy preservation properties. This scheme combines the use of a MAC algorithm and a hash chain element to calculate MAC tags. It reduces the computational overhead by minimizing the usage of asymmetric message signing and asymmetric message validation. This scheme also minimized bandwidth usage when compared with other PKI schemes given that the MAC tag is smaller than asymmetric produced signatures.
Zhang et al. in [40] proposed an authentication scheme known as Roadside Unit Aided Message Authentication Scheme (RAISE). This scheme establishes a shared key between each vehicle and the nearest RSU. Whenever the sender vehicle wants to send a safety message, he broadcasts it to other vehicles. The RSU is responsible for verifying the authenticity of the message and communicate the result to the vehicles. By introducing MACs, RAISE aims to reduce both communication and communication overheads.
While lightweight approaches, the above solutions have no particular concern with the possibility of important lost messages.
3.2.2 Hash Function based authentication schemes
As explained in 2.3.5.1, hash functions are used mainly for integrity checks and not message encryption. The hash function takes a message as input and produces a fixed-size string, called the hash value. The usage of methods based on hash functions allows the authentication process to be executed very efficiently.
A simple scheme is to hash a message and append the hash value to it. However, this scheme does not provide full authentication nor non-repudiation, given that an attacker may edit the message and update the hash value, and produce a completely new message.
In [41], Chuang et al. introduced Trust-Extended Authentication Mechanism
(TEAM). TEAM is a decentralized alternative that uses a pre-shared key in the authentication process. This scheme is particularly lightweight given that it relies only on XOR operations and hash-functions. This scheme involves eight procedures: initial registration, login, general authentication, password change, trust-extended au-thentication, key update, key revocation, and secure communication. Before a vehicle can join a VANET, its OBU must register with an authentication server to perform a key agreement. When a vehicle wants to access a service, it has to perform the login procedure. Next, the OBU checks the authentication state itself (i.e., the lifetime of the
key). If the lifetime of the key is reduced to zero, the vehicle is considered mistrustful. The vehicle performs a trust-extended authentication procedure. The trustful vehicles assist other vehicles in performing the authentication procedure, communicate with other trustful vehicles (i.e., secure communication procedure) or to access the Internet. If the key is bellow a given threshold, the vehicle performs a key update procedure. TEAM minimizes the usage of asymmetric keys in order to establish a single multi-usage symmetric key.
In [42] and [43] recearchers present schemes that make use of hash functions to achieve special security requirements such as privacy, unlinkability and untraceability. As for previous schemes theses requirements are not the focus os our work. For this reason we will not describe them in detail.
Hash function schemes provide a lightweight solution that fit under the VANET particular needs. Nonetheless most of the existing schemes have no concern for lost messages (a common scenario in vehicular networks). With this in mind they are not fit for emergency messages scenarios. In the following sections we will describe scenarios that take these concerns into account, and that we found to be particularly interesting in VANET scenarios.
3.3 Guy Fawkes protocol
The Guy Fawkes protocol [44] by Anderson et al. is a secure communication algorithm based on hash functions and message chaining mechanisms. As the name of the algorithm points out, their authors came up with it while discussing how a modern Guy Fawkes would send messages, to advertise his cause. Their main concern was to develop an algorithm that allowed Guy Fawkes to disclose authenticated messages
without getting caught. 1.
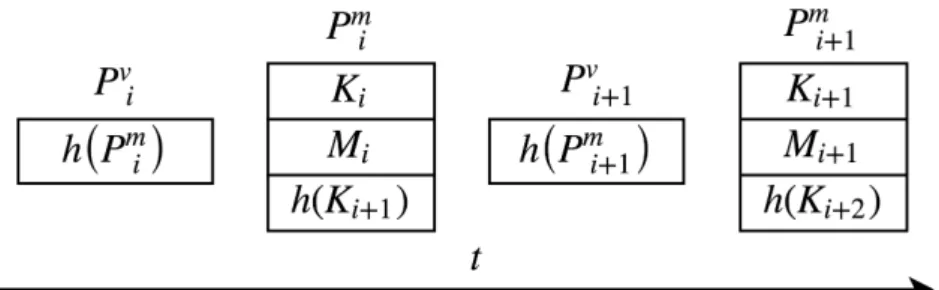
The protocol works by chaining messages, i.e. including the hash of a nonce in the
i-th message and in message i + 1 revealing that nonce. In Figure 3.1 we depict the Guy
Fawkes protocol execution over time. Next, to better explain the algorithm’s execution, we present in detail the protocol’s behaviour:
1. Select a random word Ki+1
2. Form its hash h (Ki+1)
3. Build a message Pm
i = (Ki||Mi||h (Ki+1)), where Mi represents the message
number i of a chain of n messages.
4. Form it’s hash Pv
i = h (Pim) and publish it.
5. Reveal the message Pim.
1Guy Fawkes is know to have been member of a group of provincial English Catholics responsible for the failed Gunpowder Plot of 1605 [45].
Figure 3.1: Sequence of packages in the Guy Fawkes protocol. Pm
i and Pi+1m are messages and Piv and Pi+1v are message’s hashes (validations);
The Guy Fawkes protocol is straightforward, yet the chain alone does not provide enough security. The non-repudiation criterion is only accomplished if the first message source can be proved to be from the supposed sender. Without this constraint, the receiver has no certainty about the source of the message, and therefore the whole chain cannot be trusted. With this in mind, the bootstrap of the protocol must use a digital signature protocol that authenticates the message chain source. Only the first message requires signing so that the whole chain is trustworthy. We commonly refer to this message as an Anchor message. The methods referred in 2.2.1 are possible examples to be used in Anchor messages.
Another issue of this protocol presents itself when we consider its usage in unreliable networks. The unpredictability of these networks poses a severe challenge to the Guy Fawkes protocol since if a single package is lost, the whole chain must be reset. A work around to this issue would be to send an Anchor message periodically. This way nodes that lost messages and new nodes would be able to reestablish the message chain.
Morevover, and although this protocol presents security features that can lead to authenticated communications, under specific circumstances, it is vulnerable to MitM attacks. In fact, if an attacker is able to deploy a physical barrier to packet broadcasting (e.g. by intercepting the wiring of the antenna of the broadcasting device), it can perform
the following attack:
1. block the broadcast of genuine packets from Pim onward;
2. wait until receiving both Pv
i+1 and Pi+1m ;
3. Change Mi+1 in Pi+1m to Fi+1 (fake message) and recompute Pi+1v accordingly;
4. broadcast the tampered packets Pv
i+1 and Pi+1m and repeat the process in the
following packets.
Clock synchronization and fixed reception windows can avoid this problem, but they impose a fixed transmission rate that increases the medium occupancy. The use of clock synchronization algorithms is introduced in 3.4 by the Timed Efficient Stream Loss-tolerant Authentication) (TESLA) protocol [46].
![Figure 2.1: VANET communication types[6]](https://thumb-eu.123doks.com/thumbv2/123dok_br/15751982.1073770/29.892.210.705.125.371/figure-vanet-communication-types.webp)
![Figure 2.4: Graphical representation of three critical characteristics of hash functions [25]](https://thumb-eu.123doks.com/thumbv2/123dok_br/15751982.1073770/41.892.133.788.114.322/figure-graphical-representation-critical-characteristics-hash-functions.webp)